Webhook Misconfiguration Detected¶
This rule detects when a required webhook is missing or has been disabled for an organization or project. Webhooks play a critical role in triggering automated security scans and workflows whenever code is pushed to a repository. Without them, new commits may bypass security checks, allowing vulnerabilities to slip into the codebase undetected.
Such misconfigurations may be accidental, due to changes in settings or permissions, or intentional—done by a malicious actor to avoid detection. Investigating and restoring proper webhook functionality is necessary to maintain the integrity of the CI/CD pipeline and overall software supply chain.
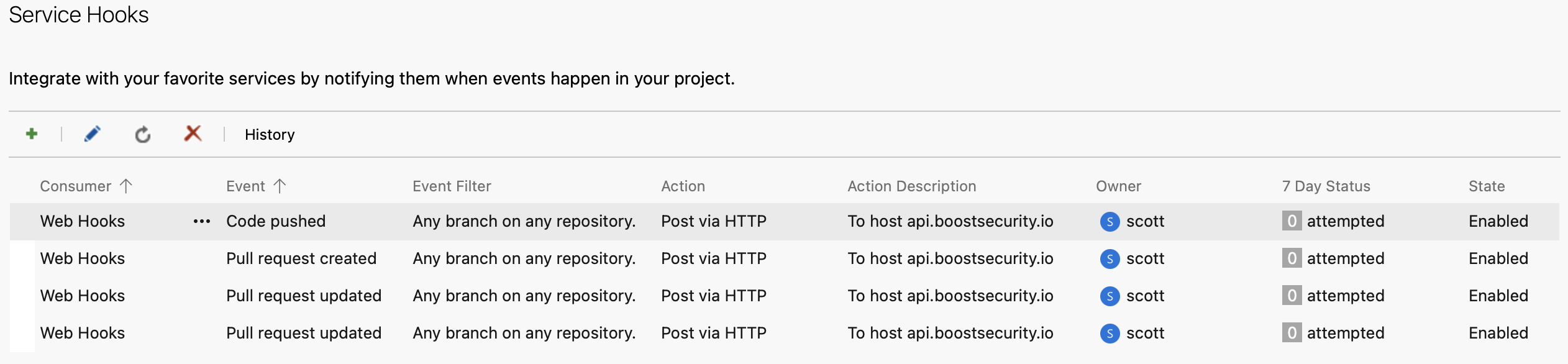
Figure 1: Expected state – all security-related webhooks are present and enabled.
Why This Matters¶
- Security Gaps: Without functioning webhooks, security scanners or other automation tools (like CI/CD pipelines) may not run, creating blind spots.
- Governance Failure: Disabled webhooks can signal weak controls over the development workflow.
- Potential Malicious Behavior: Disabling webhooks may be a deliberate attempt to prevent security tooling from catching vulnerabilities or malware introduced into code.
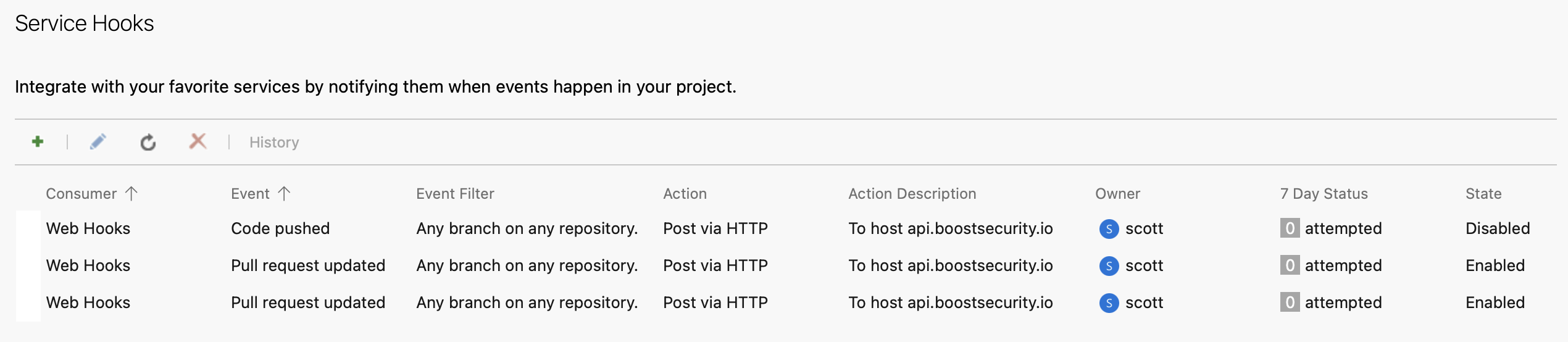
Figure 2: Webhook misconfiguration detected – one missing and one disabled.
Mitigation Steps¶
- Review webhook settings in your SCM provider (e.g., GitHub, GitLab, Bitbucket) to ensure required webhooks are properly configured.
- Re-enable any disabled security-related webhooks.
- Verify webhook delivery history to identify when issues began and correlate with commit history.
- Restrict permissions around webhook configuration to trusted roles only.
- Set up monitoring to alert when critical webhooks are removed or disabled.
- Audit recent commits for suspicious activity or unscanned changes while the webhook was disabled.