Enabling SBOM Content Retrieval for a Container Image in AWS ECR¶
This guide explains how to set up SBOM (Software Bill of Materials) content retrieval for a container image in AWS ECR (Elastic Container Registry) via BoostSecurity integration. Follow these steps to enable SBOM content retrieval for a container image in AWS ECR:
- Navigate to the Integrations page.
-
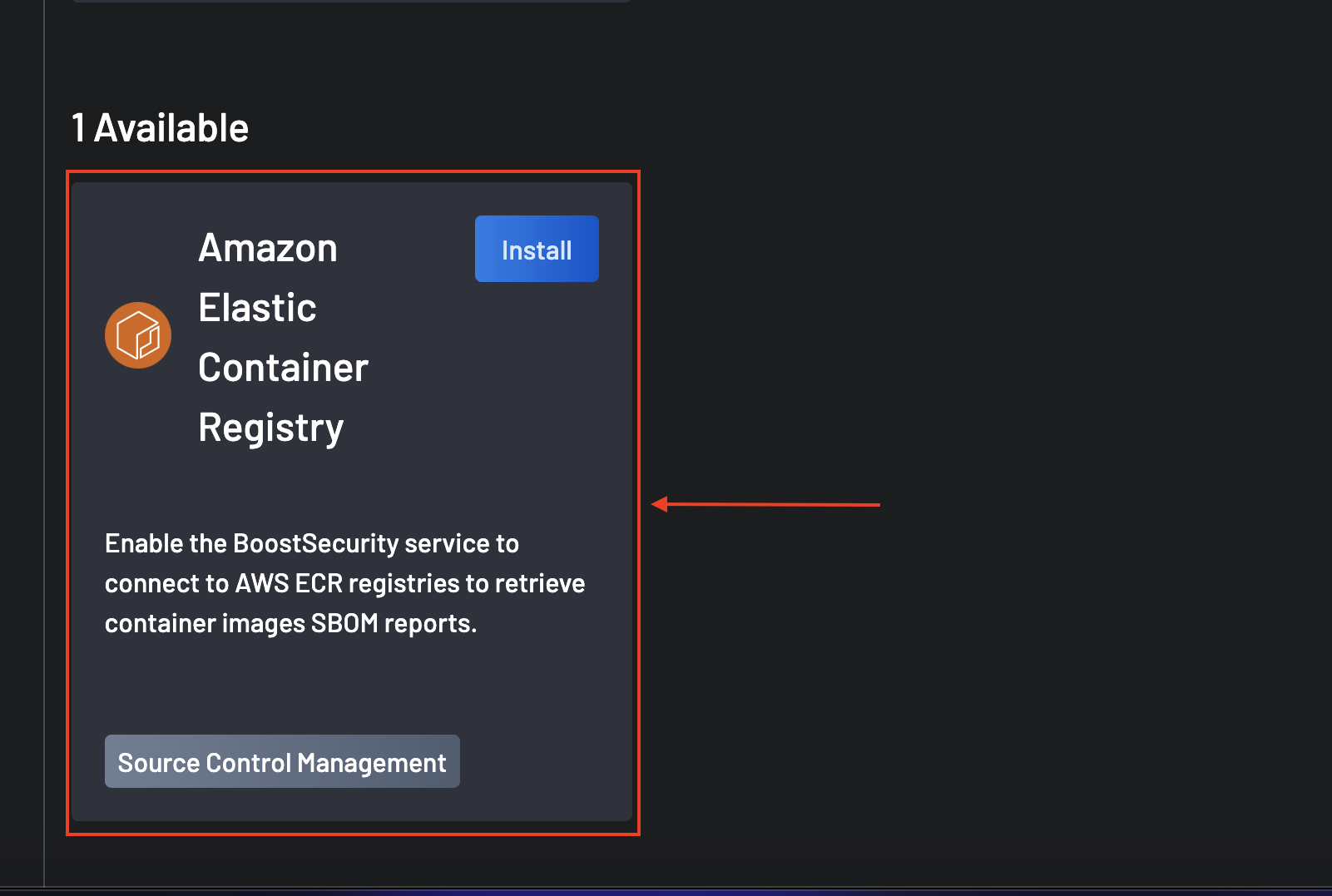
Scroll to the
Availablesection and select Amazon Elastic Container Registry. -
Click on the Install button.
-
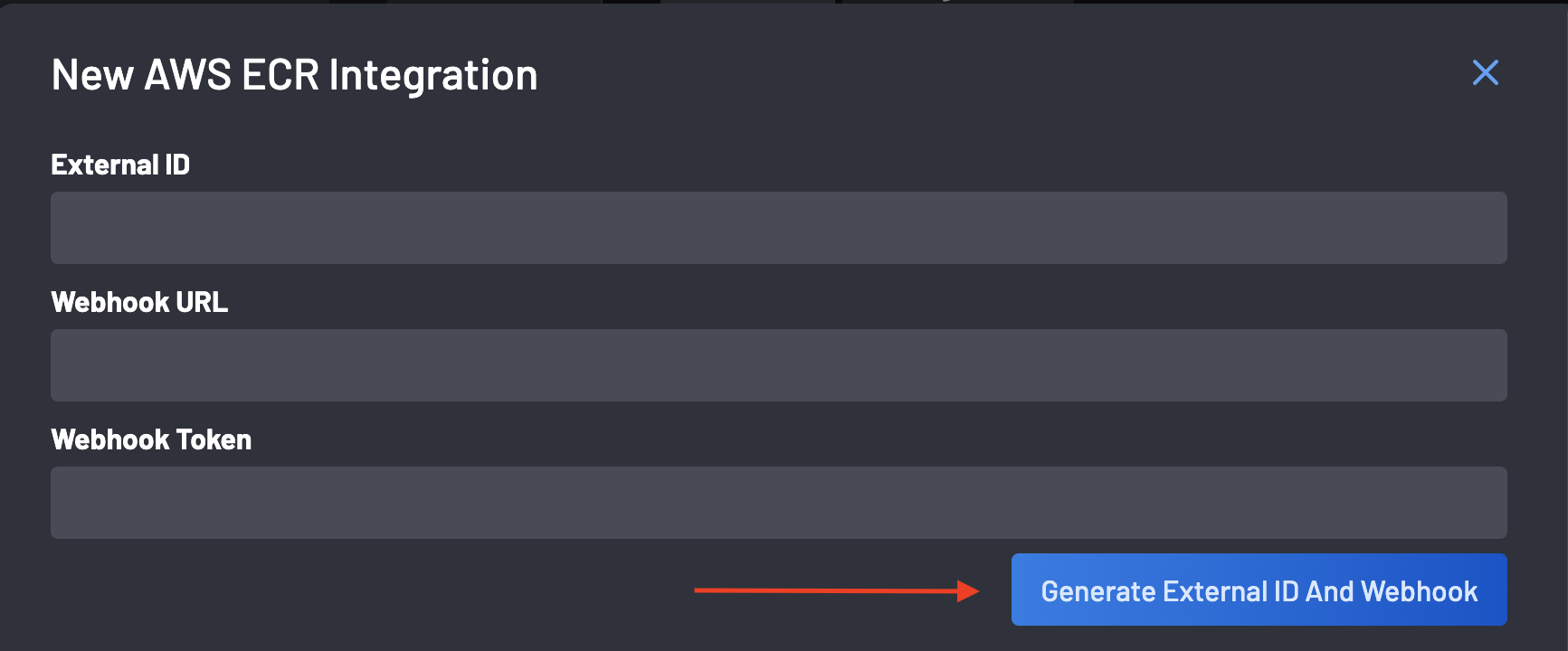
Click the Generate External ID and Webhook button to receive a randomly generated External ID and Webhook URL and Token.
-
Create an EventBridge rule for the webhook
{ "source": ["aws.ecr"], "detail-type": ["ECR Image Action"], "detail": { "action-type": ["PUSH"], "result": ["SUCCESS"] } }- Set the target of the rule to be an EventBridge API destination.
- Set the API destination endpoint to the
webhook_urlwith POST as the http method. - The authorization type for the connection is an API key where the key and value are
API key name = ApiKeyandValue = webhook_secret.
-
Ensure a proper setup of your IAM role with the provided External ID. Here are the required settings:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "209299908473" }, "Action": "sts:AssumeRole", "Condition": { "StringEquals": { "sts:ExternalId": "externalIdProvidedByBoost" } } } ] } -
Go to your AWS account and create the necessary resources with appropriate permissions.
- Inspector permissions: Refer to Inspector Permissions
- Getting SBOM reports
- Your IAM Role Policy Policy must include these permissions:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "s3:GetObject", "s3:ListBucket", "s3:GetBucketLocation", ], "Resource": [ "arn:aws:s3:::s3-bucket-name", "arn:aws:s3:::s3-bucket-name/*" ] }, { "Effect": "Allow", "Action": [ "ecr:DescribeRepositories", "ecr:ListImages", "ecr:DescribeRegistry", "ecr:DescribeImageScanFindings", "ecr:BatchGetRepositoryScanningConfiguration", "ecr:DescribeImages" ], "Resource": "*" }, { "Effect": "Allow", "Action": [ "inspector2:CreateSbomExport", "inspector2:GetSbomExport" ], "Resource": "*" }, { "Action": [ "kms:Decrypt" ], "Resource": "arn:aws:kms:*:number-of-the-account:key/rest-of-the-info" } ] }Note: The created S3 bucket must be in the same region as the scanned ECR repository.
-
S3 Bucket Policies (1 per region): The S3 bucket should be in the same region as the ECR repository and have this policy applied to it:
{ "Version": "2012-10-17", "Statement": [ { "Sid": "allow-inspector", "Effect": "Allow", "Principal": { "Service": "inspector2.amazonaws.com" }, "Action": [ "s3:PutObject", "s3:PutObjectAcl", "s3:AbortMultipartUpload" ], "Resource": "arn:aws:s3:::s3-bucket-name/*", "Condition": { "StringEquals": { "aws:SourceAccount": "number-of-the-account" } } } ] } -
You need one KMS key per S3 bucket region to use SBOM on ECR repos in different regions, use KMS cross-region replication to accomplish this task:
{ "Sid": "Allow Amazon Inspector to use the key", "Effect": "Allow", "Principal": { "Service": "inspector2.amazonaws.com" }, "Action": [ "kms:Decrypt", "kms:GenerateDataKey*" ], "Resource": "*", "Condition": { "StringEquals": { "aws:SourceAccount": "number-of-the-account" } } } -
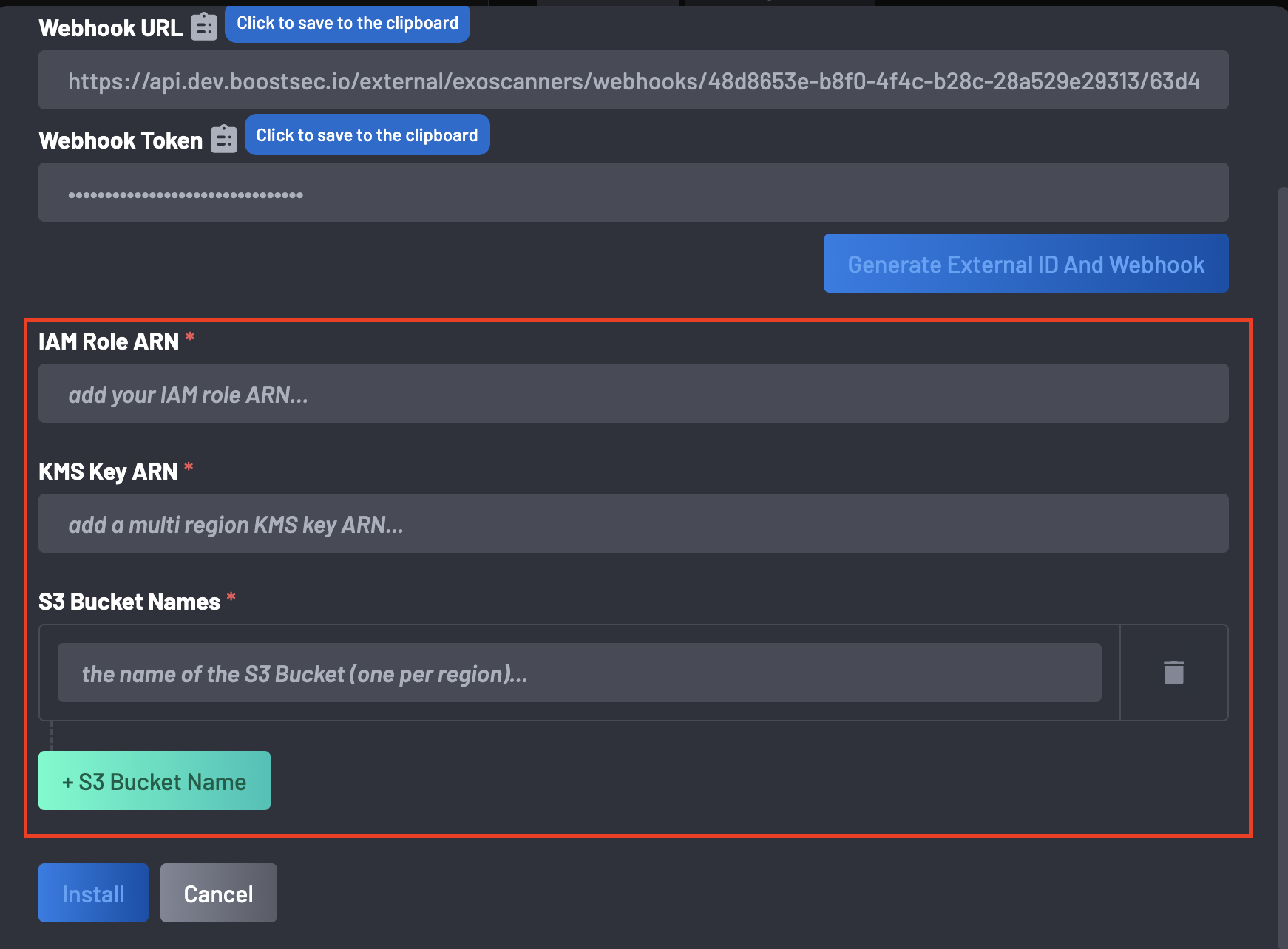
Return to BoostSecurity and provide the following information during installation:
- IAM Role ARN
- KMS Key ARN
- S3 Bucket Names: Add bucket names using the + S3 Bucket Name button. Use the delete button to remove or replace bucket names.
- Click on Install and the integration is ready.