Dynatrace Integration with BoostSecurity¶
The Dynatrace integration with BoostSecurity enables joint customers to enhance security visibility and risk prioritization by combining runtime and development-time security insights. This integration links vulnerabilities detected at runtime with their source code context, improving triage, remediation, and security policy enforcement. Existing security results from the Dynatrace tenant are continuously imported for processing through BoostSecurity policies.
Benefits of the Integration¶
- Code-to-Cloud Mapping: Links runtime security insights from Dynatrace with BoostSecurity’s development-time context, providing a complete security view.
- Enriched Security Context: BoostSecurity ingests runtime data from Dynatrace, enriching its analysis with Kubernetes cluster details, internet reachability, and runtime vulnerability exposure.
- Improved Prioritization: Surfaces critical risks by combining runtime threat intelligence with development security data.
- Context-Aware Security Policies: BoostSecurity’s policy engine incorporates runtime data, enabling precise security controls in the development pipeline.
Prerequisites¶
Before enabling the Dynatrace integration, ensure the following:
- BoostSecurity Account: Access to your BoostSecurity workspace.
- Dynatrace Account: Administrator privileges in Dynatrace.
- Dynatrace Application Security: Must be enabled in Dynatrace.
Dynatrace API Application Setup¶
Before installing the integration, you need to set up an API application in Dynatrace.
- Create a new application in Dynatrace to obtain a Client ID and Client Secret. See Dynatrace documentation.
- Assign the following permissions to your Dynatrace application:
storage:events:readstorage:entities:readstorage:buckets:read
-
Retrieve your Environment ID: it is the first subdomain of your Dynatrace URL, e.g.
https://{ENVID}.apps.dynatrace.com/ -
Retrieve your Account ID from the
JSONbody returned by the SSO token endpoint (Refer to step 1 in the Dynatrace documentation). -
Validate your credentials by requesting an OAuth token. A successful response (HTTP 200) means your client has the right permissions; (HTTP 400) indicates you’re missing one or more scopes:
curl --request POST 'https://sso.dynatrace.com/sso/oauth2/token' \ --header 'Content-Type: application/x-www-form-urlencoded' \ --data-urlencode 'grant_type=client_credentials' \ --data-urlencode 'client_id={CLIENT_ID}' \ --data-urlencode 'client_secret={CLIENT_SECRET}'
If you receive HTTP 200, you’re all set. If you receive HTTP 400, double‑check that the three storage scopes are granted.
Enable the Integration¶
Setting up the Dynatrace integration is quick and straightforward:
Step 1: Turn on the Integration¶
- Navigate to BoostSecurity > Settings > Integrations.
-
Locate the Dynatrace integration tile and click the Install button.
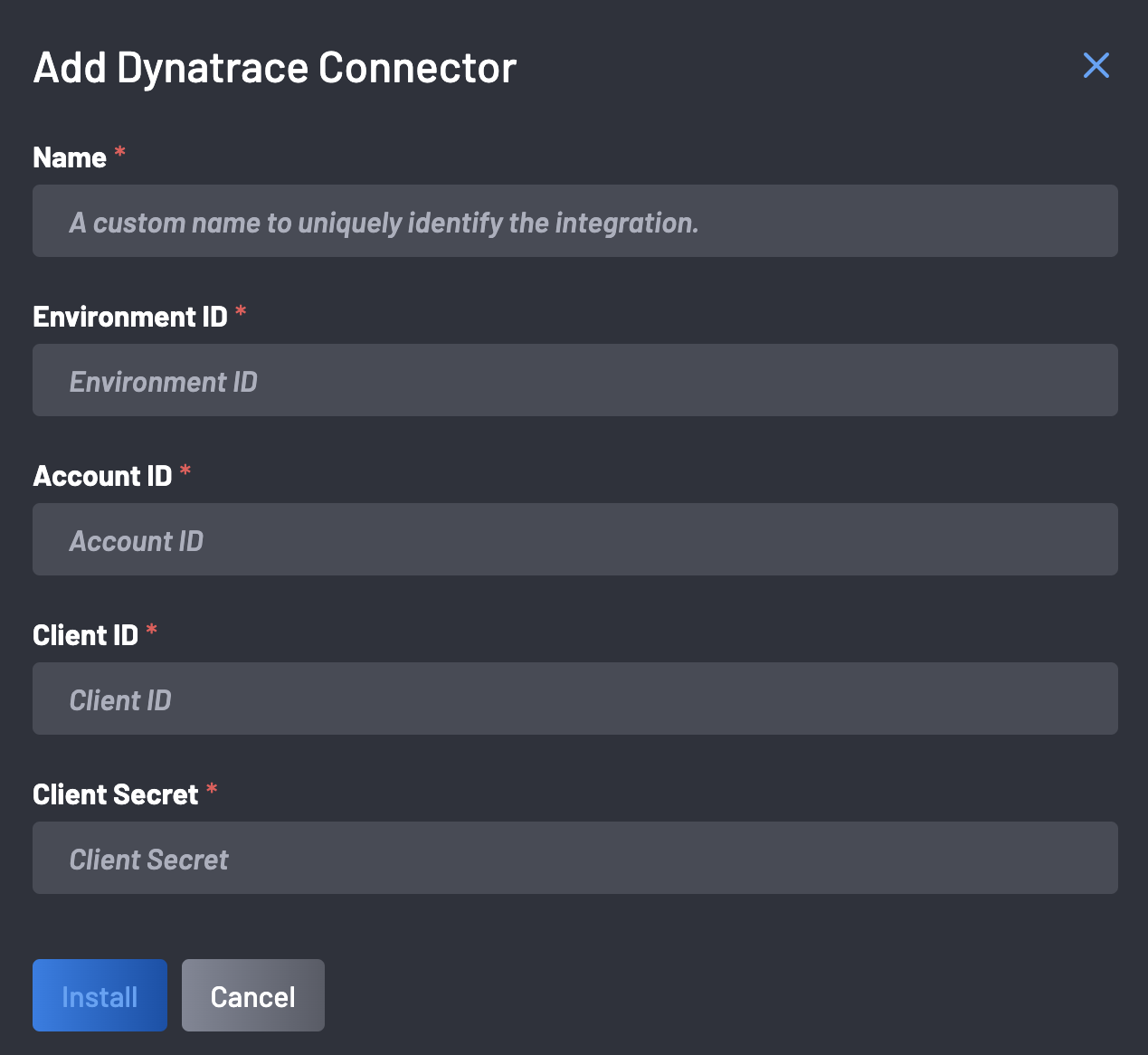
-
Input the necessary details for the integration, i.e., Name, Environment ID, Account ID, Client ID, Client Secret, and click the Install button.
-
The setup should finalize for users with the correct privileges.
Step 2: Validate the Integration¶
- Verify that BoostSecurity is receiving runtime data from Dynatrace.
- Check security findings in BoostSecurity, such as Kubernetes cluster details and vulnerability prioritization.
Key Features¶
Code-to-Cloud Mapping¶
- Dynatrace detects vulnerabilities (e.g., CVEs in containers, OWASP Top 10 risks like SQL injection) but lacks development context.
- BoostSecurity links runtime vulnerabilities to their source code, identifying the originating repository, responsible developer, and related security issues.
- This connection accelerates remediation and enhances vulnerability prioritization.
Enriched Security Context¶
BoostSecurity ingests runtime data from Dynatrace, adding: - Kubernetes cluster and service details. - Internet and data reachability of affected containers. - Whether a CVE is risky due to module loading or vulnerable function execution.
Improved Risk Prioritization¶
- BoostSecurity uses Dynatrace insights to surface high-risk vulnerabilities. Examples include:
- High EPSS CVEs that are internet-accessible.
- SQL injection vulnerabilities affecting PII, where the database is reachable from the container.
Context-Aware Security Policies¶
BoostSecurity’s policy engine allows fine-grained security controls based on runtime data. Policies can now:
- Fail builds if the commit introduces a vulnerability that is exploitable in the wild, loadable into memory, and the container is internet-accessible.
- Insert PR comments only when a CVE has a fix and is actively exploited.