Software Bill Of Materials (SBOM)¶
BoostSecurity enables collecting the nested inventory of all open-source and third-party components in your project codebase.
Collecting the projects' SBOMs is as simple as configuring the BoostSecurity SBOM scanning module to the projects' workflows, and the inventories are generated at every commit on the projects' default branches.
In addition to reporting the inventories of components, BoostSecurity also reports on the known security vulnerabilities for these components.
Getting Started¶
The first step in enabling SBOM generation for your project is to configure the SBOM scanner. The SBOM scanner runs whenever a commit is made on the default branch and collects the components' inventory.
Note: Even if the workflow is configured to run the SBOM scanner on pull requests, the scanner does not collect the inventory of components on pull requests.
Two versions of SBOM scanners are available to generate the SBOM inventory, whether the inventory is generated from the source code repository or from the generated container image artifact.
Note: There can only be one scanner that outputs SBOM per project.
SBOM Scanner Module from Source Code¶
To add the SBOM scanner to the workflow to collect the inventory from the source code, add a workflow yaml file with the following configuration:
GitHub Actions
```yml
name: BoostSecurity
on:
workflow_dispatch:
push:
branches:
- main
- master
jobs:
boost-sbom:
name: SBOM
if: github.event_name != 'pull_request'
runs-on: ubuntu-latest
steps:
- name: Checkout
uses: actions/checkout@v2
- name: Upload SBOM
-
uses: boostsecurityio/boostsec-scanner-github@v4
with:
registry_module: boostsecurityio/trivy-sbom
api_token: ${{ secrets.BOOST_API_TOKEN }}
```
On the next commit, the BoostSecurity SBOM scanner will collect the components inventory.
SBOM Scanner module for Container Images¶
Components inventories can also be generated from container images. When generating the SBOM from container images, operating systems packages, as well as other components pulled from dependencies, can be reported.
To add the SBOM scanner to the workflow to collect the inventory from the container images, add the BoostSecurity scanner module in the workflow after the image generation step. For example:
GitHub Actions
```yml
on:
workflow_dispatch:
push:
branches:
- main
jobs:
boost-image-sbom:
name: Boost Container
runs-on: ubuntu-latest
steps:
- name: Checkout
uses: actions/checkout@v3
### In this step here you would build
### your container image
### the step here is just an example
- name: Build Image example
run: docker build . -t <your image name>
- name: Run Boot Trivy SBOM for Image
uses: boostsecurityio/boostsec-scanner-github@v4
env:
BOOST_IMAGE_NAME: <your image name>
with:
registry_module: boostsecurityio/trivy-sbom-image
api_token: ${{ secrets.BOOST_API_TOKEN }}
```
SBOM for Multiple Container Images Per Repository¶
As described above, the image inventory is associated with the project when configuring the workflow to scan container images. But in some cases, a repository might produce multiple container images, for example, in the case of a mono repository.
In that case, the scanner module can be configured to associate a label to the SBOM inventory produced for each individual container image.
When doing so, the SBOM service tracks and reports the inventory for each image. An example of workflow configuration is as follows:
GitHub Actions
```yml
on:
workflow_dispatch:
push:
branches:
- main
jobs:
boost-image-sbom:
name: Boost Container
runs-on: ubuntu-latest
steps:
- name: Checkout
uses: actions/checkout@v3
### In this step here, you would build
### your container image
### the step here is just an example
- name: Build first Image example
run: .... image building for first image .....
- name: Run Boot Trivy SBOM for Image - asset 1
uses: boostsecurityio/boostsec-scanner-github@v4
env:
BOOST_IMAGE_NAME: <your first image name>
with:
api_token: ${{ secrets.BOOST_API_TOKEN }}
registry_module: boostsecurityio/trivy-sbom-image
scan_label: <first image label>
- name: Build second Image example
run: .... image building for second image .....
- name: Run Boot Trivy SBOM for Image - asset 2
uses: boostsecurityio/boostsec-scanner-github@v4
env:
BOOST_IMAGE_NAME: <your second image name>
with:
api_token: ${{ secrets.BOOST_API_TOKEN }}
registry_module: boostsecurityio/trivy-sbom-image
scan_label: <second image label>
```
The additional argument scan_label sets the label for the SBOM inventory on the specific asset. In the SBOM service projects list view, the project name for that asset's inventory is <organization>/<repository>/<label>. Labels can be used for mono repositories generating multiple container images to generate SBOM inventories for each container images in the repository.
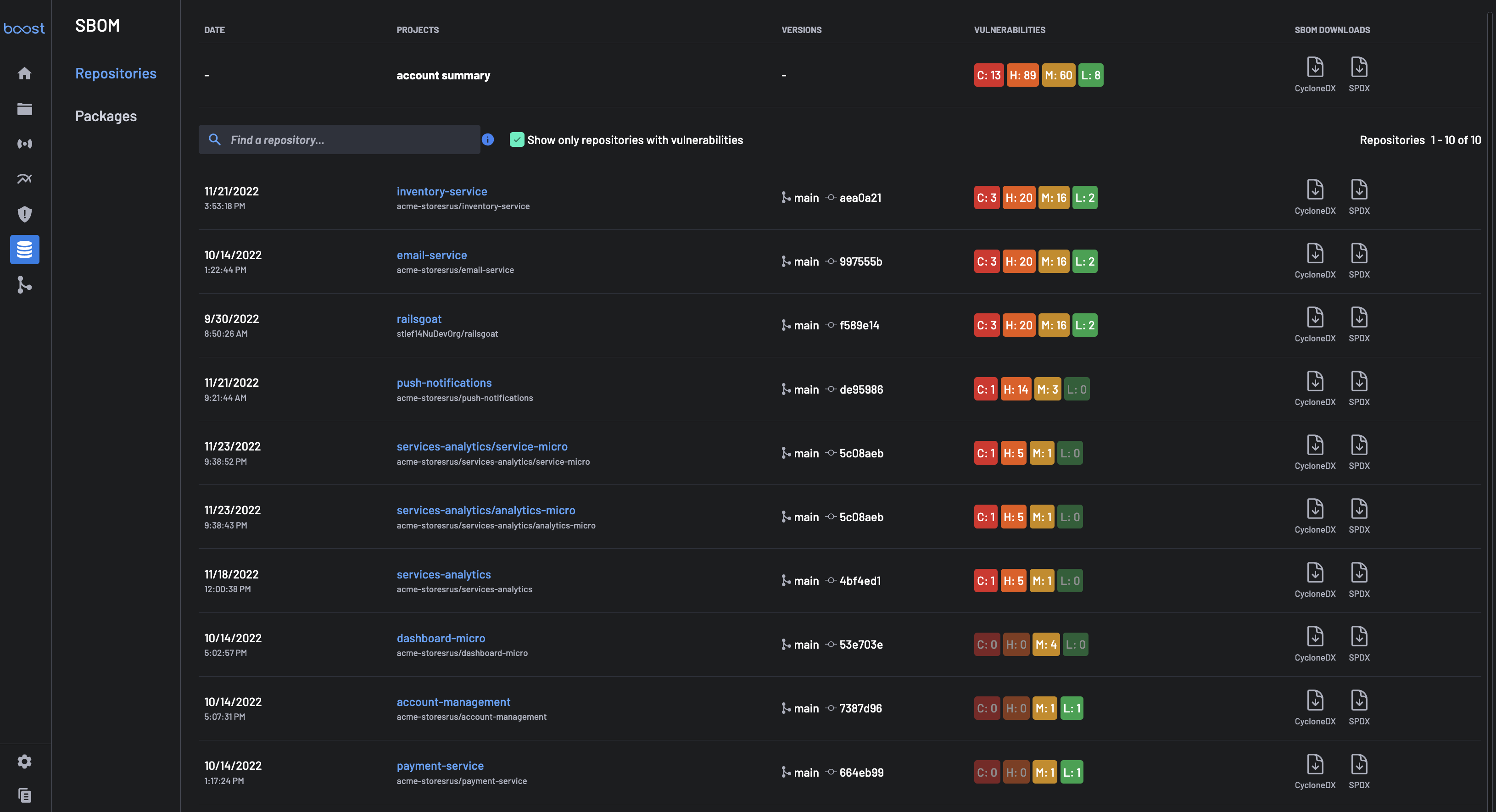
Accessing the Projects' SBOM¶
To access the SBOM service, select SBOM from the application's sidebar in the BoostSecurity dashboard. From the main SBOM view, the list of projects and their detected vulnerabilities, as well as the account-wide view, are provided.
Account Summary¶
The first section of the SBOM view is the account summary. The overall number of vulnerabilities per level is provided, i.e., the overall number of vulnerabilities across all projects and third-party components in the account. The SBOM document can be downloaded in either Cyclonedx or Spdx format for the account, from the account summary. The account summary SBOM documents contain the inventory of all components across all projects in the account.
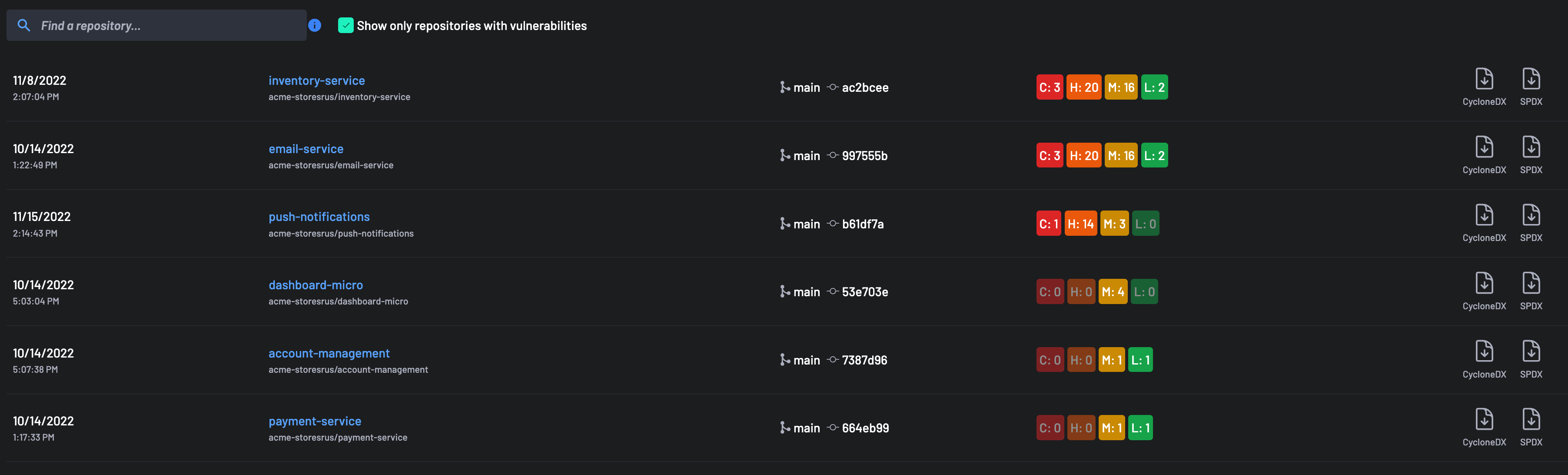
Projects Specific Summary¶
The projects summary section provides a project's based posture, providing the number of vulnerabilities summary
- Per severity level
- Per project for all projects in the account
The project-specific SBOM document can be downloaded in either the Cylonedx or Spdx format for any project from that section.
The projects are presented in descending order of vulnerability severities.
Note: The search area can be used to search for a project by name keyword across all projects in the account.
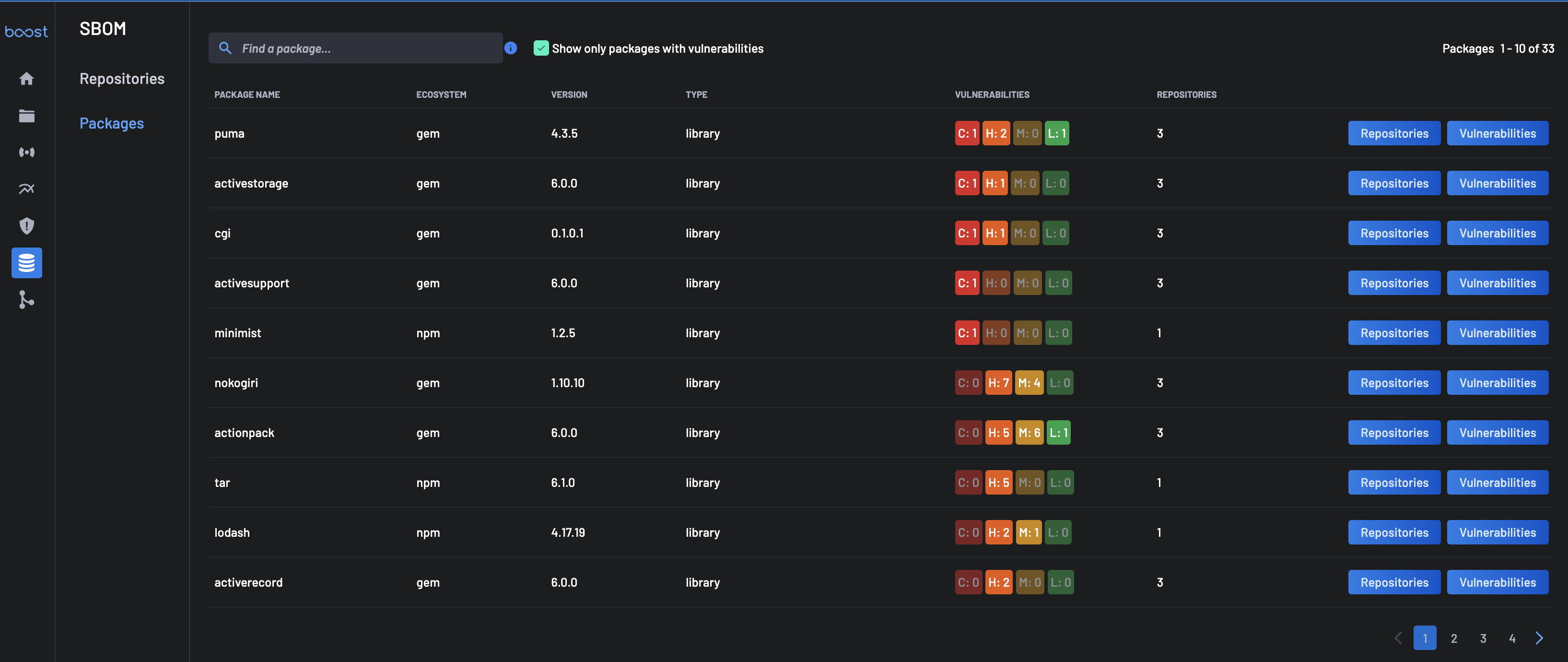
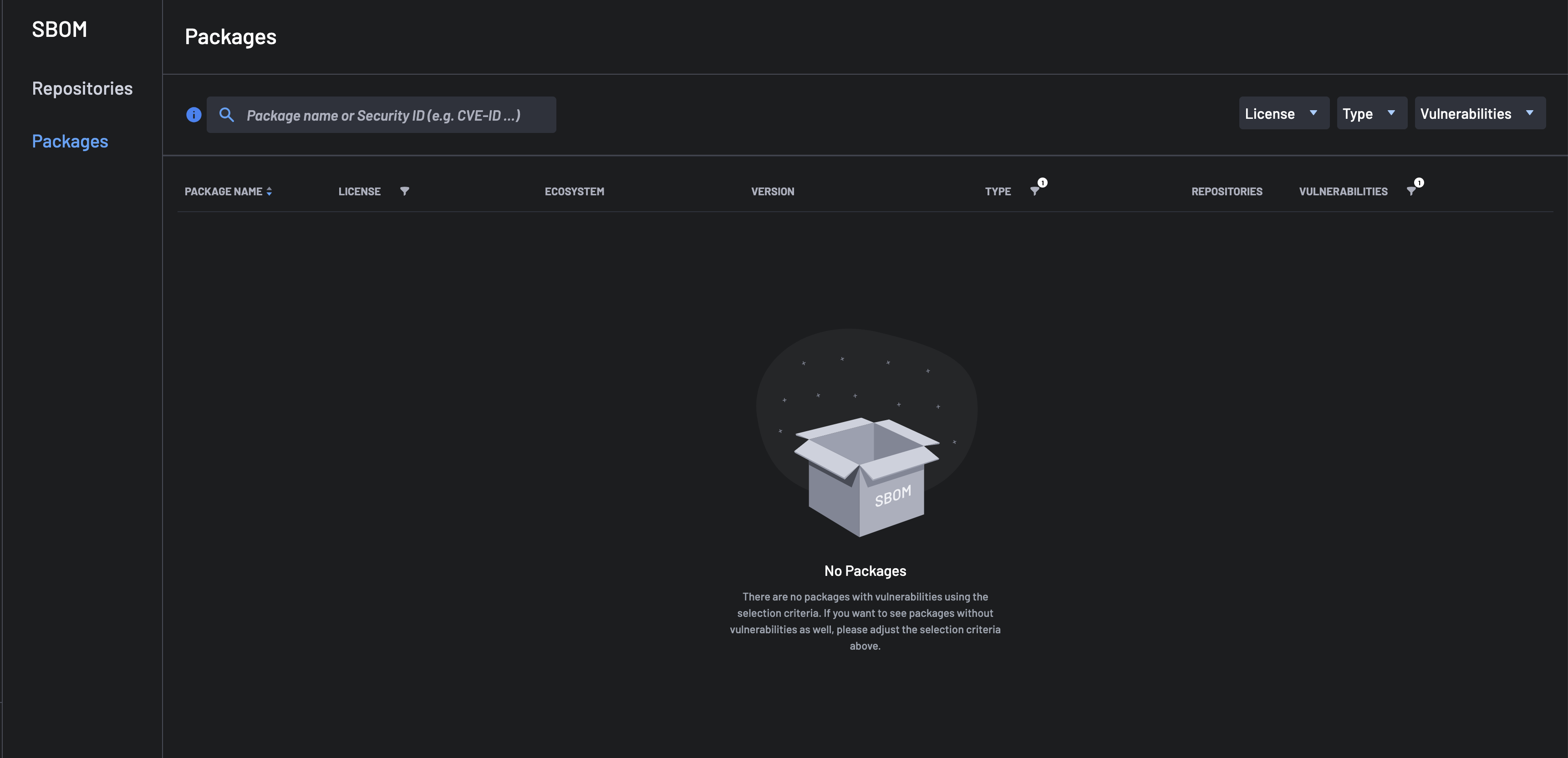
Packages view¶
The Packages view provides a quick way to find all packages and third-party components included across all projects in the account.
The packages are presented in decreasing order of number and severity of vulnerabilities. For each package, the following are provided:
- The number and severity of vulnerabilities.
- Number of repositories in the account, that includes the package.
Note: The search area can be used to search for a package by name or vulnerability id.
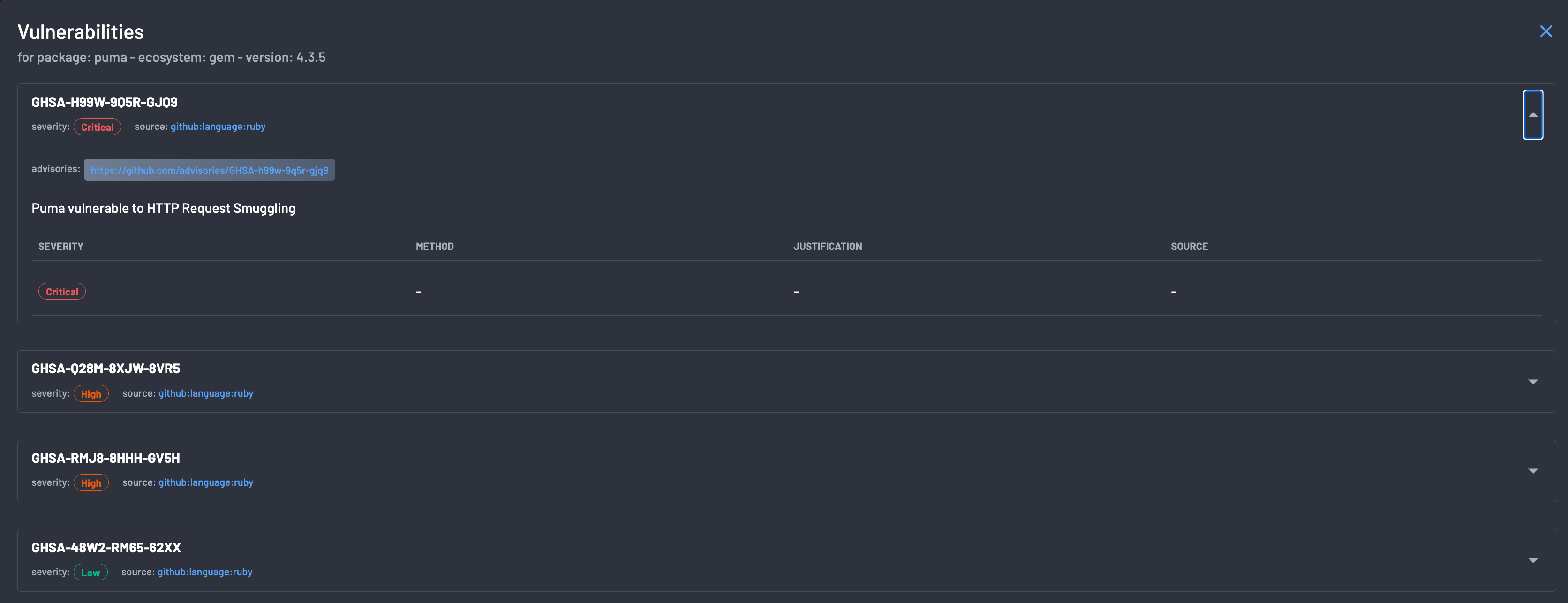
The vulnerability details for each package can be viewed by selecting the Vulnerabilities button. The list of vulnerabilities is presented, including the
- Vulnerability ID
- Severity
- Advisory
- Description
The vulnerabilities details view can be exited with "Esc" or by clicking the close (x) button.
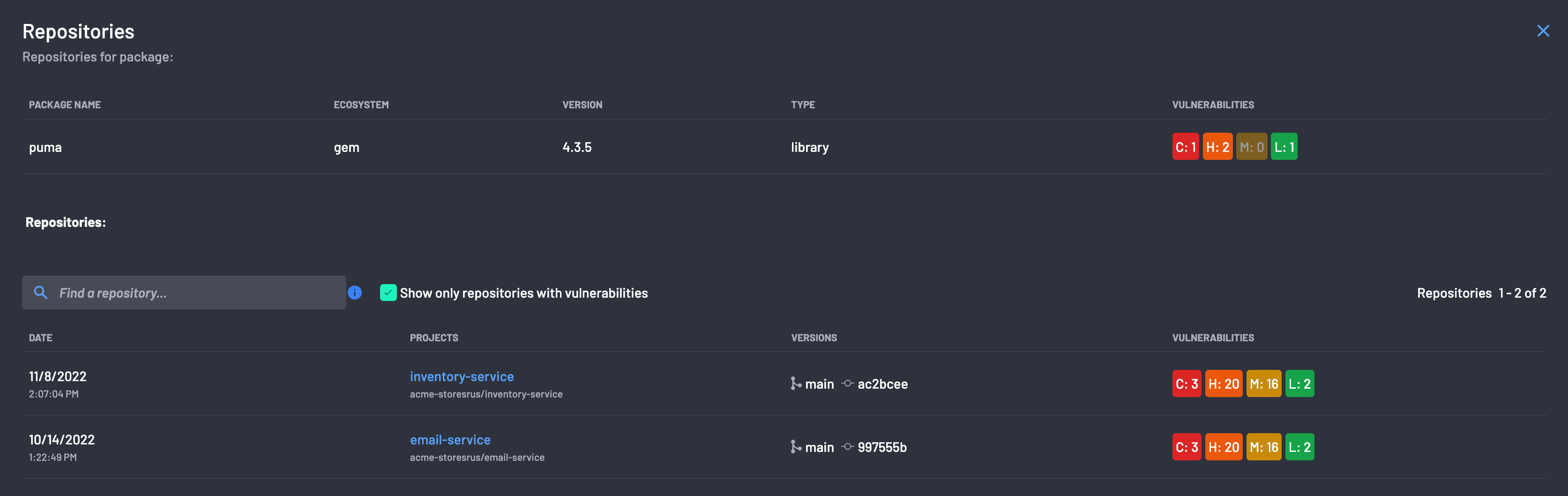
Likewise, the list of projects, including the package, can be viewed by selecting each package's Repositories button. The list of projects, including the package, is presented.
The project link can be selected from the list of projects, taking the user to the project-specific view.
If no results are found based on selected filters, you will be notified that no vulnerable packages meet the criteria.
FAQs¶
How to view packages associated with disallowed licenses¶
To view Packages associated with disallowed licenses:
- Navigate to the Packages Page.
- Click on the License dropdown at the page's top-right.
- You can search for a specific disallowed license in the search box or select one or more licenses to get a list of packages with such licenses.
How many scanners can a project have that output SBOM?¶
Note that you can only have one scanner that outputs SBOM per project.