Filters Options for Findings¶
To find specific findings that are relevant to you, go to the Findings page and use the filters. Simply click on the upside-down triangle near the screen's top-left corner.
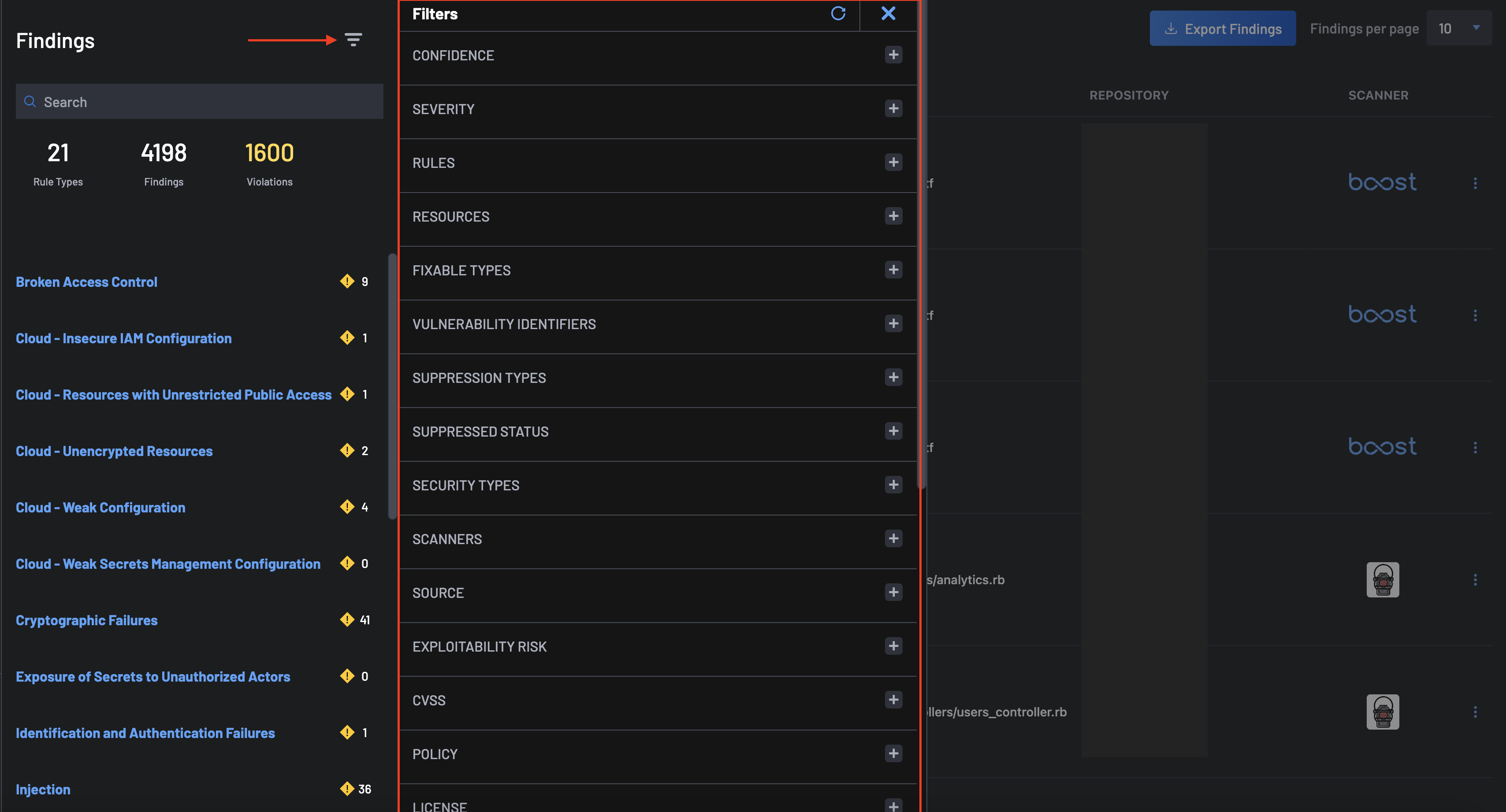
Here are the explanations for each filter:
Types of Filters¶
- Event Type: Findings can be categorized as a Violation or a Security event, with the latter being a subset of Findings that may indicate a potential breach. These events require manual review to ensure no malicious activity has occurred. The "Acknowledgement Status" is associated with the Security option to track acknowledgment of such events.
- Acknowledgment Status: This distinguishes the results for Security event findings that require a manual review as to have either been Acknowledged and/or are still Pending acknowledgment.
- Confidence: Filter Findings by confidence level: "High", "Medium", "Low", or "Not Set" for findings generated by scanners that do not populate this field.
- Severity: Separates higher-priority Critical risks from lower-priority Warnings.
- Rules: Select specific scanner rules for targeted security checks.
- Resources: Focus on findings for a specific resource (project) or a group of resources.
- Finding Types: Filter results by Violations or Findings. A Violation is a Finding that violates a Policy.
- Fixable Types: Focus on Fixable and Not Fixable security issues, making it easier to solve known vulnerabilities.
- Vulnerability Identifiers: The Common Vulnerabilities and Exposures Identifier (CVE ID) of the vulnerable libraries (SCA) to focus upon.
- Suppression Types: If "Suppressed Status" includes "Suppressed", this will offer additional filters which includes:
- Source Ignore: A finding that is "Suppressed in Code".
- Won't Fix: A true positive you've chosen not to rectify due to certain circumstances.
- False positive: An alert about a security concern that is not present.
- Suppressed Status: Filter Findings by their state: Not Suppressed (the default state) or Suppressed.
- Security Types: Categorize security Findings by CI/CD, Source Code, or SCA for easier organization.
- Scanners: Filter for findings by the scanner that found them.
- Source: Filter findings by the file in which they are found. The lists of said files are grouped by the security type, SAST for custom code, and SCA for libraries.
- Exploitability Risk: Exploit Prediction Scoring System (EPSS) predicts the likelihood of a CVE being attacked within the next 30 days.
- CVSS: The Common Vulnerability Scoring System (CVSS) gives a higher number to more dangerous security vulnerabilities found in commonly used libraries. Scores range from 0 to 10.
- Licenses: Filter for findings related to disallowed licenses. Select one or multiple licenses to retrieve results.