Software Bill Of Materials (SBOM)¶
A Software Bill of Materials (SBOM) is a formal record that lists all components such as libraries, packages, and dependencies contained within a given software artifact. It is the software equivalent of a manufacturing parts list, detailing what makes up your application. Having a reliable SBOM helps development and security teams to:
- Identify components at risk due to known vulnerabilities.
- Understand licensing obligations and risks.
- Respond faster during zero-day or supply chain attacks.
- Comply with regulatory or organizational requirements.
BoostSecurity provides a powerful SBOM management and visualization platform that goes far beyond static inventory tracking. With Boost's SBOM service, you get:
- A centralized view of components across all your repositories and container images.
- Real-time vulnerability enrichment, including CVEs, EPSS scores, CVSS v3.1 severity, and malware detection.
- Deep dependency analysis, including transitive and indirect dependencies.
- Insightful filters and search tools to pinpoint at-risk packages, projects, or configurations.
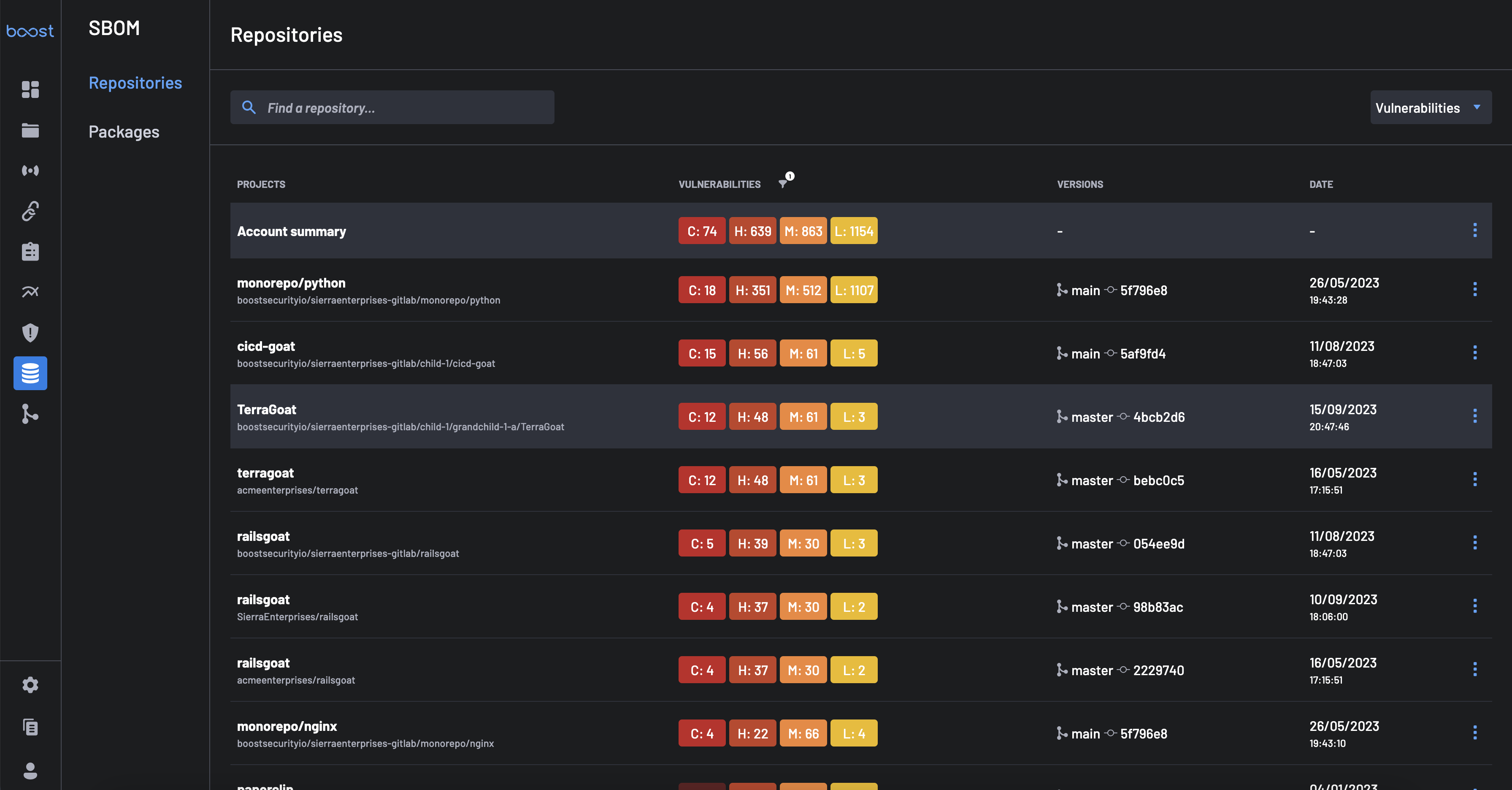
To access the SBOM service, select SBOM from the BoostSecurity dashboard sidebar. The main SBOM view displays project-specific vulnerability details and an account-wide summary of all detected vulnerabilities.
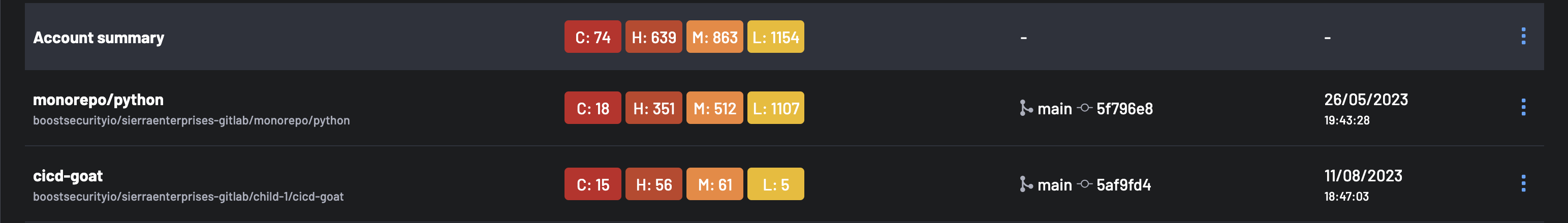
Account Summary¶
The Account Summary section displays the total number of vulnerabilities across all projects and components in your account, organized by severity level. From here, you can download a complete SBOM document in CycloneDX, SPDX, or CSV format, which contains an inventory of all components across all projects in your account.
Projects Specific Summary¶
The projects summary section provides a project-based posture, providing a summary of the number of vulnerabilities:
- Per severity level
- Per project for all projects in the account
The projects are presented in descending order of vulnerability severities.
Info
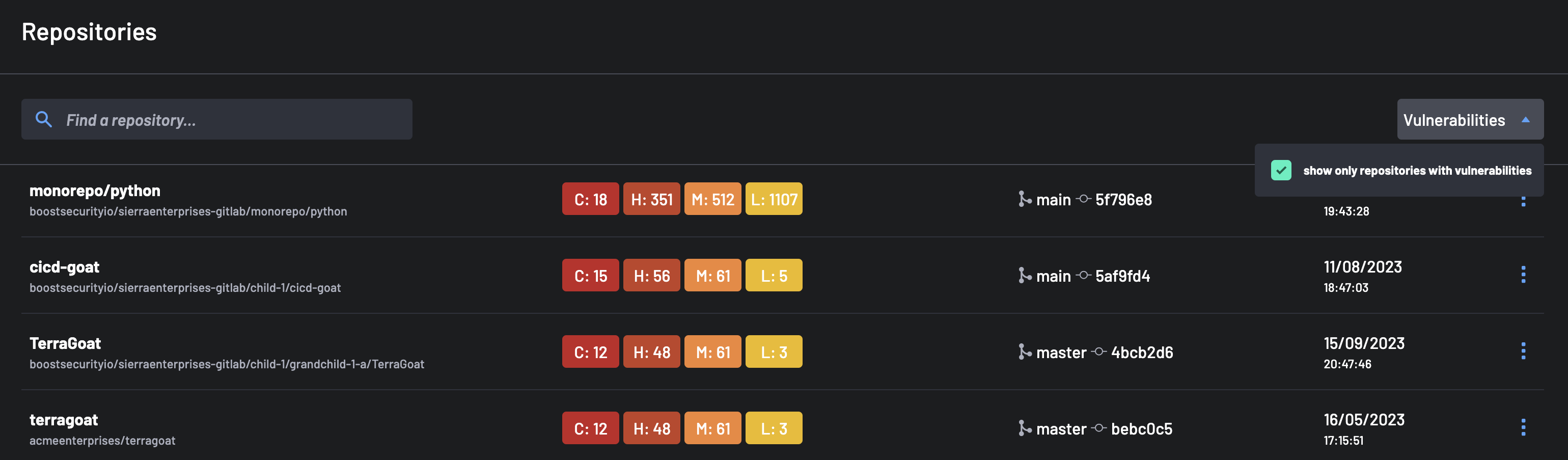
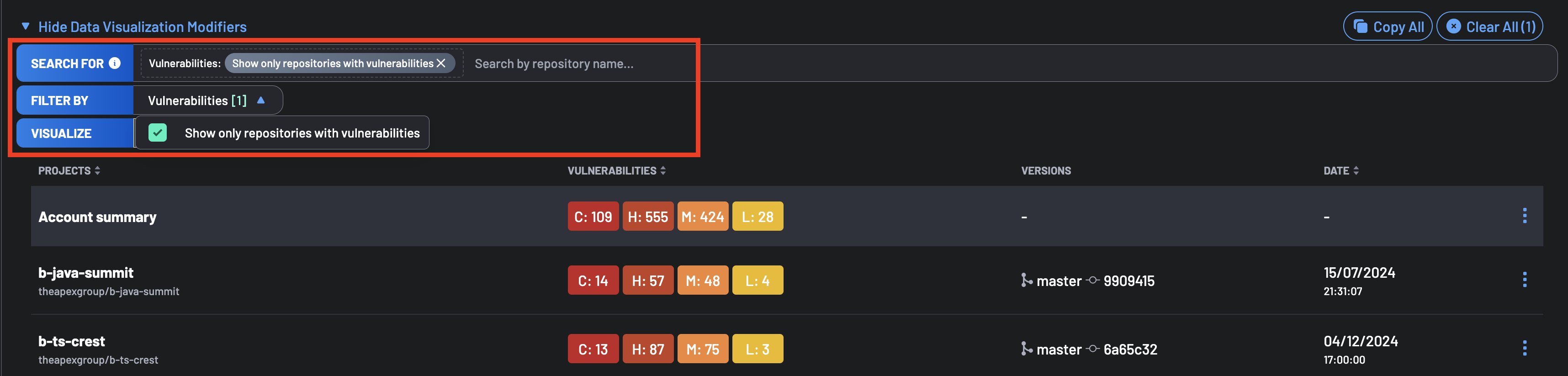
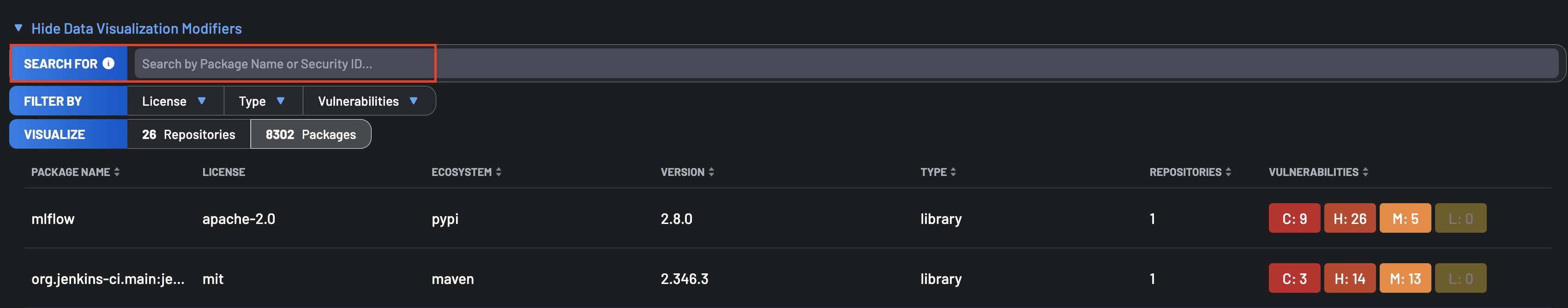
The Search For filter allows you to search for projects by name across all projects in your account. Additionally, you can utilize the Filter By option to narrow down repositories based on their License, Type, Vulnerabilities, or any custom Manual Tag assigned to the repositories.
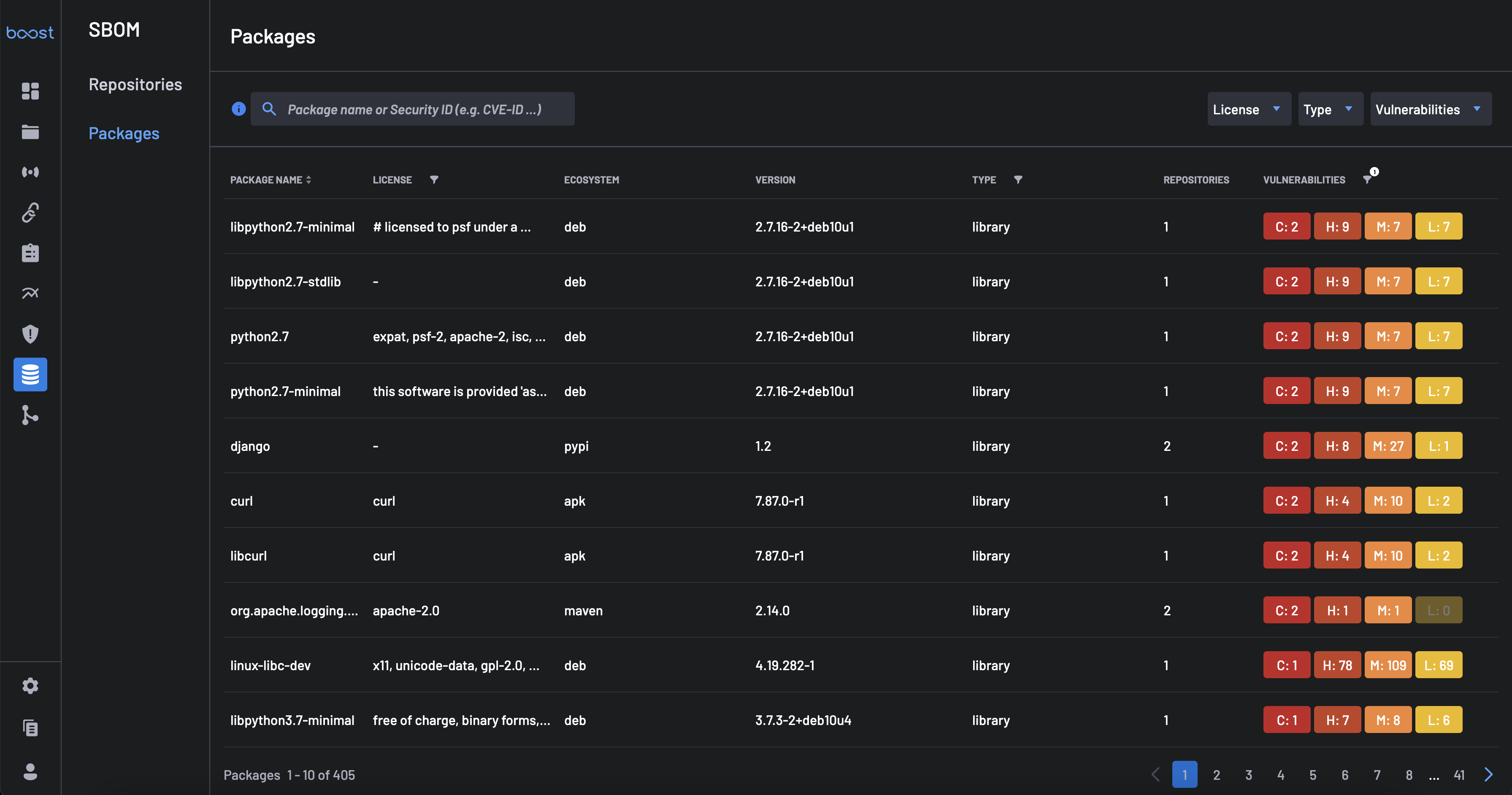
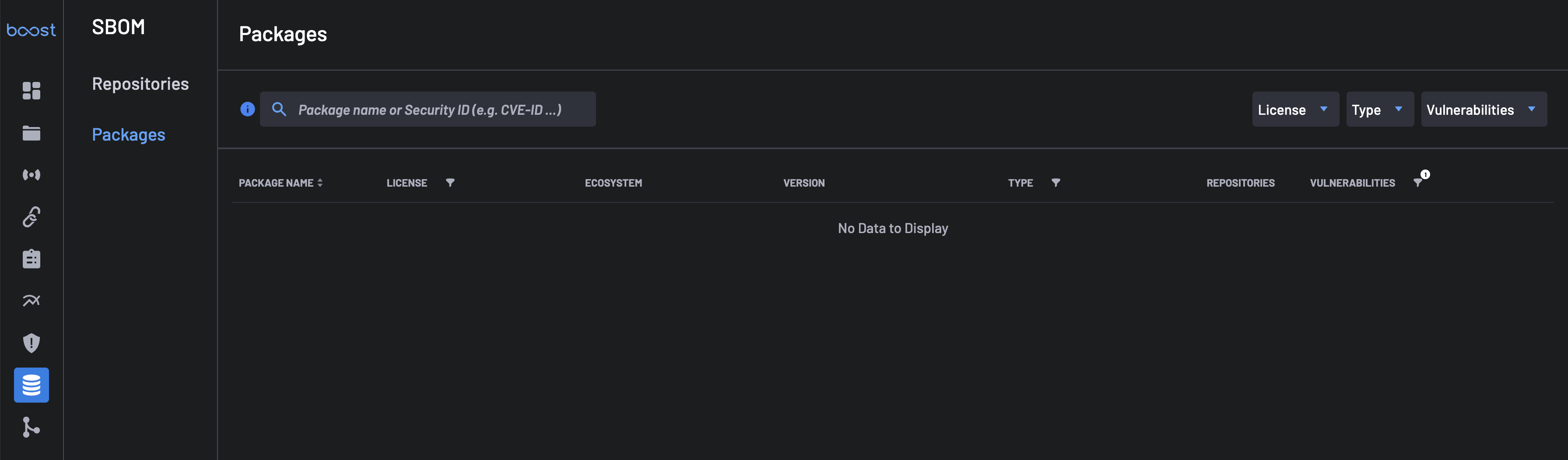
Packages¶
By selecting the Packages tab in the Visualize filter, Boost provides a quick way to find all packages and third-party components included across all projects in the account.
The packages are presented in decreasing order of number and severity of vulnerabilities. For each package, the following are provided:
- The number and severity of vulnerabilities.
- The number of repositories in the account, including the package.
Note
The search area can be used to search for a package by Package Name or Security Id. The filter by option allows you to filter by License, Type, Vulnerabilities, or custom Manual Tags.
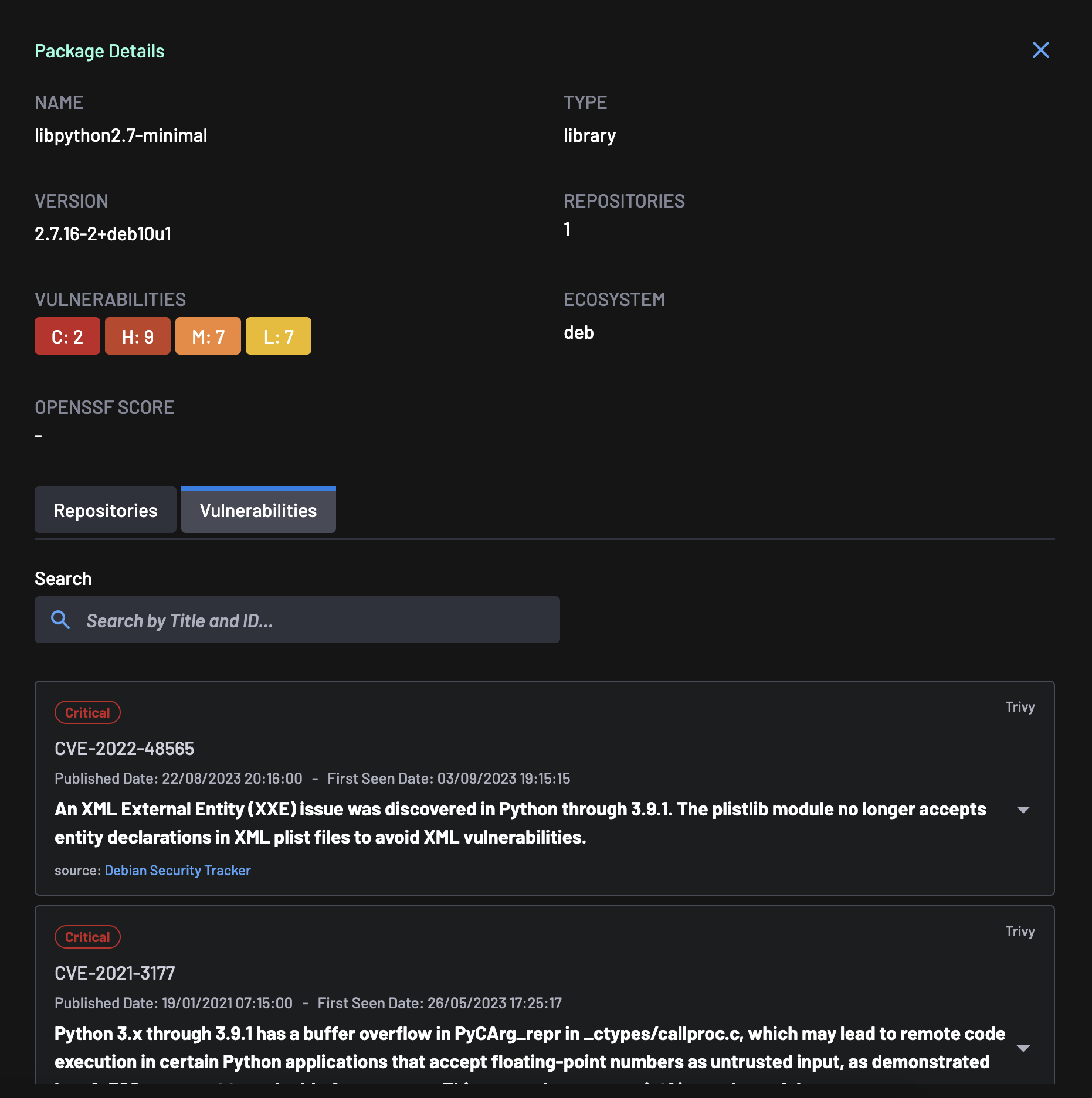
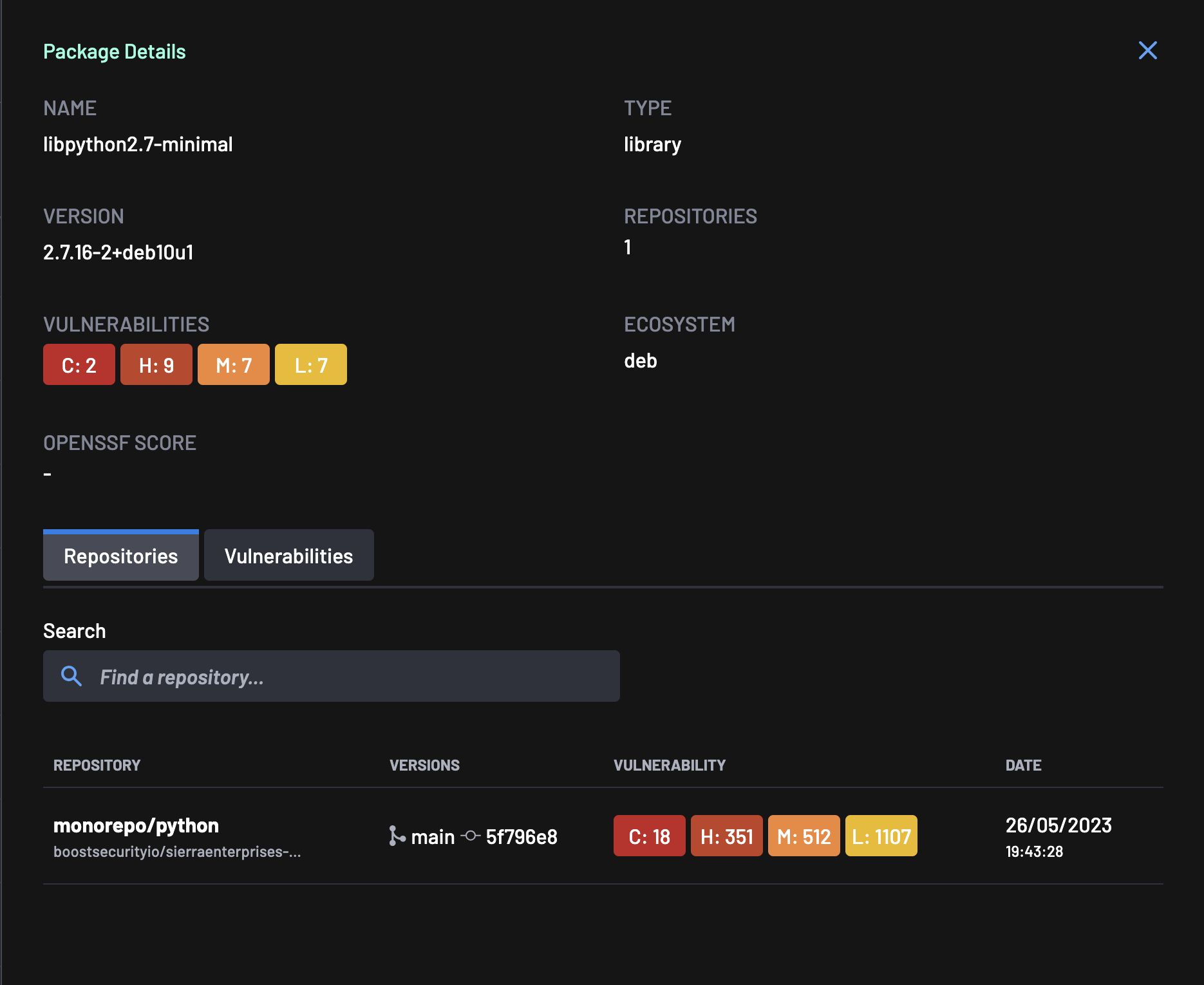
Package Details¶
Select a package from the list of packages to view further details. These details include:
- Package Name
- License
- Ecosystem
- Version
- Type
- Repositories
- Vulnerailities
Vulnerabilities¶
The vulnerability details for each package can be viewed by selecting the Vulnerabilities tab. The list of vulnerabilities is presented, including the
- Vulnerability ID
- Package Name
- Severity
- Advisories
- Source
- Description
- CVSS v3.1 Score
- EPSS Score
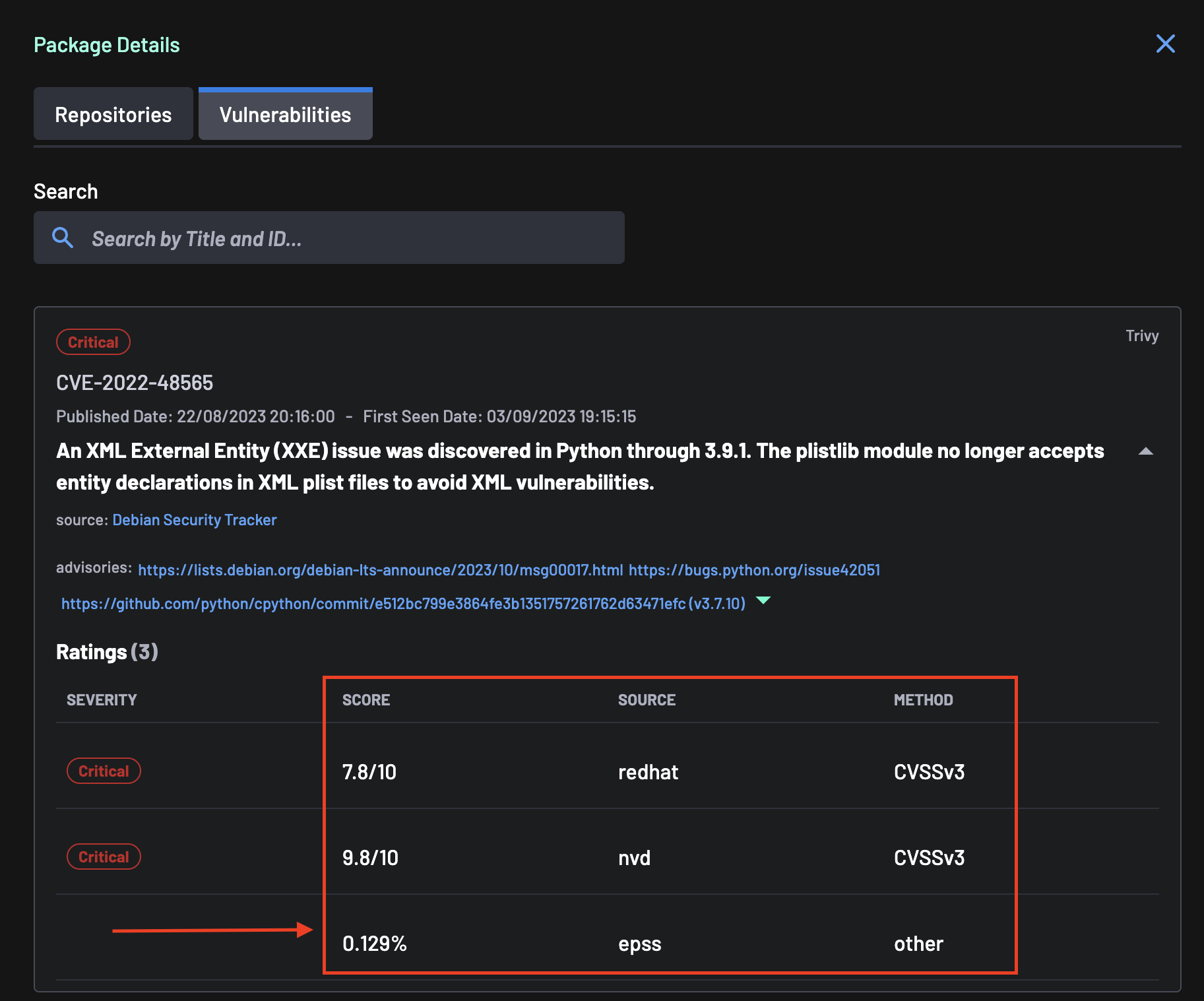
CVSS 3.1 and EPSS Score¶
The CVSS and EPSS scores can be viewed by clicking on a vulnerability listed in the Vulnerabilities tab.
The vulnerabilities details view can be exited with "Esc" or by clicking the close (x) button.
Repositories¶
Select the Repositories tab to view the list of repositories.
The project link can be selected from the list of projects, taking the user to the project-specific view.
No Packages Found¶
If results are not found based on selected filters, you will be notified that no vulnerable packages meet the criteria.
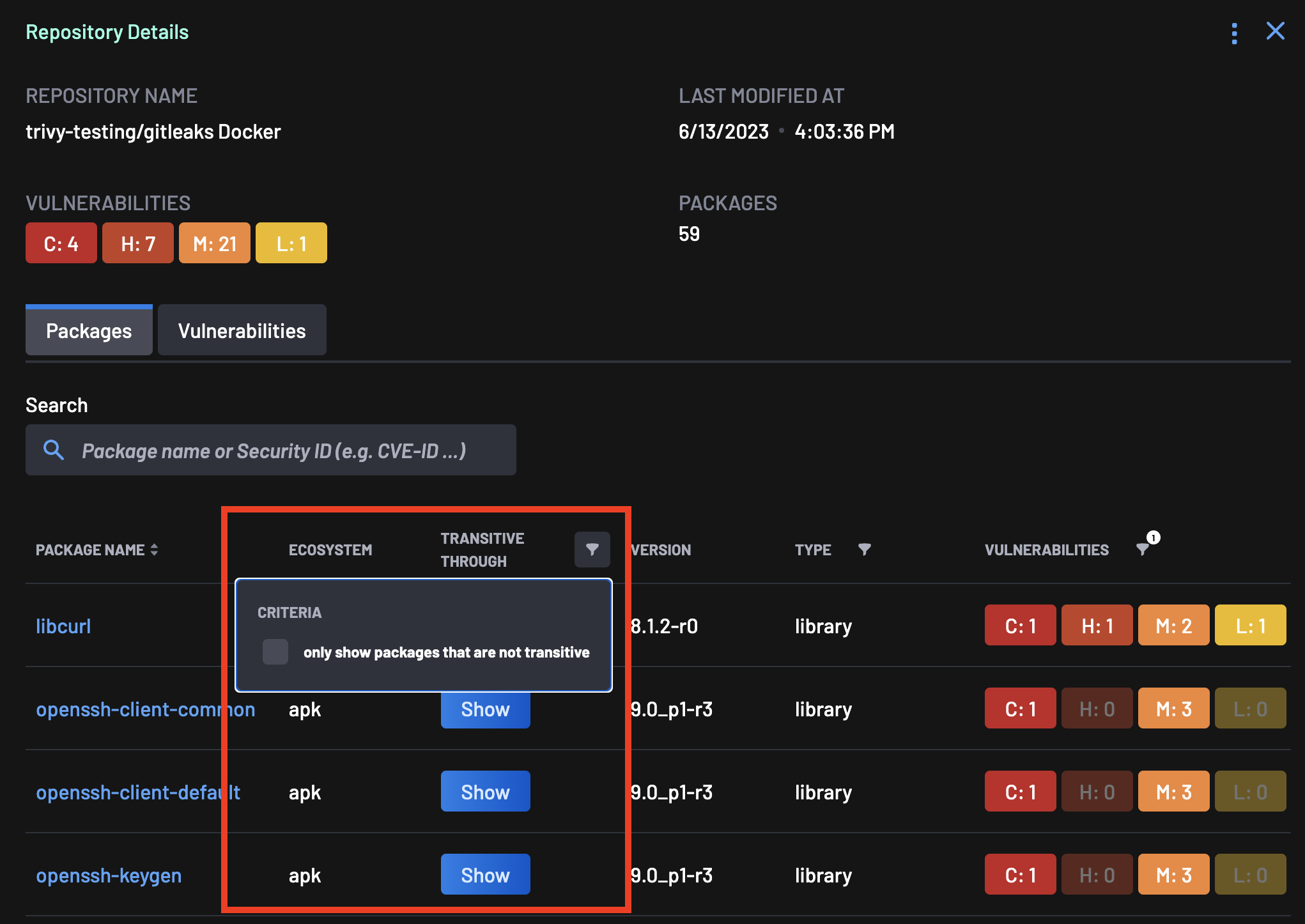
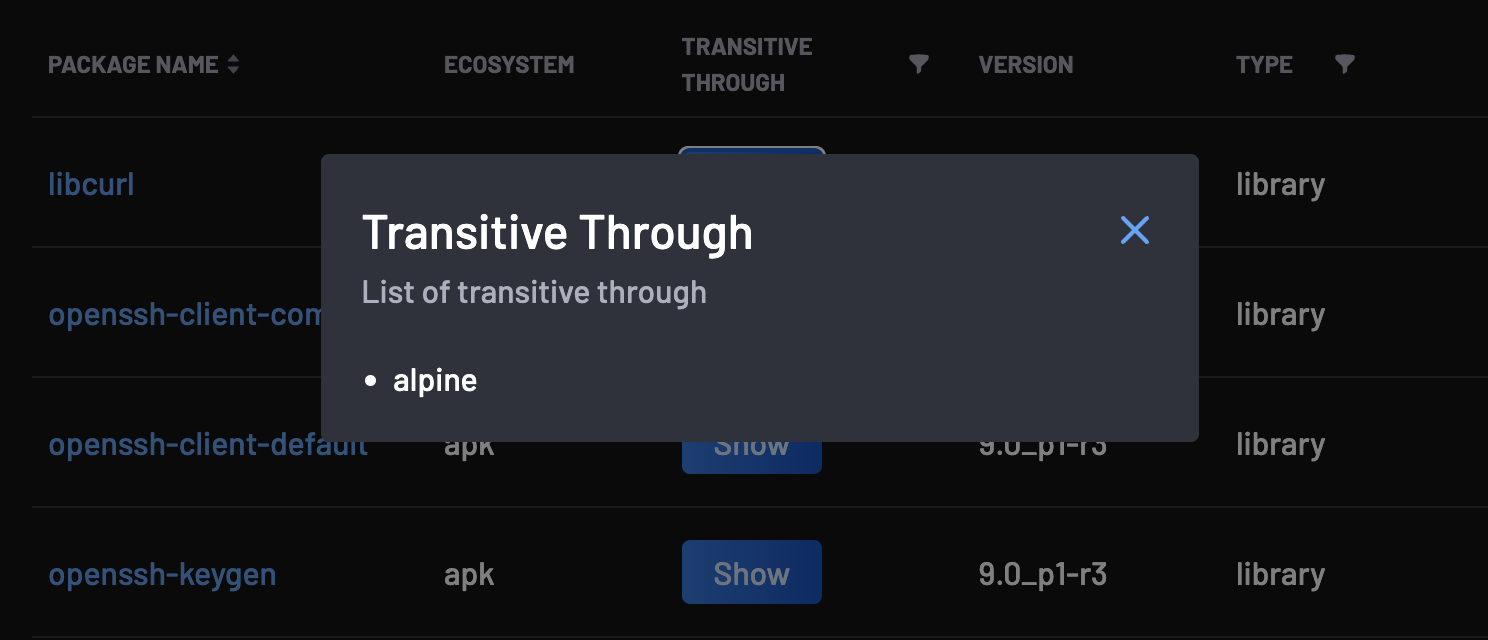
Transitive Dependencies¶
Transitive dependencies occur when security vulnerabilities or issues are detected not directly within the project's code but within the dependencies of a project's codebase, forming a chain of interconnected components.
BoostSecurity analyzes dependencies and their associated vulnerabilities comprehensively. It not only identifies issues within the project's direct dependencies but also uncovers vulnerabilities within transitive dependencies. By flagging these transitive dependencies, BoostSecurity provides an avenue for developers to prioritize and address security issues, thereby ensuring the integrity of applications.
Patch recommendations¶
For each library vulnerability, we display a link to the library's vulnerability details page. This page contains a list of all the library versions affected by the vulnerability. If a patch is available, it will specify the library version containing the fix.
Data Update Cycle¶
Data sources are regularly refreshed to ensure the most up-to-date information is available for analysis and decision-making. Updates occur every 12 hours, maintaining the accuracy and relevance of the data provided to users.