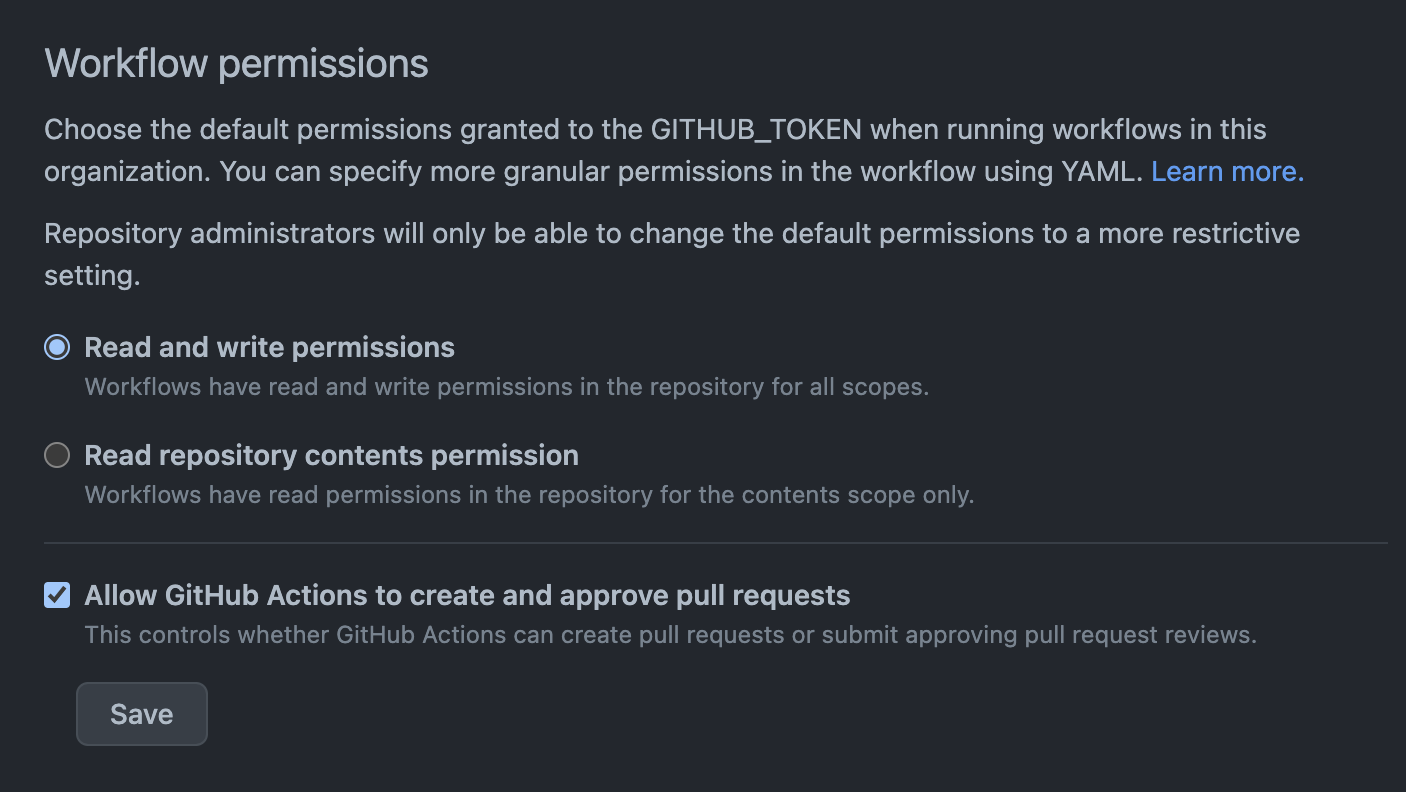
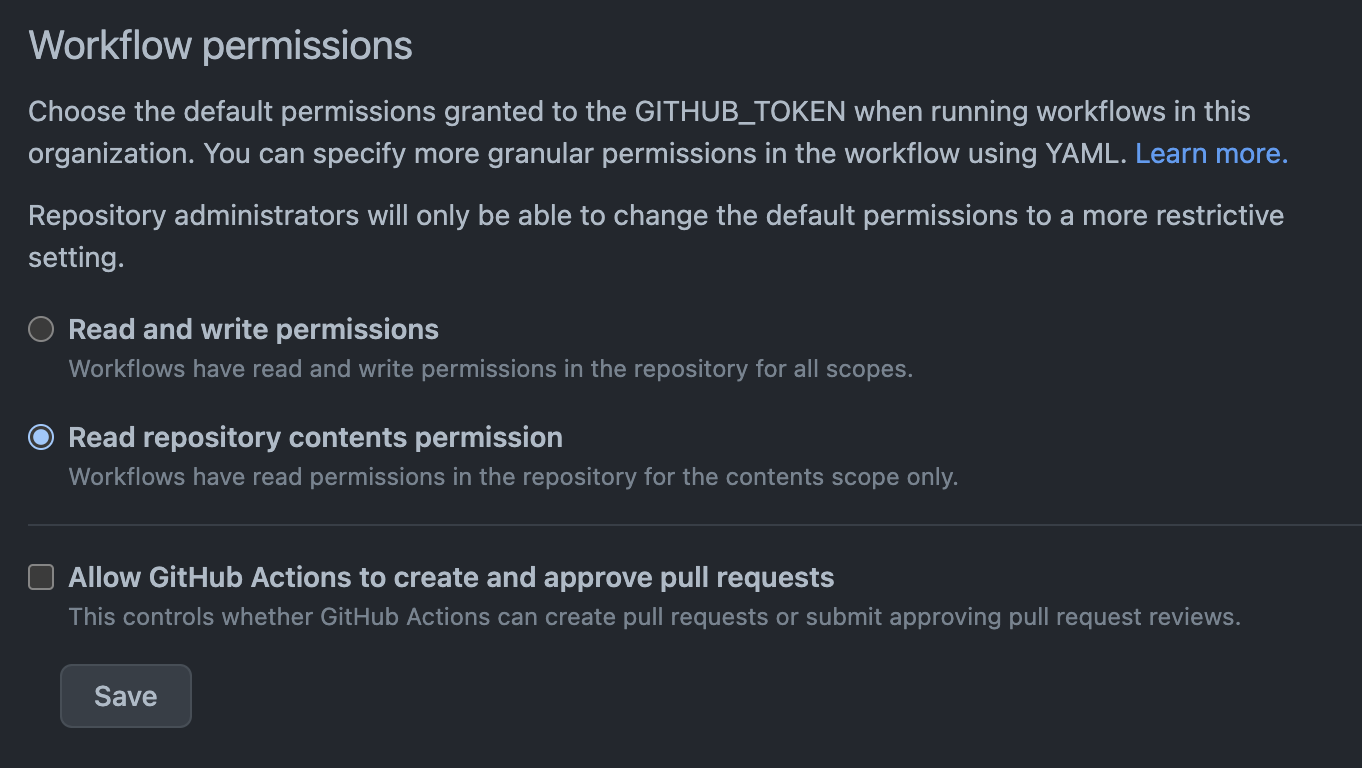
GitHub Actions can approve pull requests¶
Checks for GitHub organizations that allow GitHub Actions to create and approve pull requests.
Allowing GitHub Action Workflows to request tokens for the GitHub API with elevated privileges that can automatically create and approve Pull Requests is dangerous. If a rogue workflow can self-approve malicious code changes, it can effectively bypass any human code review. A Continuous Integration (CI) system, such as GitHub Action, should be designed and configured as securely as production systems. In fact, since built artifacts coming out of such system are often deployed automatically (CD / Continuous Deployment) any compromise of CI/CD will indirectly affect production as malicious code can end up in production.
Examples¶
Insecure Example
Secure Example