Zero Touch Provisioning for GitHub¶
This guide walks you through the process of setting up Zero Touch Provisioning (ZTP) for GitHub.
Prerequisites¶
Before you begin, make sure:
- You have integrated GitHub with BoostSecurity.
- You have created a
.boostrepository within your organization's SCM, which should contain aREADME.mdfile. - You have access to an account that is Organization owner.
- You have allowed OAuth Apps are authorized for your organization.
1. Integration Steps¶
-
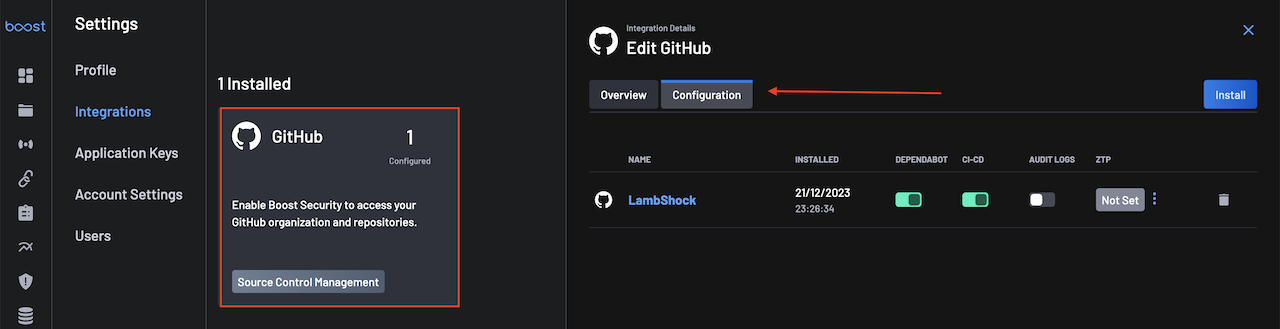
Go to the Integrations page, select your GitHub integration and click on the configuration tab.
-
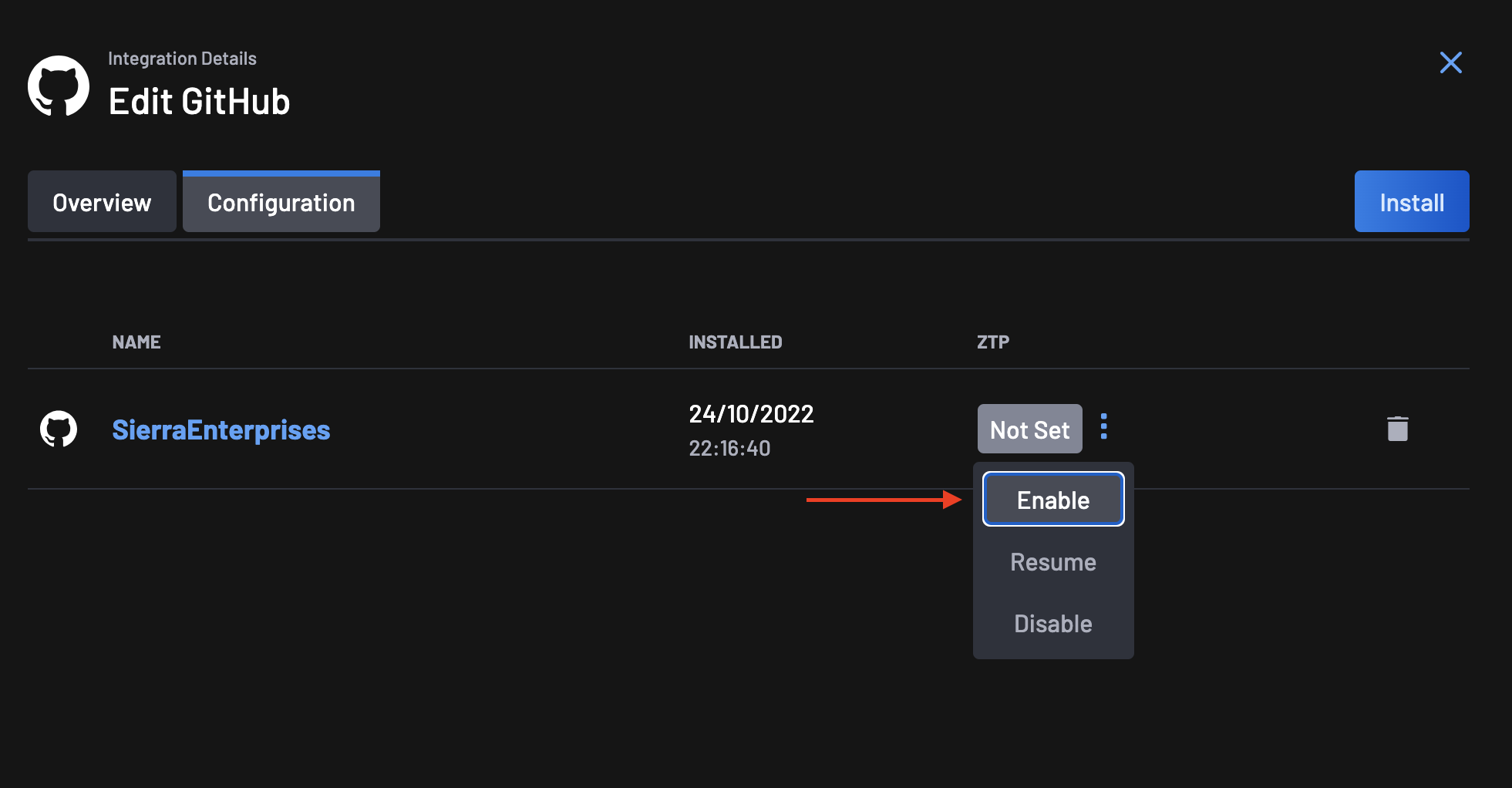
On the ZTP column, you will notice that the ZTP status is set to Not Set. Click on the actions menu next to the status and select Enable.
-
On the ZTP Wizard, the first step is to give BoostSecurity permissions for the Zero Touch Flow on your GitHub Organization.
-
Click the Install ZTP Application button to redirect you to your GitHub organization.
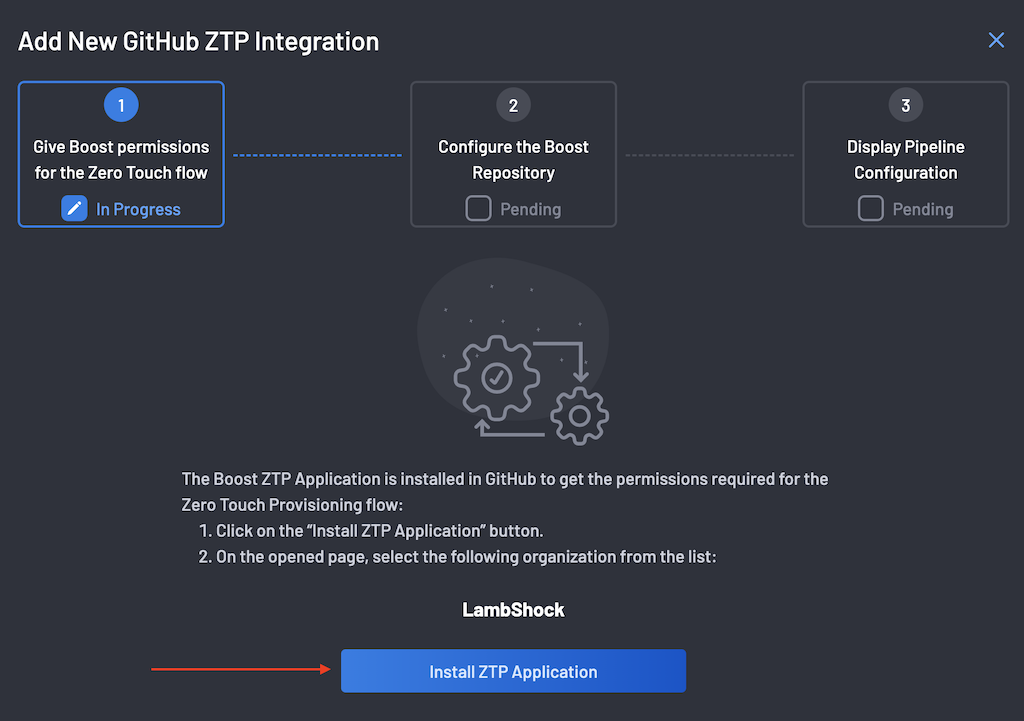
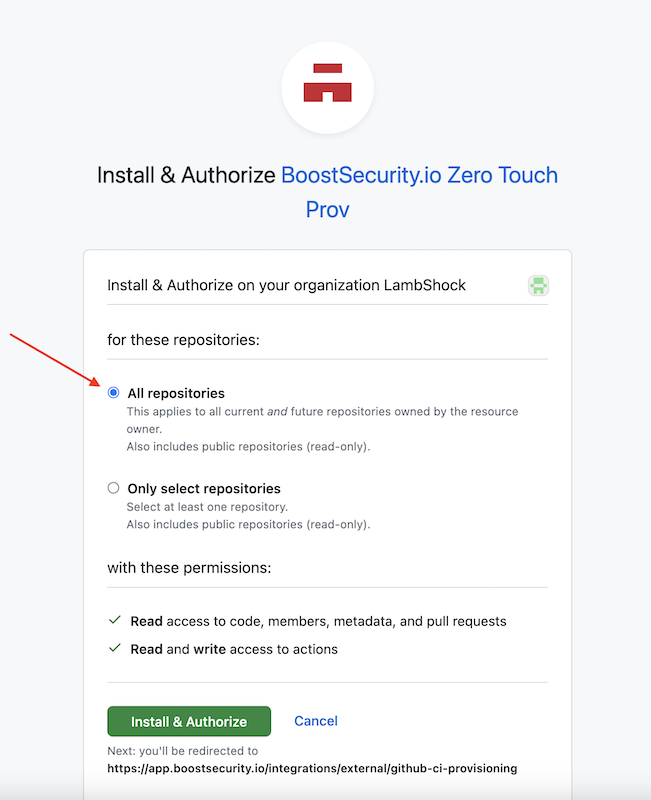
-
As an organization owner, install and authorize the BoostSecurity.io Zero Touch provisioning on all repositories or you could choose which specific repos to install ZTP for. Installing organization-wide only ensures that all repos are covered and configured for ZTP. Click on the Install & Authorize button at the bottom of the page.
-
-
In the ZTP Wizard, the second step is to give BoostSecurity permissions to configure the
.boostrepo.-
As an organization owner, ensure that OAuth Apps are authorized for your organization.
-
Click the Configure the Boost Repository button to redirect you to your GitHub organization.
-
Grant the requested temporary OAuth authorizations to the BoostSecurity CI Provisionning OAuth App for it to perform configuration actions on your behalf.
-
With the granted authorization, the BoostSecurity CI Provisioning OAuth App configures the
.boostrepo.
-
-
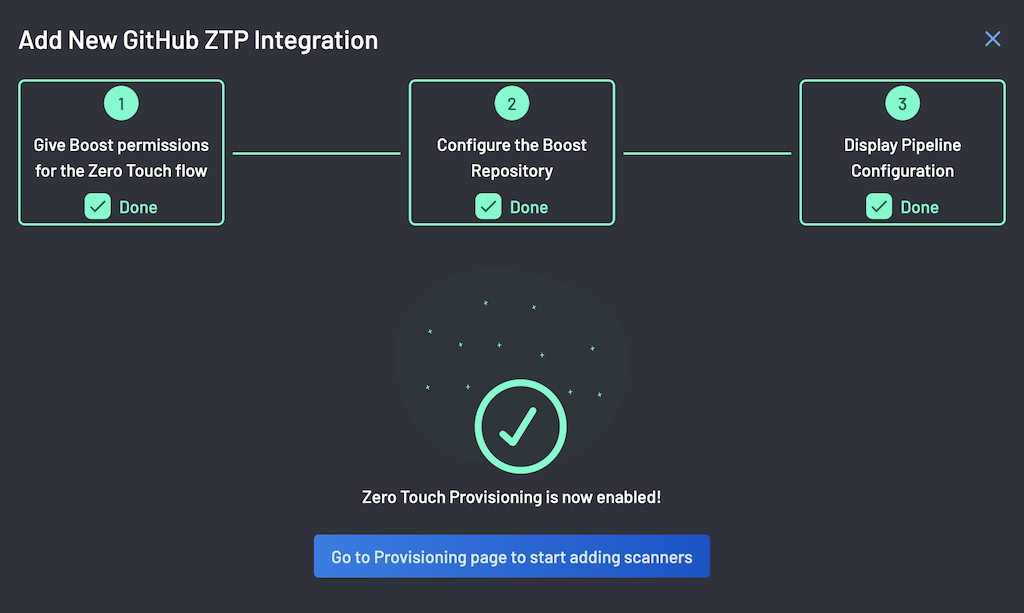
On successful
.boostrepo configuration, the BoostSecurity.io Zero Touch Provisioning installation is completed.Zero Touch Provisioning is now enabled!!!
-
You can now enable one or many scanners.
Security¶
During the zero touch provisioning setup, you are required to grant authorization to the BoostSecurity CI Provisioning OAuth App. With the authorization, this app performs actions on your behalf to complete the configuration of the .boost repo. This section provides more insights on the security and safeguards of this step.
-
Temporary Authorizations:
The requested authorizations are only required at installation to configure the
.boostrepository. Once completed, BoostSecurity destroys the OAuth access token. For added security, one could explicitly revoke the BoostSecurity CI Provisioning OAuth App by navigating to GitHub Settings → Applications → Authorized OAuth Apps. -
Auditable Actions:
The actions performed by the BoostSecurity CI Provisioning OAuth App are fully auditable in GitHub Security Log.
Alternate Procedure¶
For convenience, the above procedure, step (4.b) is performed as an organization owner. We understand that even with the safeguards present in the Security section, some organizations might not be comfortable granting the BoostSecurity CI Provisioning OAuth App authorization as an organization owner. Alternatively, this step could be performed using a low privilege organization member account.
If you decide to proceed with this alternate procedure, as an additional prerequisite, you will be required to:
- Have access to an Organization member account with push permission to the
.boostrepository.
Then after you have executed step (4.a), perform the following:
- Log out as an organization owner from GitHub.
- Login to GitHub as an organization member with push permissions to the
.boostrepository. - Proceed with step (4.b) as above while acting as the organization member with low privileges.