Filters Options for Findings¶
Utilize the filters on the Findings page to easily locate specific findings that are relevant to you.
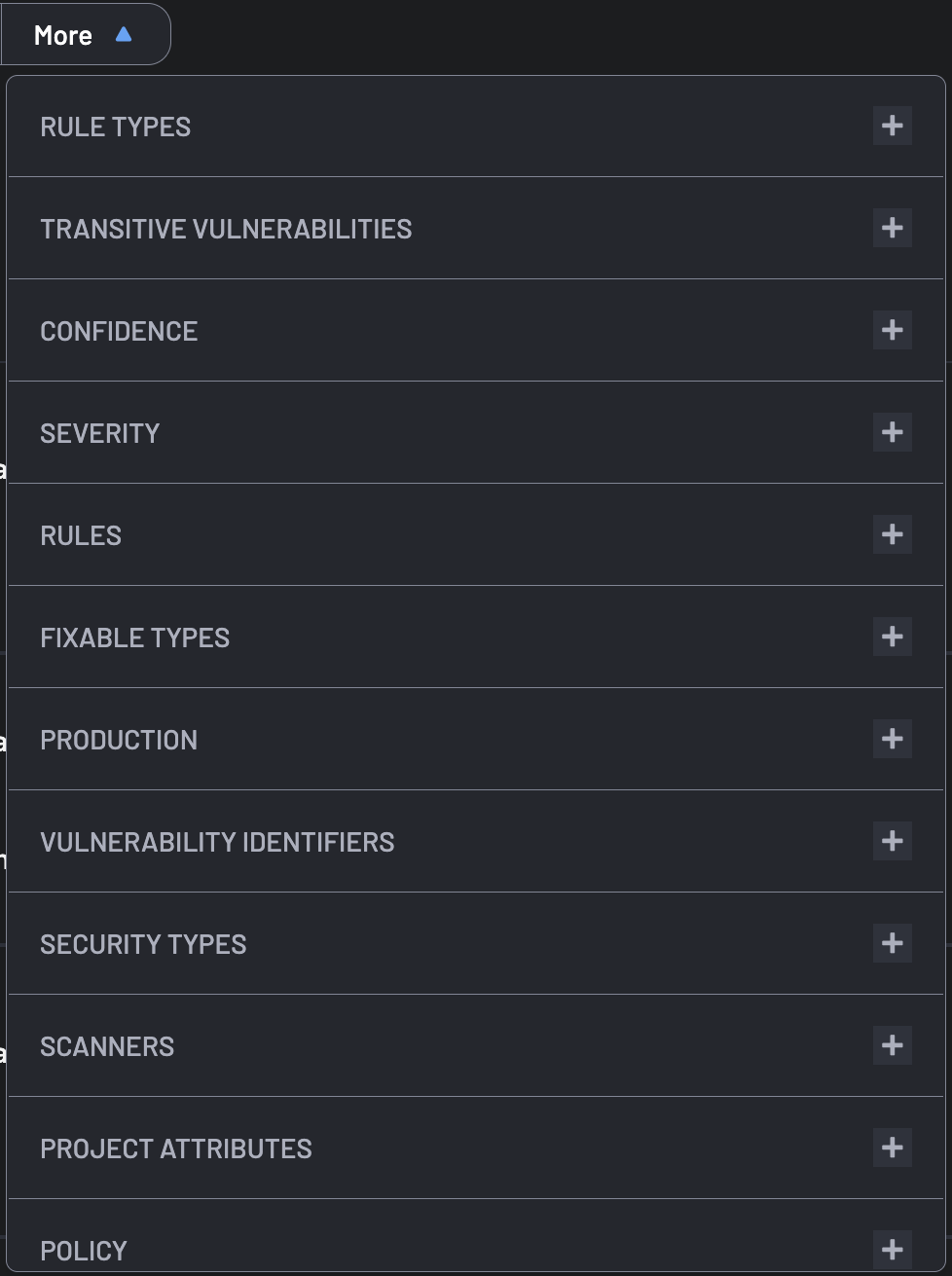
Additional filters are accessible via the More menu, organized into distinct categories for enhanced navigation and clarity, as illustrated below.
Findings Filter Groupings¶
The More menu organizes filters into logical groupings to streamline your workflow and improve accessibility. These groupings include:
- DETECTION: Filters related to the identification process. They include Scanners and Security Types.
- FINDING CLASSIFICATION: Includes filters for detailed analysis, such as Rules, Rule Types, Source, and Vulnerability Identifiers.
- FINDING DETAILS: Comprehensive filters that provide in-depth insights into each finding, encompassing CVSS scores for severity assessment, Dev Dependency status, Exploitability Risk (EPSS) for attack likelihood, Fixable and Not Fixable classifications, License compliance, Secrets Validity for credential security, Transitive Vulnerabilities in dependencies, and Vulnerable Code Reached to indicate potential exploit paths.
- FINDING LOCATION: Precision filters that pinpoint the exact origin of findings, including Source (File Location for SCA/SAST scans), Source (Image for Container scans), and Source (Package for SCA dependencies), enabling targeted investigation and resolution.
- FINDING TRIAGE: Filters designed to prioritize and manage findings effectively, including Confidence, Severity, and Verified Manually, to assess the reliability and urgency of each finding.
- RESOURCE DETAILS: Filters that provide context about the resources associated with findings. They include Manual Tag, Organizations, Policy, and Project Attributes.
- RUNTIME: Focuses on runtime-specific filters to assess findings during execution. They include Kubernetes Service, Kubernetes Cluster, and Production.
Here are the explanations for each filter:
Types of Filters¶
- Confidence: Filter Findings by confidence level: "High", "Medium", "Low", or "Not Set" for findings generated by scanners that do not populate this field.
- Severity: Separates higher-priority Critical risks from lower-priority Warning, Minor, or Not Set.
- Manual Tag: Filters findings based on custom tags assigned to specific resources (e.g., repositories, organizations). Tags such as critical, outsourced, or non-prod can be created and applied to help group and track security issues across similarly categorized assets.
- Rule Types: Select specific scanner rules for targeted security checks.
- Organizations: Focus on findings for a specific organization or a group of organizations.
- Finding Types: Filter results by Violations or Findings. A Violation is a Finding that violates a Policy.
- Fixable Types: Focus on Fixable and Not Fixable security issues, making it easier to solve known vulnerabilities.
- Vulnerability Identifiers: The Common Vulnerabilities and Exposures Identifier (CVE ID) of the vulnerable libraries (SCA) to focus upon.
- Suppressed Status: Filter Findings by their state: Not Suppressed (the default state) or Suppressed.
- Security Types: Categorize security Findings by Container, SAST, or SCA for easier organization.
- Scanners: Filter for findings by the scanner that found them.
- Source: Filter findings by the file in which they are found. The security type groups the lists of said files, SAST for custom code, SCA for libraries, and Container Scanning for container images.
- Exploitability Risk: Exploit Prediction Scoring System (EPSS) predicts the likelihood of a CVE being attacked within the next 30 days.
- CVSS: The Common Vulnerability Scoring System (CVSS) gives a higher number to more dangerous security vulnerabilities found in commonly used libraries. Scores range from 0 to 10.
- Transitive Vulnerabilities: This is a filter for findings related to vulnerabilities found in dependencies that software code components use. It is further divided into sub-filters namely:
- Transitive Dependencies: These are vulnerabilities found in the code components used to build software.
- Direct Dependencies: These are vulnerabilities found in the code used for software.
- Project Attributes: This filter allows users to categorize and filter findings based on specific characteristics or metadata associated with a project, such as project contributors, associated services or other custom attributes.
- Policy: This filter enables users to categorize and filter findings based on predefined security policies set within the organization.
- Kubernetes Service: This filter allows users to isolate and analyze findings specific to individual Kubernetes services within a cluster.
- Kubernetes Cluster: This filter focuses on findings associated with entire Kubernetes clusters.
- Production: This filter narrows down findings to those occurring in production or non-production environments.