Findings¶
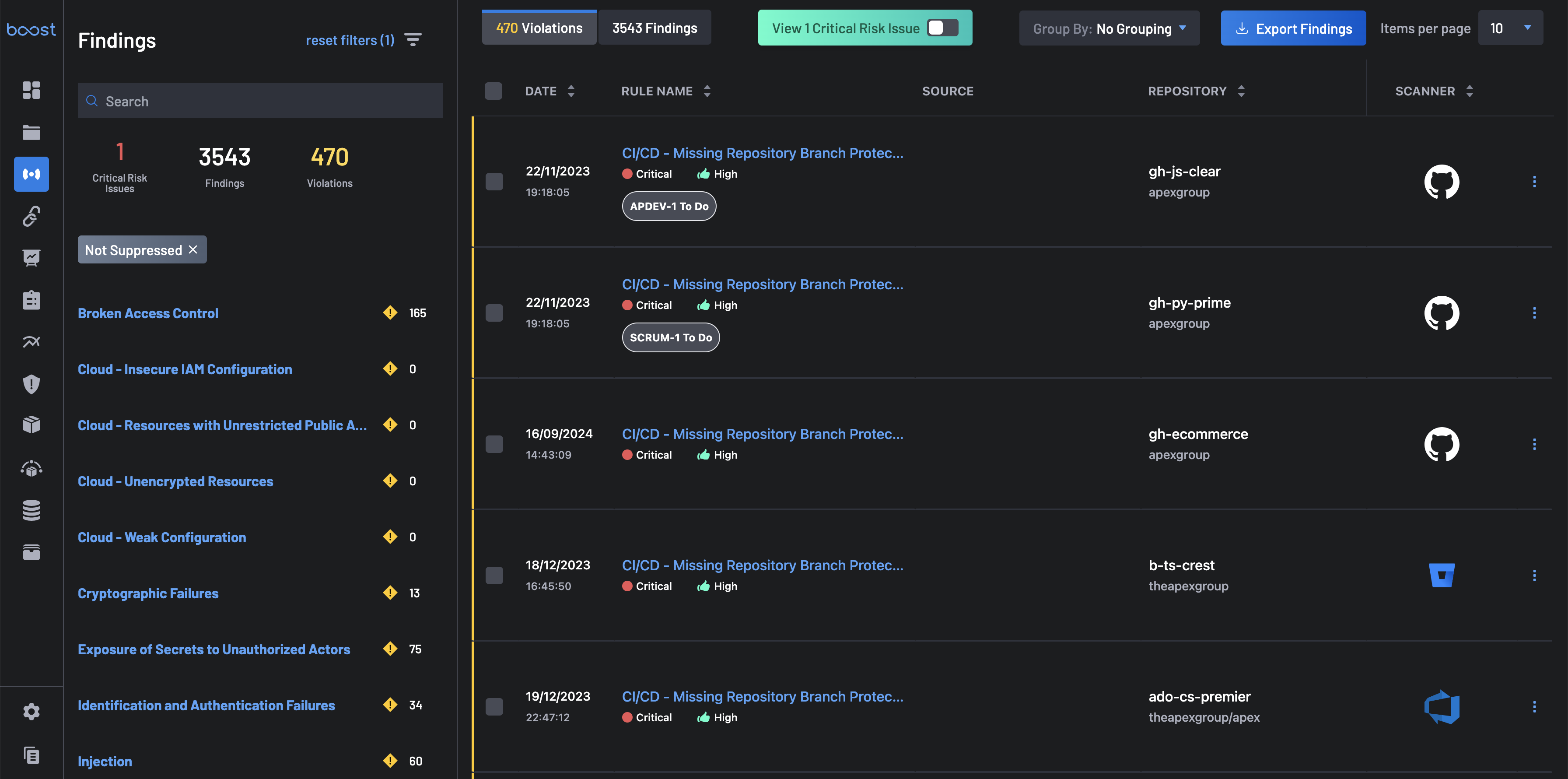
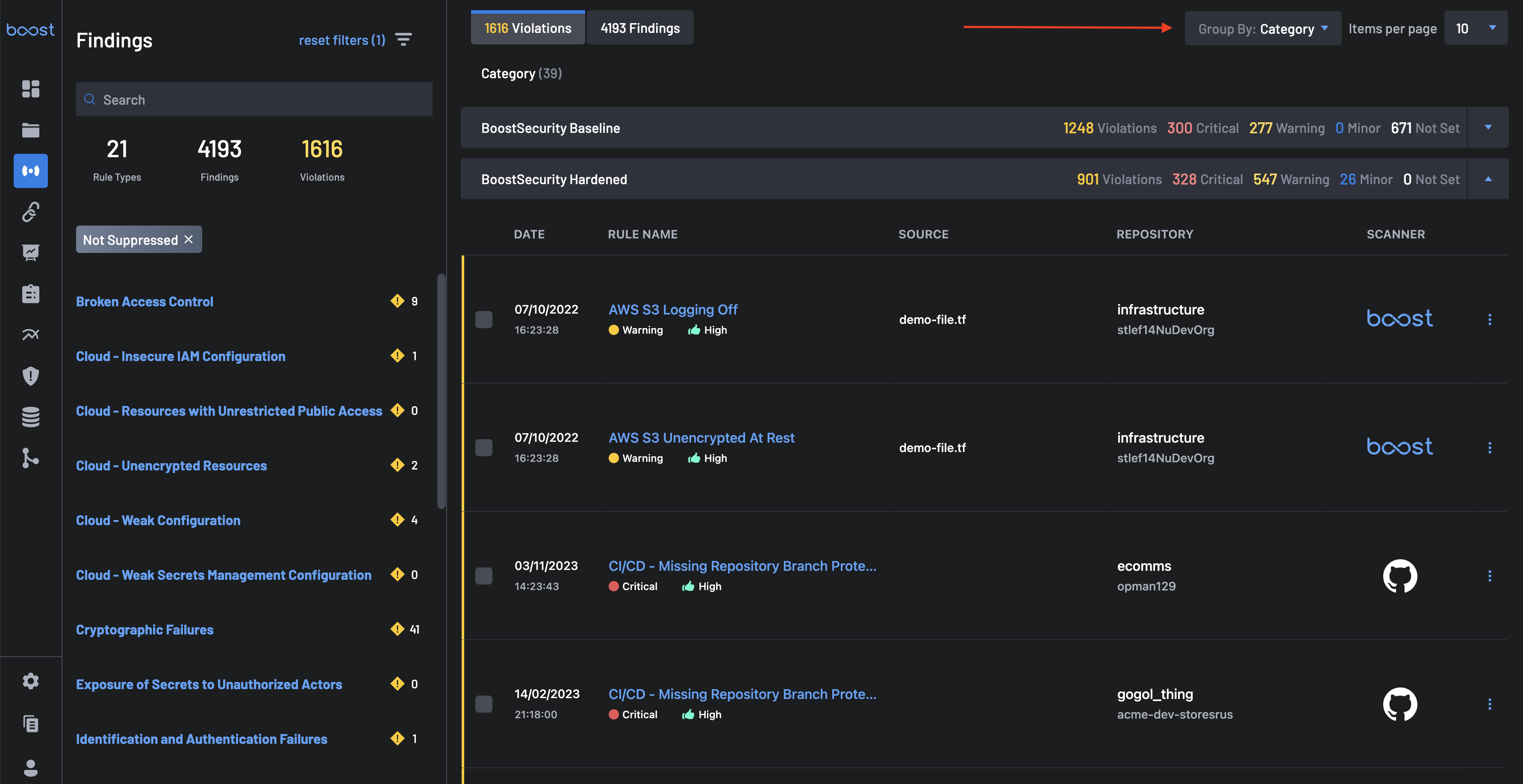
The Findings page provides a detailed list of identified vulnerabilities, including their severity levels and affected code components. The findings page also offers the flexibility to tailor your view by applying filters, searching and grouping bulk selection of findings, and more.
Key Features¶
Violations and Findings¶
The Findings page offers an improved user experience by categorizing "Violations" and "Findings" into distinct tabs.
Critical Risk Issues¶
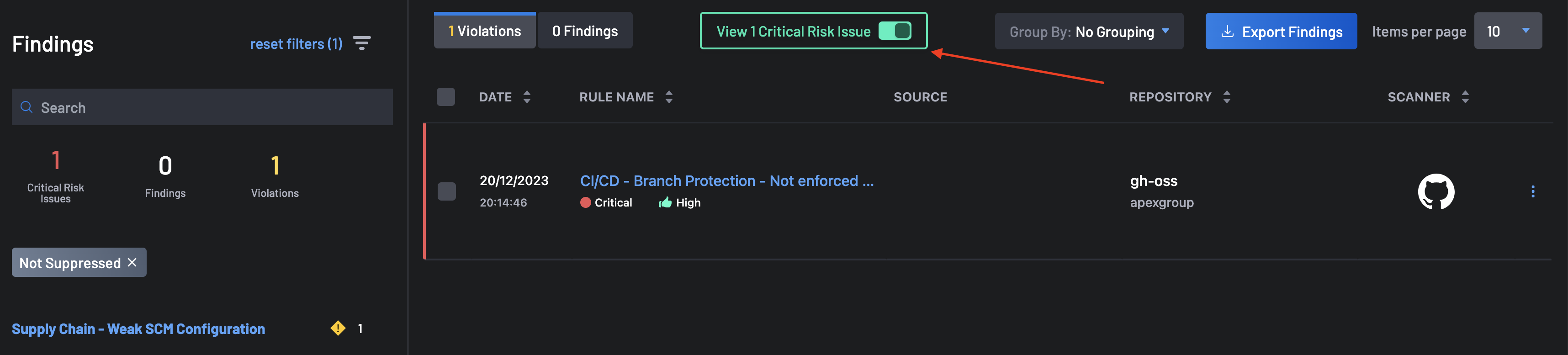
The Findings page allows you to focus on the most important risks that needs to be addressed immediately. You can view these issues by clicking the Critical Risk Issues tab under Filter By to see these critical risks. For issues to be categorized as critical risk, they must include one of or all the following issues:
- PII Detection & Missing Branch Protection
- Privileged Container Running
- Lack of Code Reviewers, etc.
Findings Filters¶
Improve findings management using advanced filters based on Severity, Acknowledgment Status, Manual Tag, etc.
Findings Groupings¶
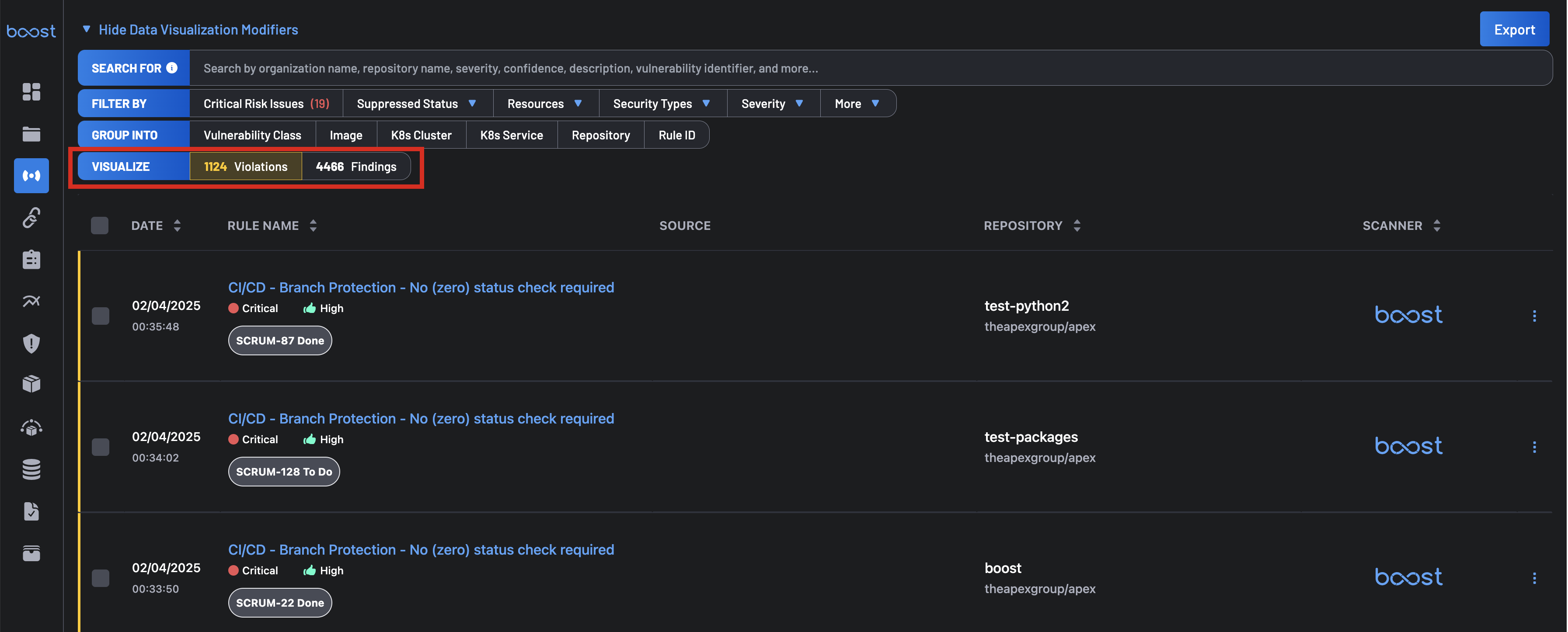
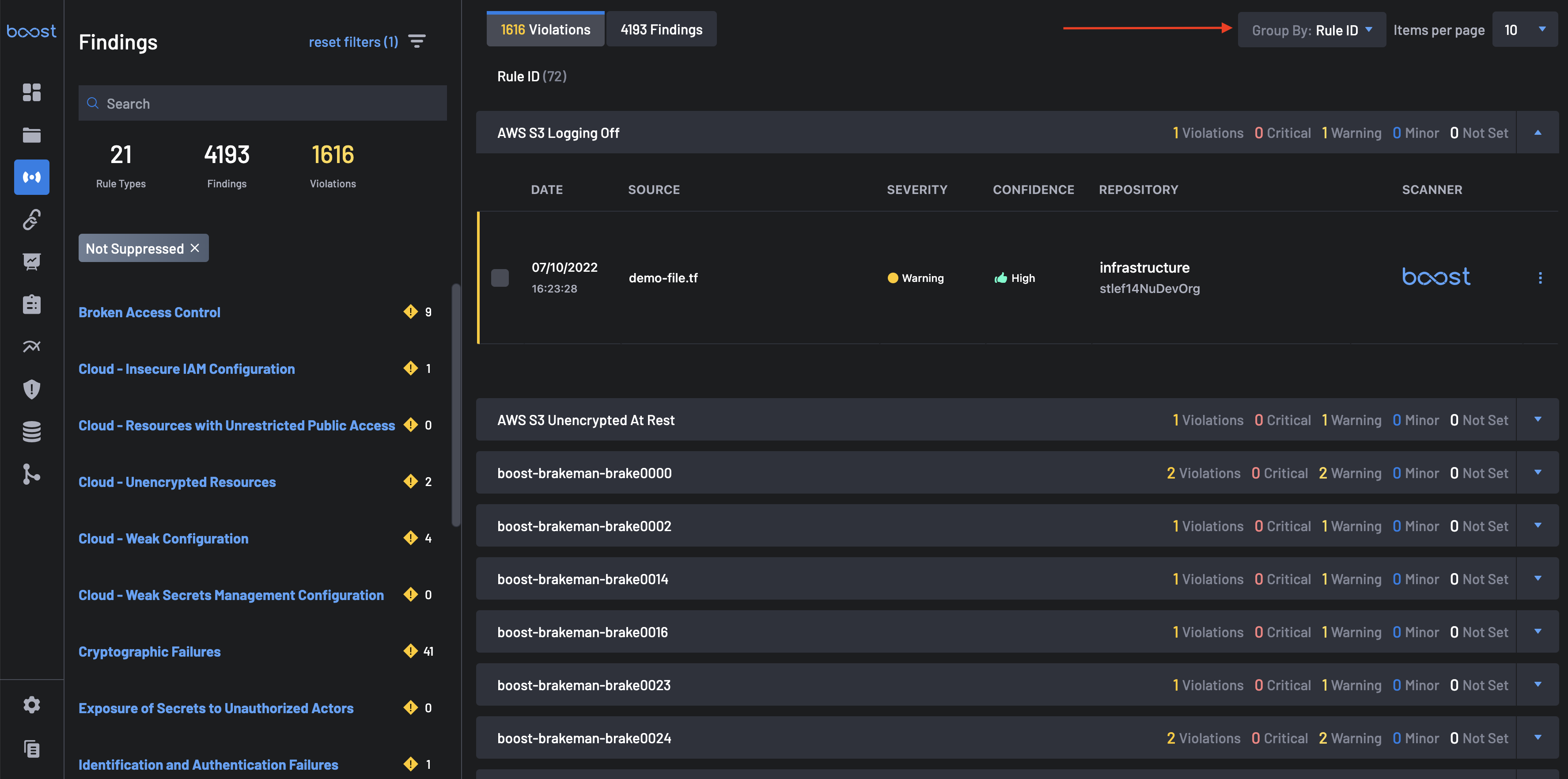
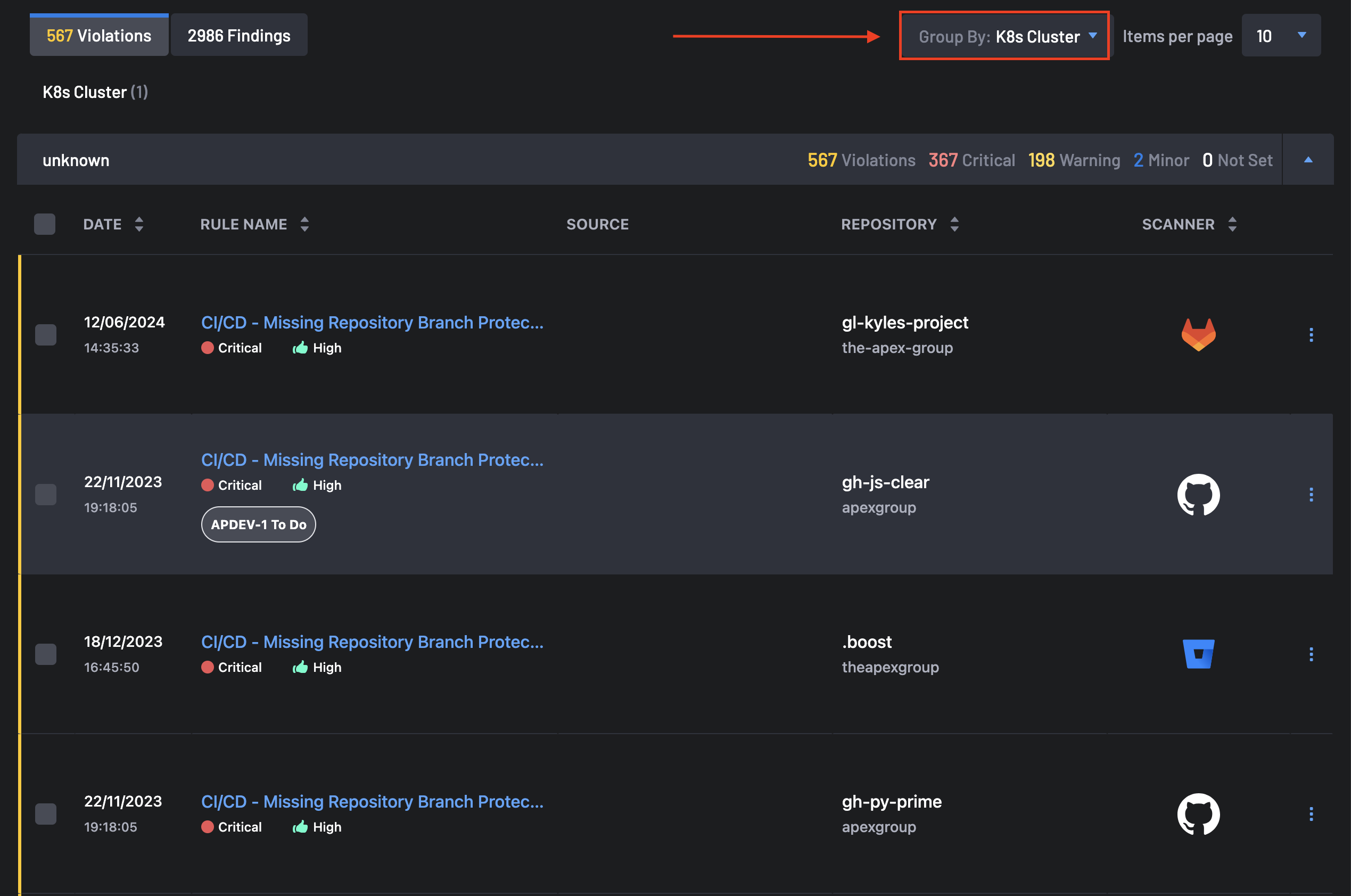
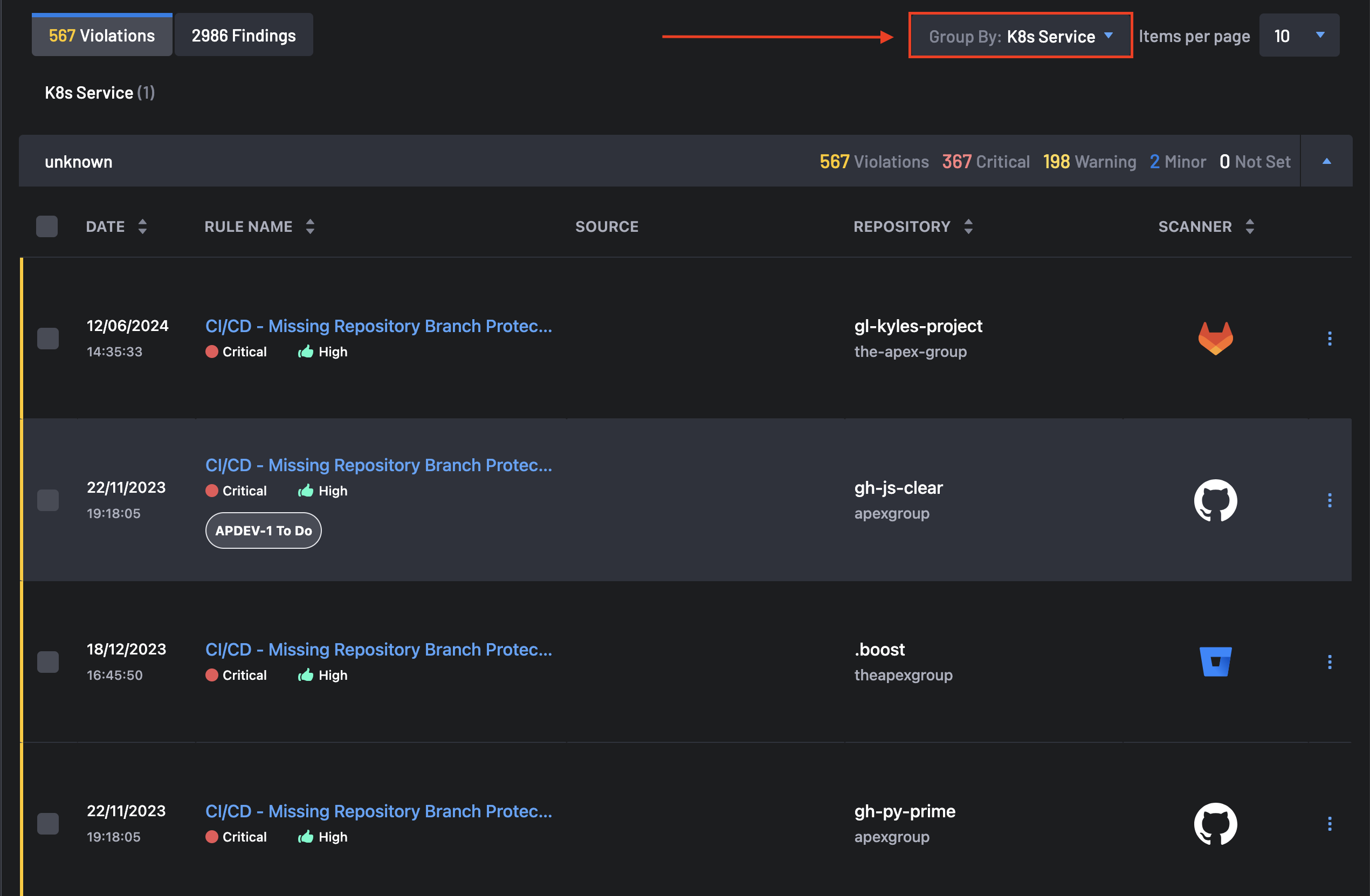
The Group Into filter allows you to group violations and findings by Rule ID, Repository, Image, Vulnerability Class, K8s Cluster, or K8s Service.
- Grouping By Rule ID: This group contains information about Rule IDs, the number of findings, violations, and their severities. Once you expand each result, you can see the Date, Rule Name, Source, Repository, and Scanner.
To get findings groupings by rule id, select Rule ID in the Group Into tab.
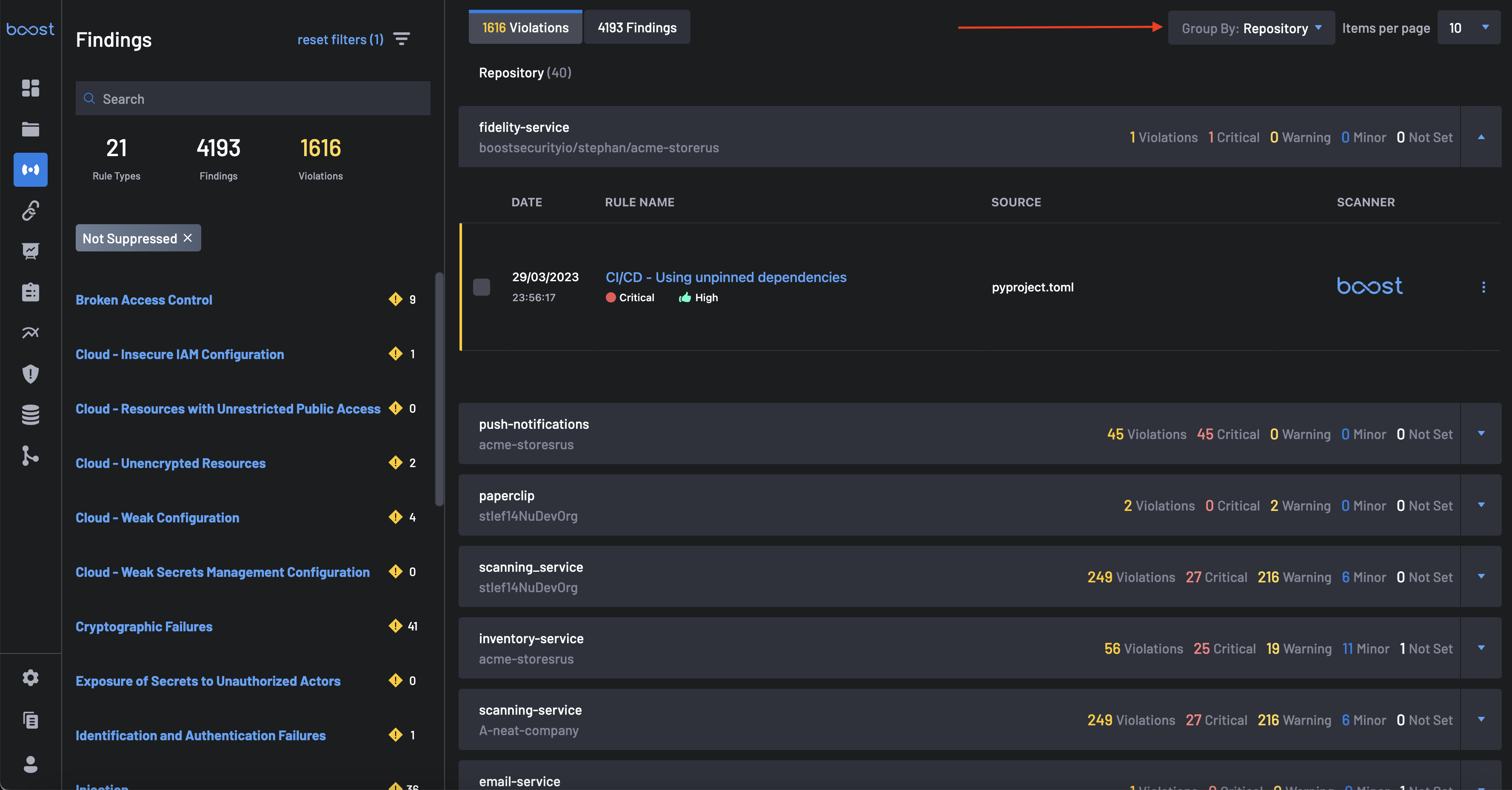
- Grouping By Repository: This group includes the repository, findings, violations, and severities. Once each result is expanded, it displays the date, rule name, repository, source, and scanner.
To get findings groupings by repository, select Repository in the Group Into tab.
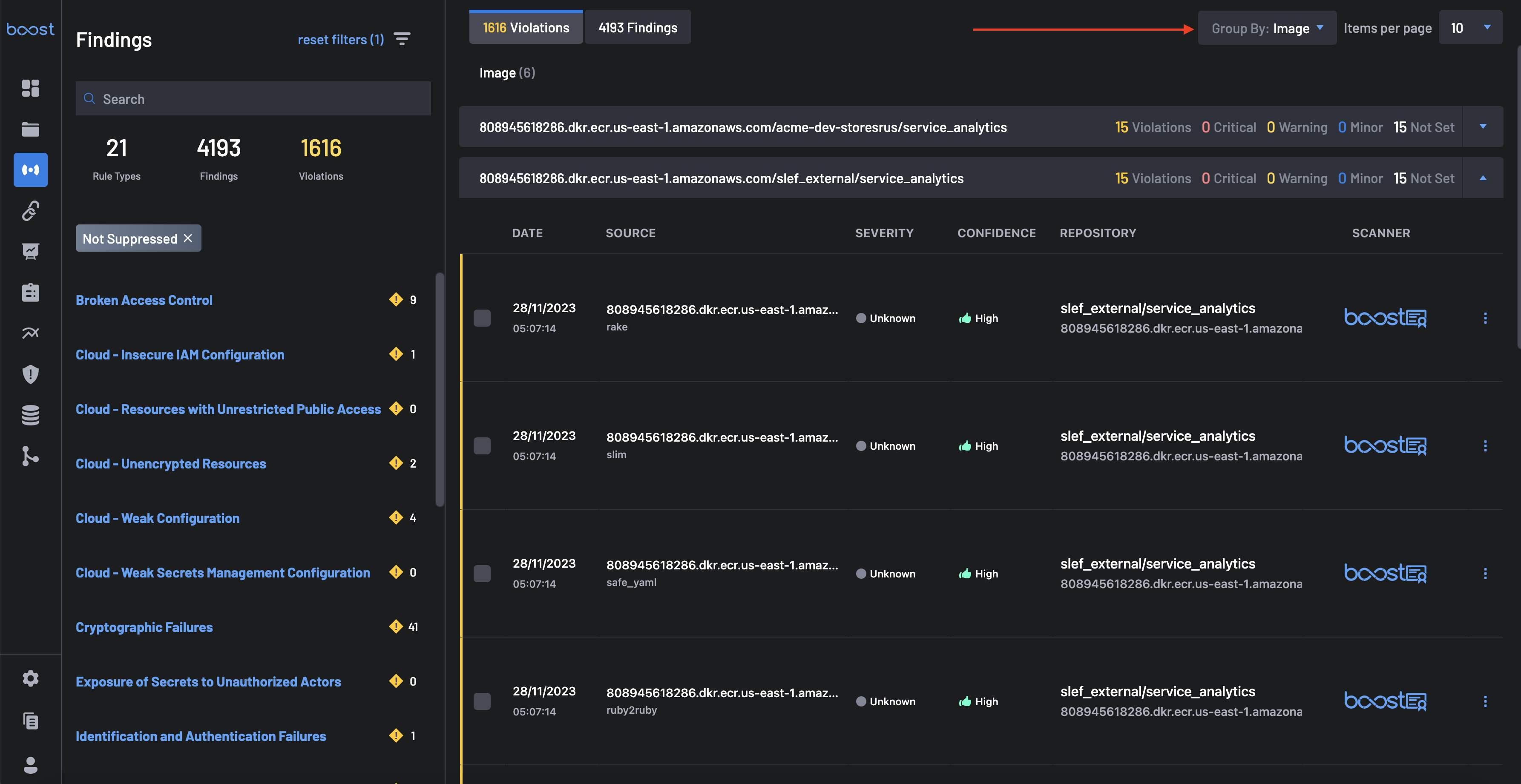
- Grouping By Image: Here, not all findings belong to the container type. Therefore, grouping by image is like filtering by container type and grouping by image. This group contains information about the image, such as the number of findings, violations, and severities.
To get findings groupings by image, select Image in the Group Into tab.
- Grouping By Vulnerability Class: This group includes the critical risk issues, findings, violations, and severities. Once each result is expanded, it displays the date, rule name, severity, source, repository, and scanner.
To get findings groupings by vulnerability class, select Vulnerability Class in the Group Into tab.
- Grouping By K8s Cluster: This group contains violations, critical issues, warning, and minor findings grouped into specific Kubernetes clusters. Once expanded, the date, rule name, source, repository, and scanner are displayed for each Violations and Findings.
To get findings groupings by K8s clusters, select K8s Cluster in the Group Into tab.
- Grouping By K8s Service: This group contains violations, critical, warning, and minor findings grouped into specific Kubernetes services. Once expanded, the date, rule name, source, repository, and scanner are displayed for each Violations and Findings.
To get findings groupings by K8s services, select K8s Services in the Group Into tab.
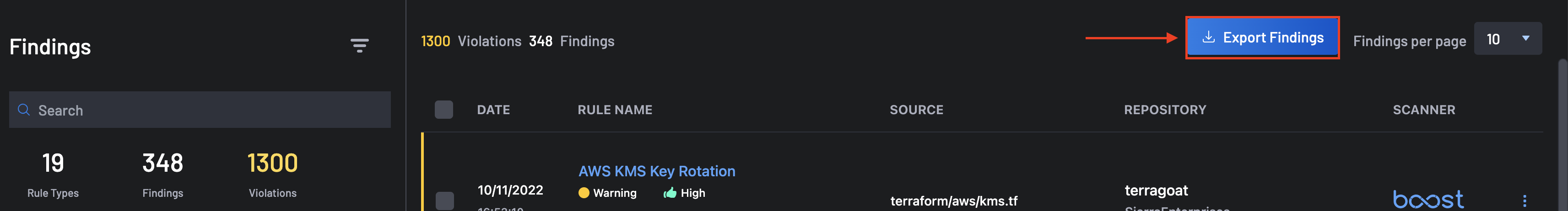
Export Findings¶
This feature provides a way to export findings data in a .CSV format for further analysis and reporting. You can get a full findings report by clicking the Export Findings button located at the top-right corner of the screen.
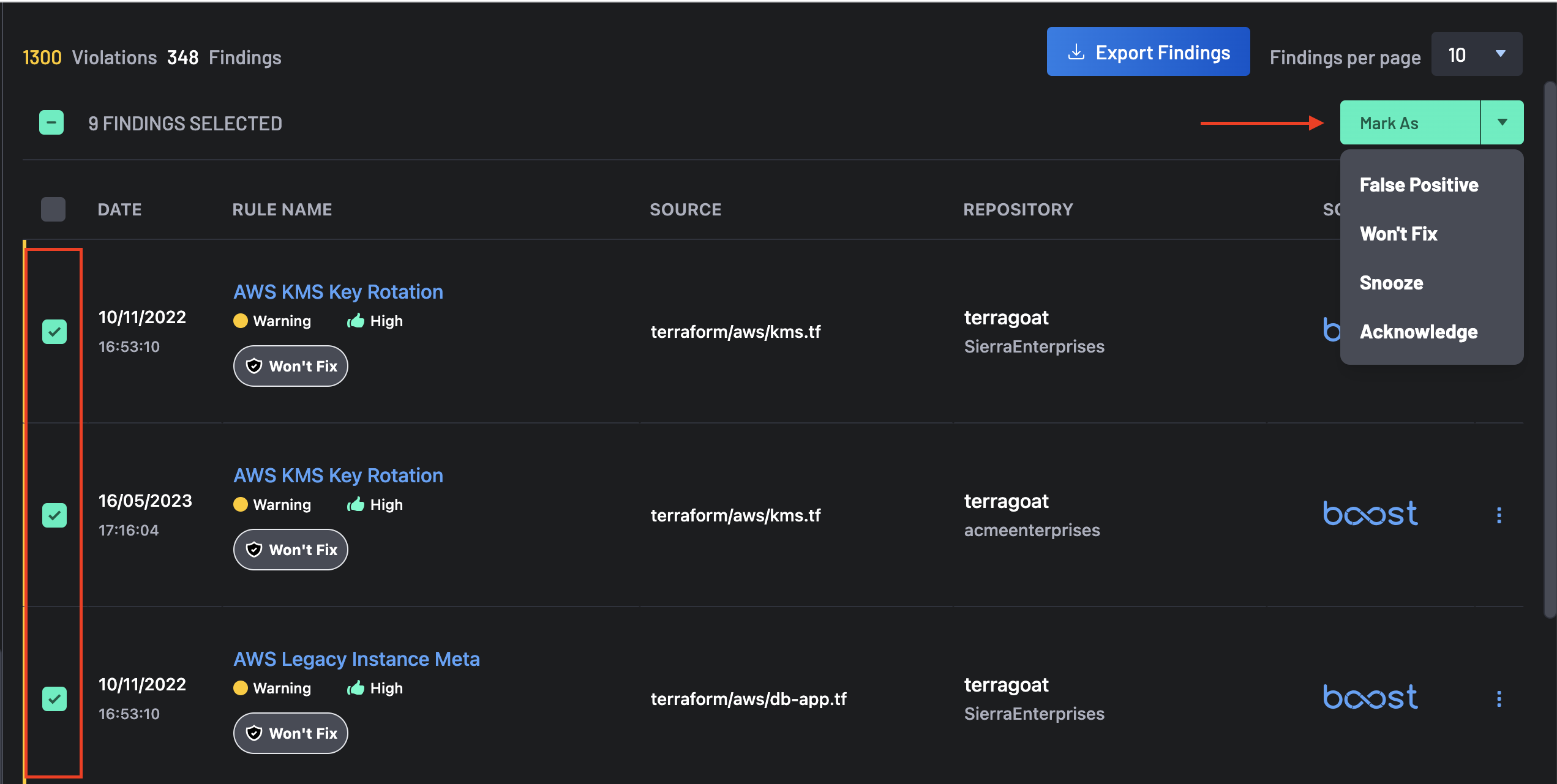
Bulk Selection of Findings¶
Select one or more findings to perform triage actions such as Override, Mark as Verified, or suppress as a False Positive, Won't Fix, or Snooze.
Severity Information¶
This provides information about the potential impact of exploiting a known vulnerability.
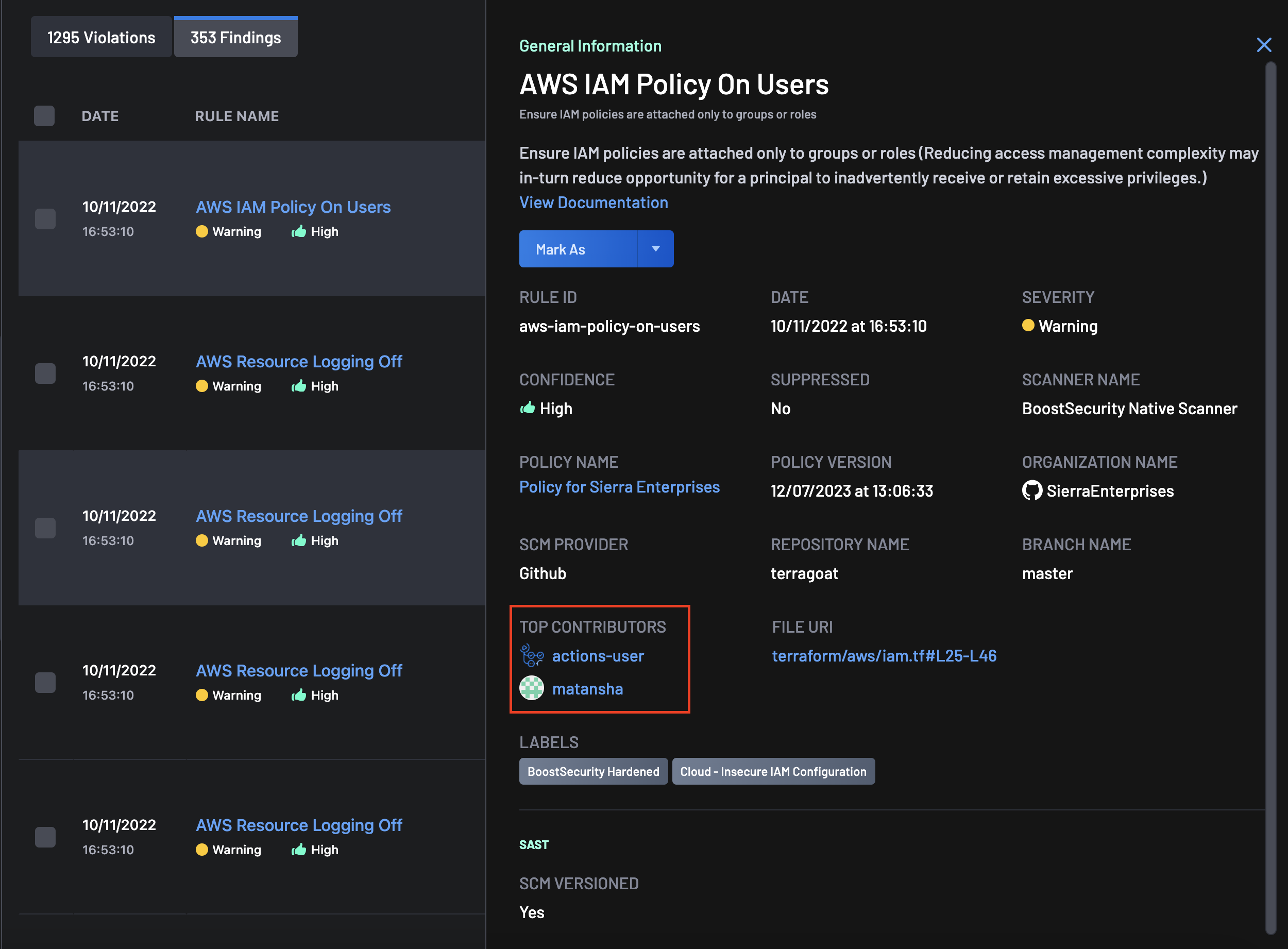
Top Contributors to a Code Repository¶
This feature highlights the leading contributors to a code repository in a Finding. It is supported for GitHub, ADO, BitBucket, and GitLab repositories.
Transitive Dependencies¶
Transitive dependencies occur when security vulnerabilities or issues are detected not directly within the project's code but within the dependencies of a project's codebase, forming a chain of interconnected components.
BoostSecurity analyzes dependencies and their associated vulnerabilities comprehensively. It not only identifies issues within the project's direct dependencies but also uncovers vulnerabilities within transitive dependencies. By flagging these transitive dependencies, BoostSecurity provides an avenue for developers to prioritize and address security issues, thereby ensuring the integrity of applications.
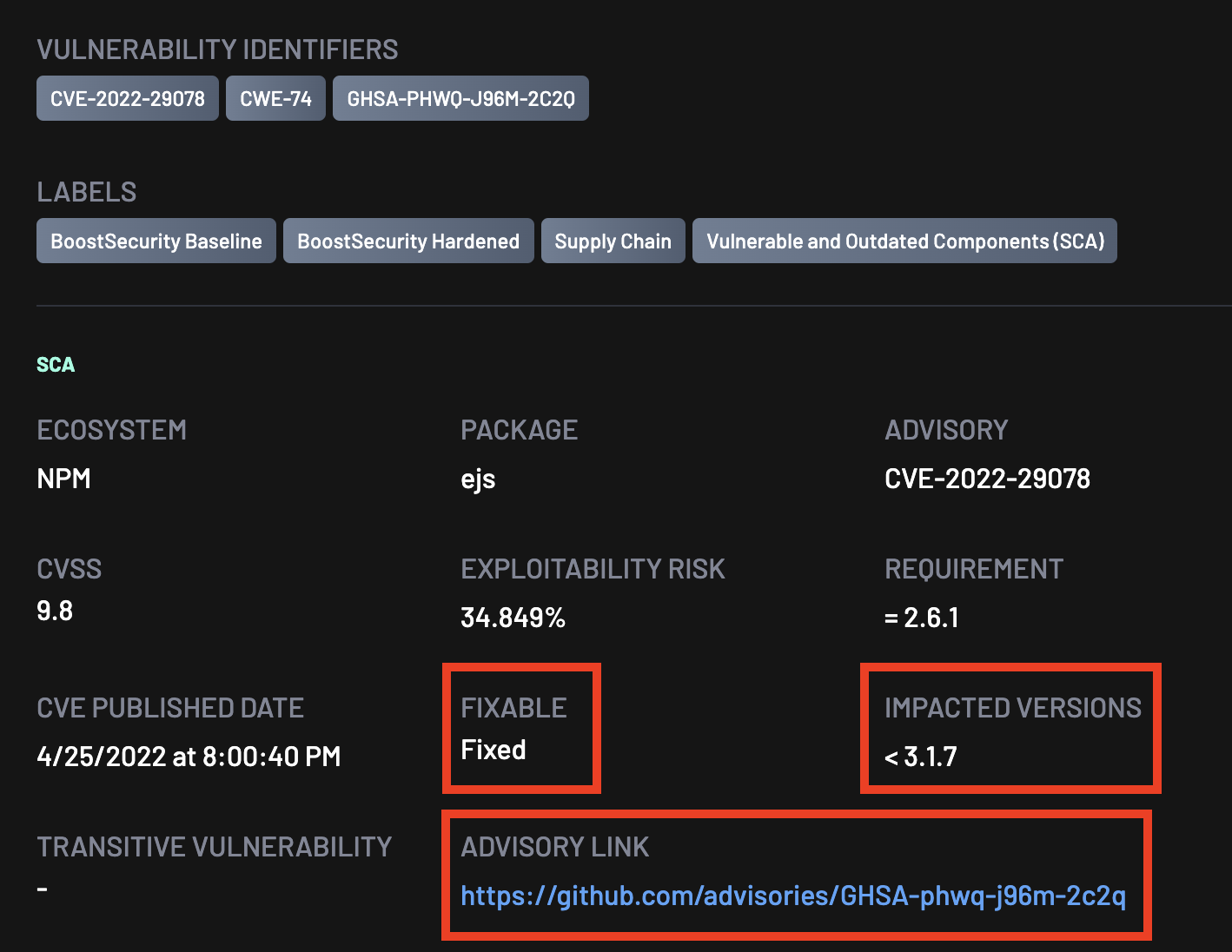
CVE IDs¶
The CVE (Common Vulnerabilities and Exposures) identification for findings directly within the Findings View.
Advisory Links¶
Detailed information about a CVE.