Compliance¶
The Compliance page in BoostSecurity offers a centralized interface to monitor and manage compliance across various assets and repositories. It enables users to assess their adherence to critical security standards and frameworks by tracking specific compliance controls across different resource groups. This page is especially beneficial for organizations seeking to maintain or improve their security posture by ensuring that code repositories and associated workflows follow industry best practices.
Key Features of the Compliance Page¶
1. Resource Management¶
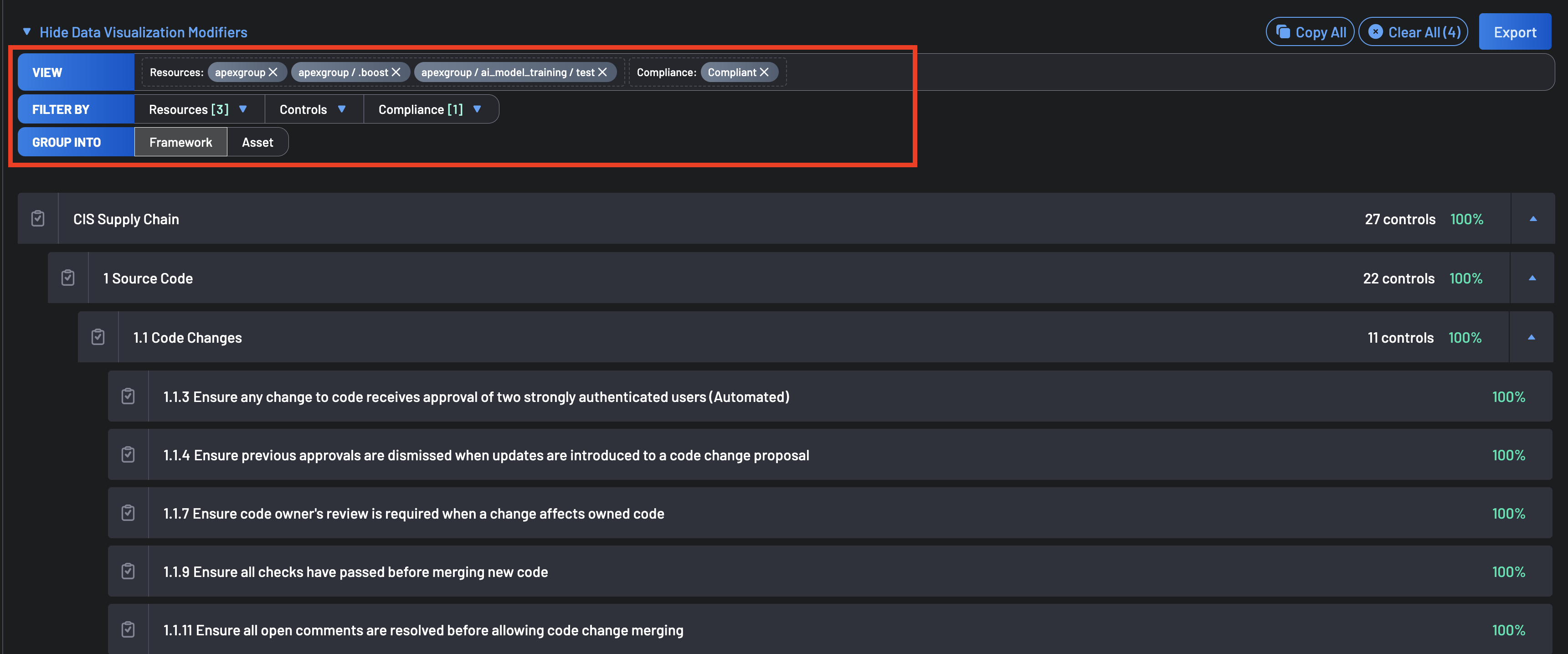
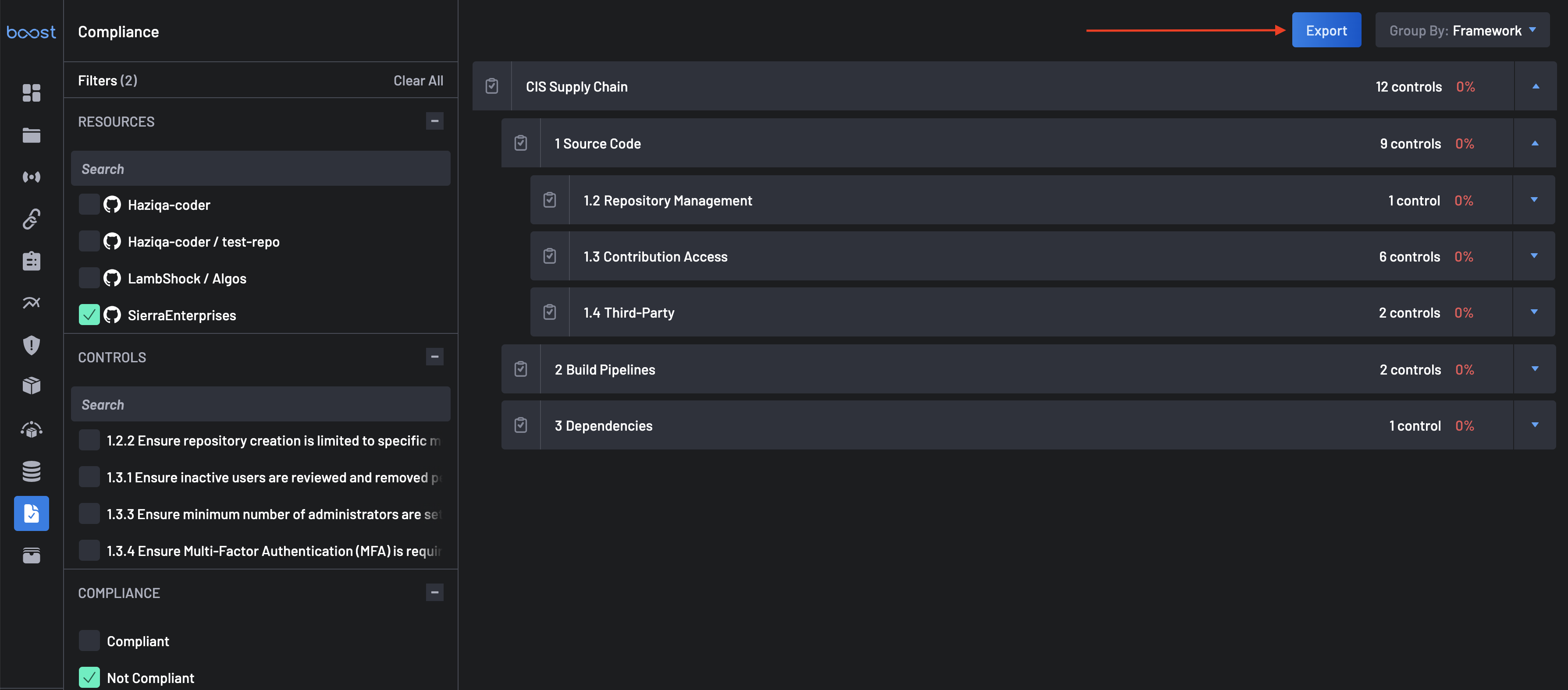
On the top of the page, the filter panel lists all available filters to refine your search across connected repositories and projects, allowing users to select or multi-select and focus on specific resources. Each resource represents a project or repository where compliance checks are applied.
- Filter By: Users can quickly filter results by Resources, Controls, Compliance, or Manual Tag within the list.
- Group Into: Users can group results into Framework or Assest, enabling a more targeted compliance assessment.
- View: The View filter tab shows all the applied filters to users.
2. Control Monitoring¶
The Controls panel provides a searchable list of individual security controls. These controls are derived from compliance frameworks and represent specific security measures or requirements that should be enforced in the code and repository management processes. Examples of these controls include:
- Code Tracking: Ensuring changes to code are tracked in a version control platform.
- Approval Mechanisms: Requiring code changes to receive approval from authenticated users.
- Repository Access: Restricting repository creation, deletion, and access to authorized members only.
Each control is linked to a unique identifier (e.g., 1.1.1, 1.1.2) and can be individually searched or selected for review. The Unknown and 0% labels indicate compliance status, providing users with immediate insight into areas that may need attention.
3. Export Compliance Report¶
The Export button, located at the top right of the Compliance page, allows users to download compliance data for further analysis or reporting. This feature is useful for organizations that need to:
- Share compliance reports with security teams or stakeholders.
- Track compliance changes over time.
- Perform offline reviews or integrate compliance data with other security monitoring tools.
Users can click the Export button to generate a structured report that aligns with user-selected filters, summarizing compliance status across all selected resources and controls.
4. Compliance Frameworks¶
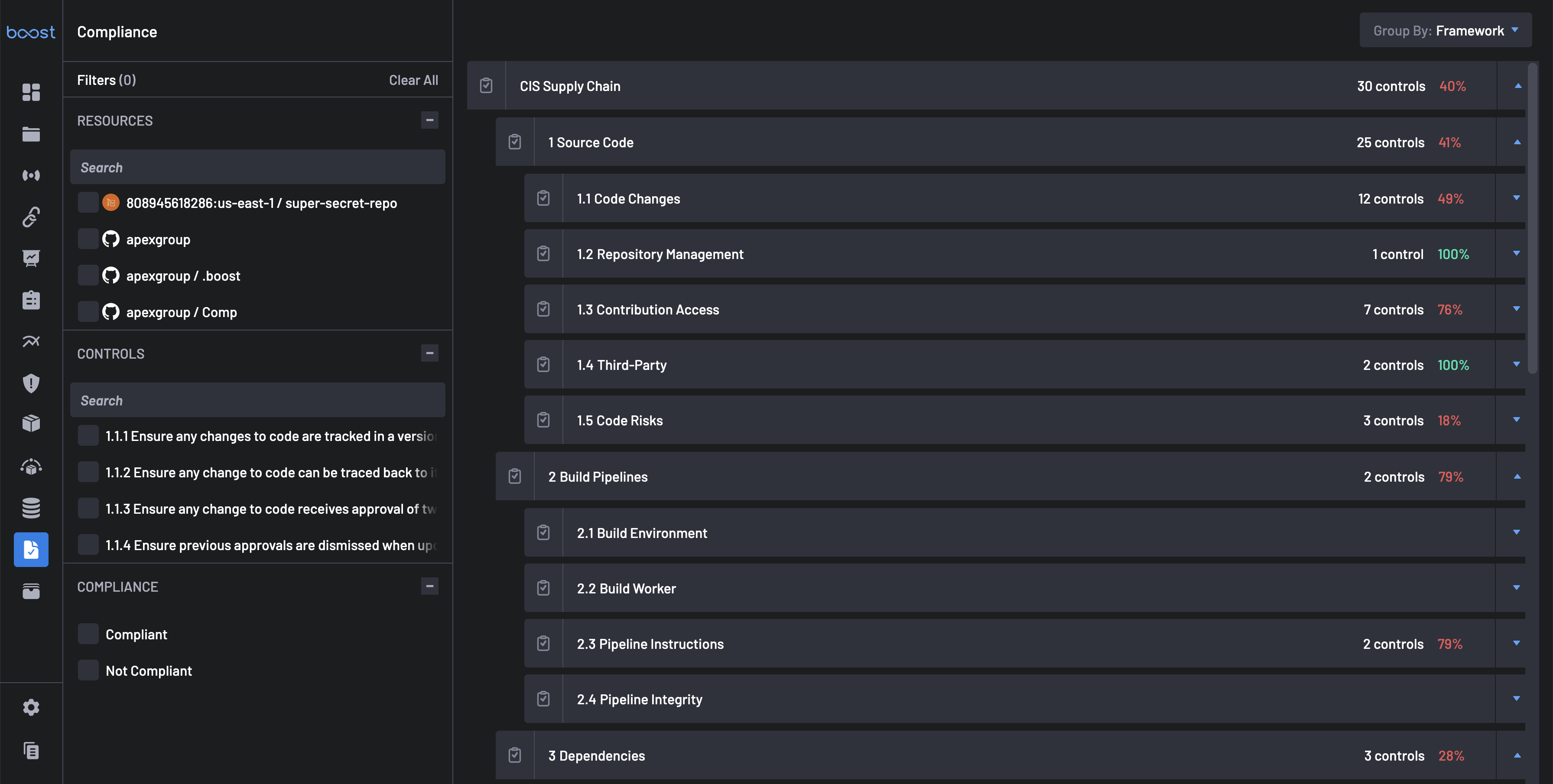
The right-hand panel displays a hierarchical view of the compliance frameworks, such as the CIS Supply Chain framework, broken down into categories and individual controls. Each category represents a specific area of the development and deployment process, with individual controls that define security best practices for that area. The categories include:
-
Source Code: This section focuses on secure practices for managing and tracking code changes to ensure integrity and accountability within the source code repository. An example of a control in this category is:
- Code Changes: Ensuring changes to the code are tracked in a version control system, verified by authenticated users, and reviewed before merging.
-
Build Pipelines: This category centers on the security of the automated processes that compile and package the code into executable artifacts. It ensures that the build process itself is secure and resistant to tampering. An example of a control in this category is:
- Pipeline Integrity: Verifying that only trusted and authenticated sources can trigger builds.
-
Dependencies: This section addresses the security of third-party libraries and dependencies that the project relies on. Ensuring these dependencies are secure and up-to-date is essential to avoid vulnerabilities in external code.
-
Artifacts: This category is concerned with managing the security of artifacts produced by the build pipeline, such as binaries, containers, or other packaged files. It ensures that artifacts are stored securely and are verifiable, preventing the introduction of compromised versions. Controls include:
- Verification: Ensuring that artifacts are digitally signed or hashed so they can be verified before deployment.
-
Deployment: This category focuses on securely deploying code and artifacts to production environments. It covers the practices and controls necessary to ensure that only verified code is deployed and that deployment activities are logged and monitored.
Each category is expandable, revealing specific controls that define the security requirements or best practices. Compliance percentage scores (e.g., "0%") provide a visual summary of compliance within each category.
5. Control Details and Compliance Status¶
For each control within a category, a description outlines the security requirement. Each control shows its compliance status:
- Unknown: Indicates that the status of the control is yet to be determined.
- 0%: Shows that the control is currently not compliant with the set requirement.
Each control includes specific language, such as "Ensure any changes to code are tracked in a version control platform" or "Ensure repository deletion is limited to specific users." This language is intended to help users understand what is required to achieve compliance for each control.
Warning
If you have drop all anywhere in your policy, compliance is always 0 for affected assets.
Usage Summary¶
The Compliance page provides a structured approach to viewing and enforcing compliance across your organization's assets. By tracking specific controls against resources and leveraging frameworks such as CIS Supply Chain, users can ensure that code repositories and workflows adhere to security best practices. This page supports organizations in maintaining a robust security posture and helps prioritize security efforts by highlighting non-compliant areas.