Enabling SBOM Content Retrieval for a Container Image in AWS ECR¶
This guide explains how to set up SBOM (Software Bill of Materials) content retrieval for a container image in AWS ECR (Elastic Container Registry) via BoostSecurity integration.
Note
To use this feature, you must be using AWS Inspector.
Permissions¶
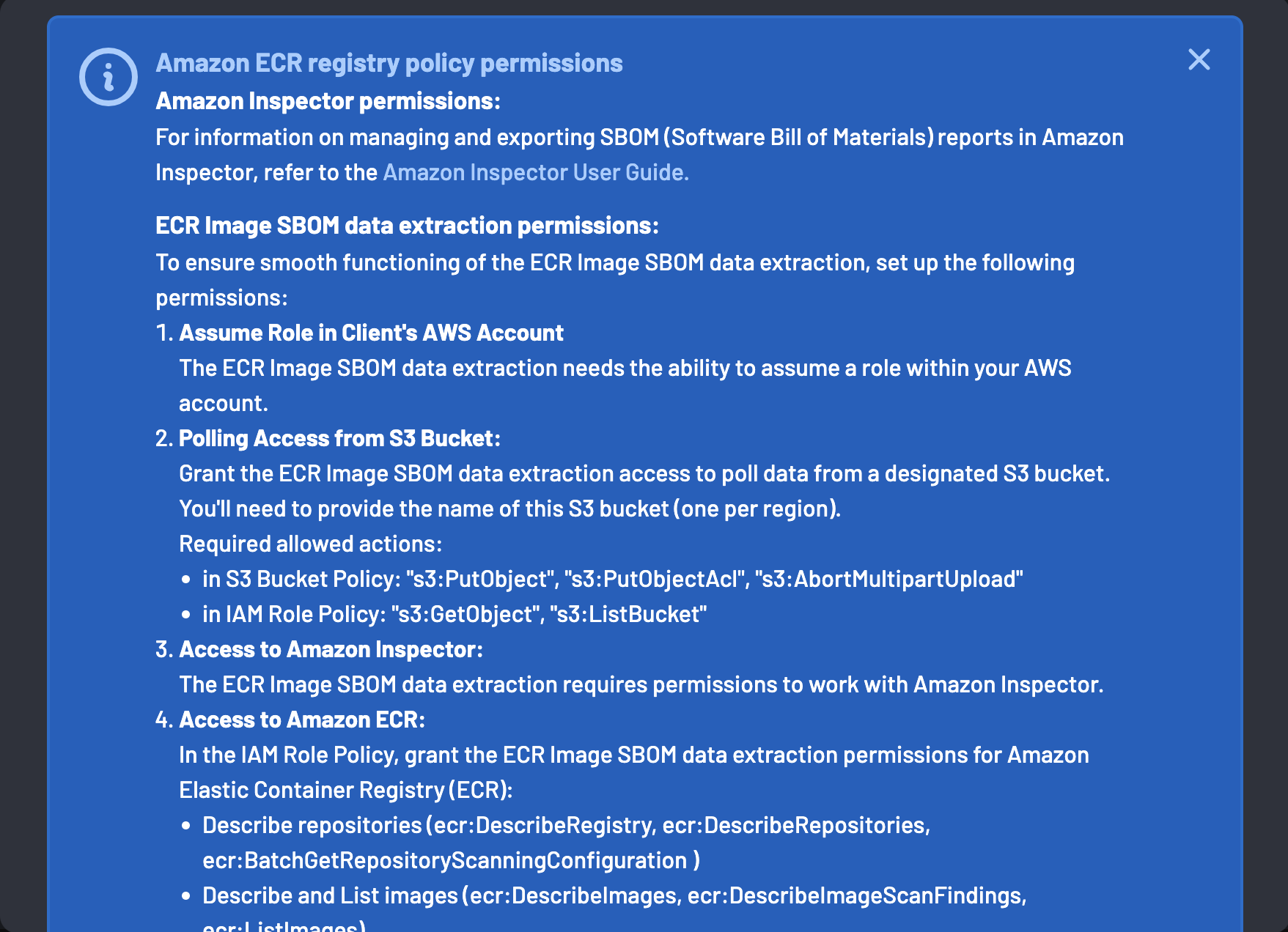
To enable a successful integration, ensure these permissions are satisfied:
Integration Steps¶
Follow these steps to enable SBOM content retrieval for a container image in AWS ECR:
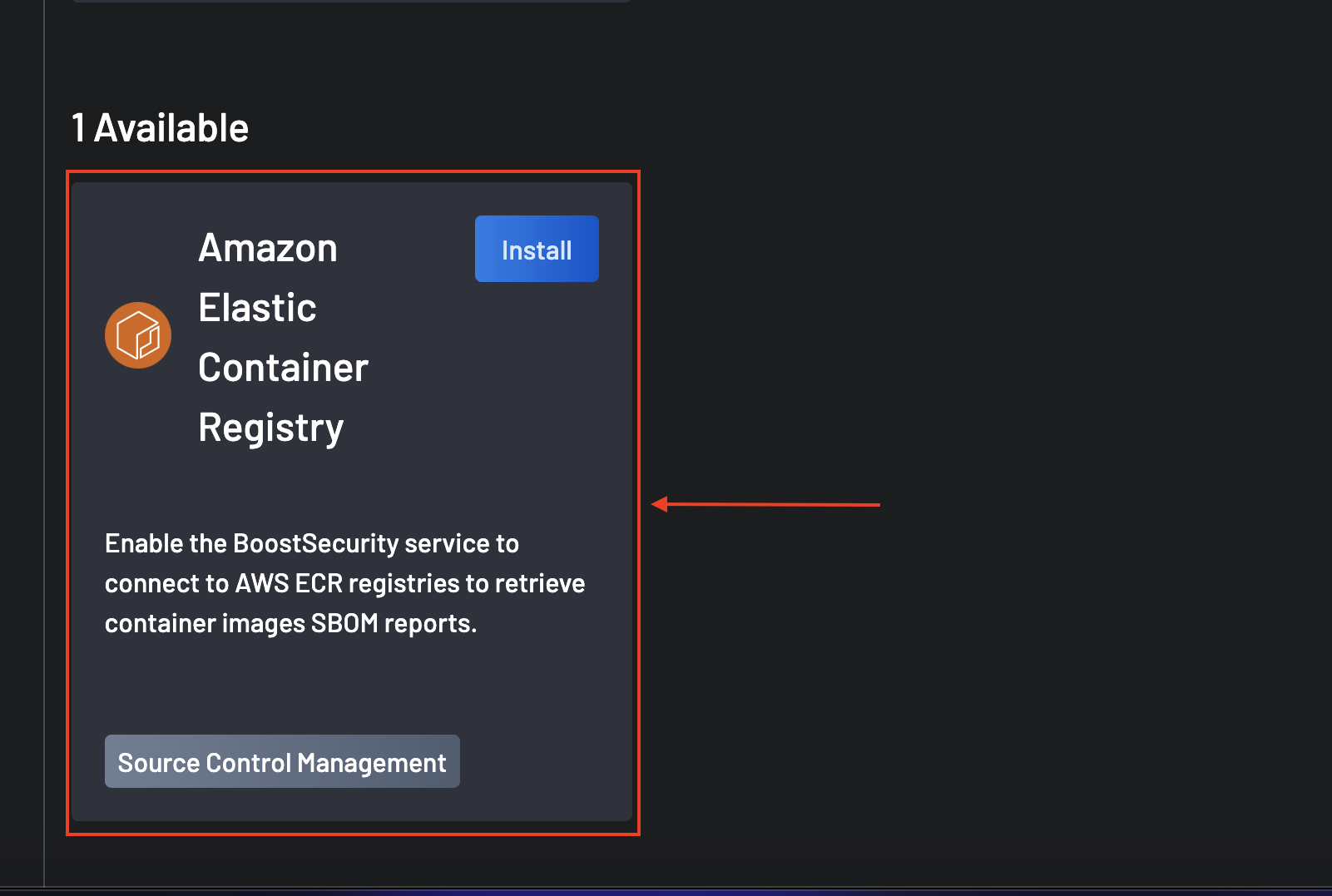
- Navigate to the Integrations page.
-
Scroll to the
Availablesection and select Amazon Elastic Container Registry. -
Click on the Install button.
-
A list of permissions required for the integration are displayed.
-
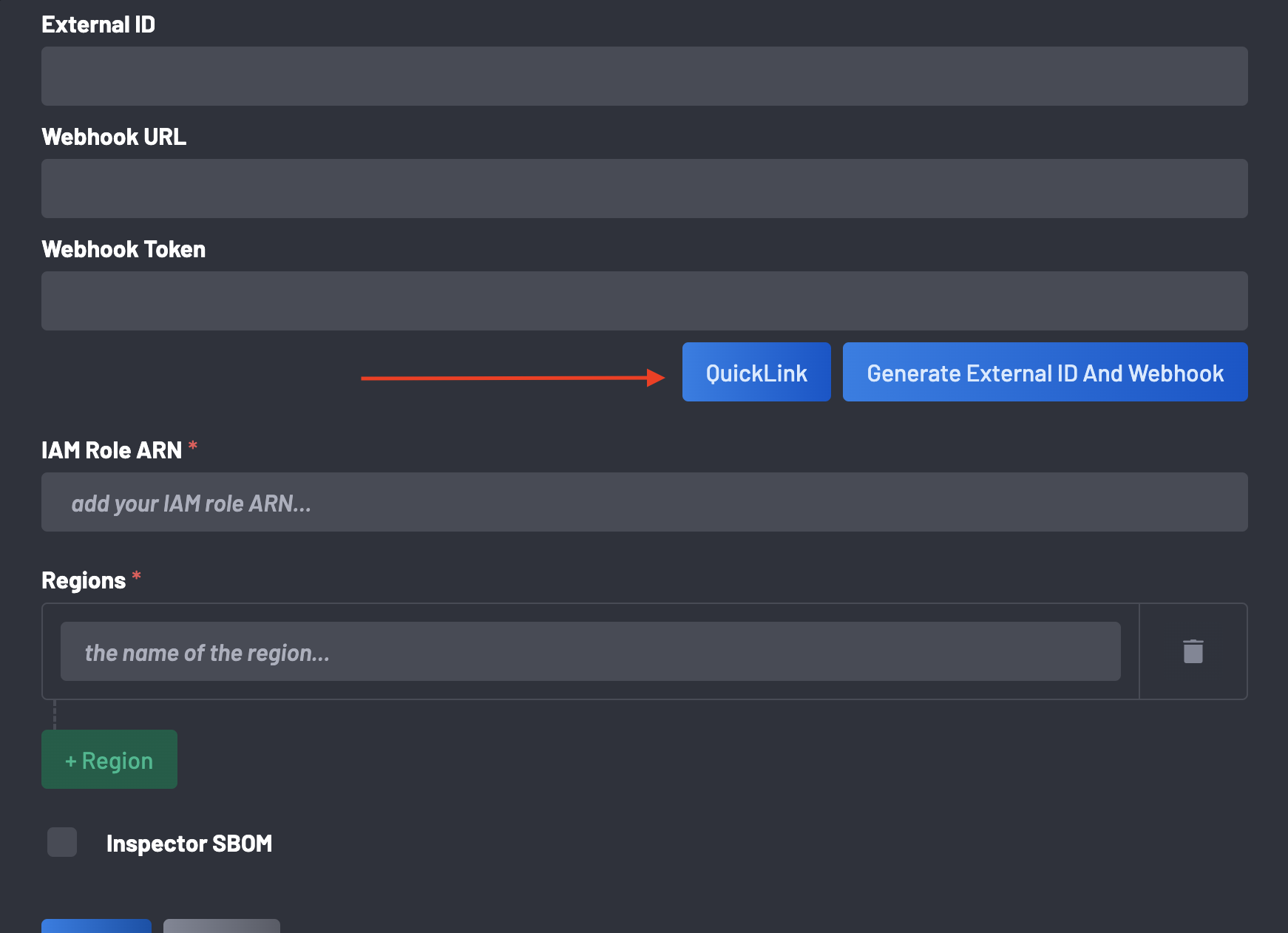
Click the QuickLink button. This will redirect you to the AWS Portal to deploy a CloudFormation Stack.
Note
To continue, you need to be signed in to AWS with the required permissions.
-
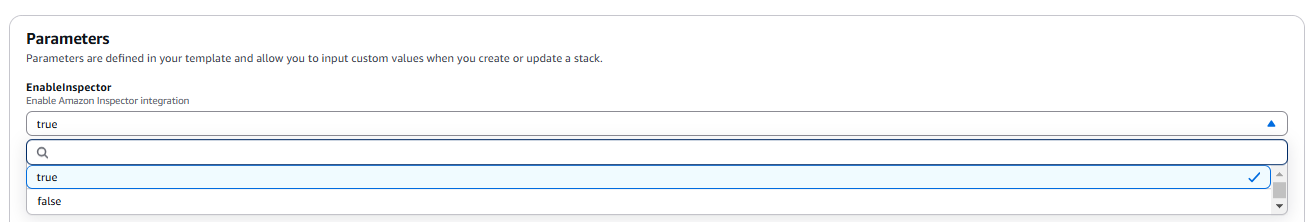
Change the stack parameter EnableInspector in the AWS Portal to
true.Note
if this is not done, you won't be able to enable the Scan, but you will still have visibility of your images within Boost
-
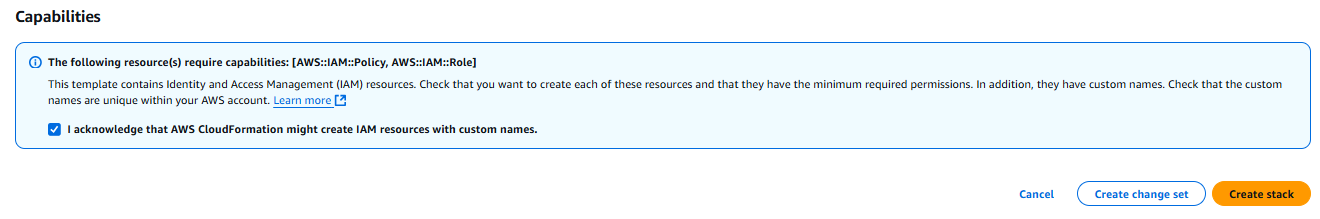
On the bottom of the page, select the checkbox shown below and click the Create Stack button.
-
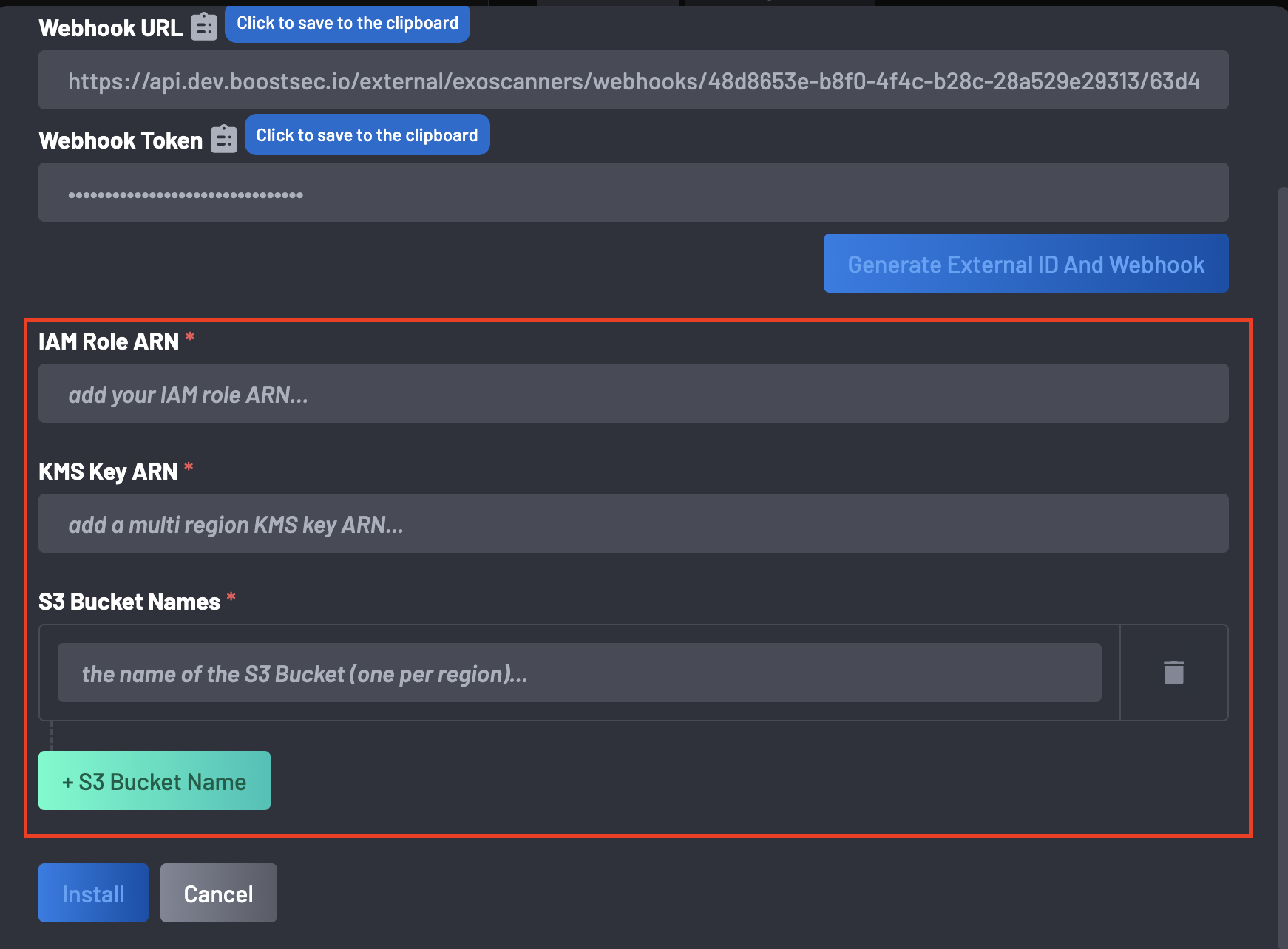
Return to the ongoing integration, select the Inspector SBOM checkbox, and provide the following information created on the CloudFormation Stack above:
- IAM Role ARN
- Regions
- KMS Key ARN
- S3 Bucket Names: Add bucket names using the + S3 Bucket Name button. Use the delete button to remove or replace bucket names.
-
Click on Install to complete the integration.
Your AWS ECR integration is now successfully configured for SBOM content retrieval.