Configuring Entra ID and Azure DevOps Integration with BoostSecurity¶
This guide provides detailed instructions for configuring Microsoft Entra ID and Azure DevOps (ADO) to integrate with BoostSecurity. The configuration establishes a secure connection using an Entra ID app registration, service principal, and associated permissions. By following the steps outlined in this guide, you will:
- Create and configure an Entra ID application registration.
- Assign the required Azure DevOps API permissions.
- Generate and manage client secrets.
- Connect Azure DevOps to your Entra ID tenant.
- Configure BoostSecurity to integrate with your ADO environment.
- Enable webhook installation and Zero Touch Provisioning (ZTP).
This process ensures BoostSecurity can securely interact with your Azure DevOps organization while adhering to best practices for access control and automation.
Entra ID Configuration¶
-
In the Azure Portal, navigate to Entra ID → Manage → App Registrations , and create a new app registration.
-
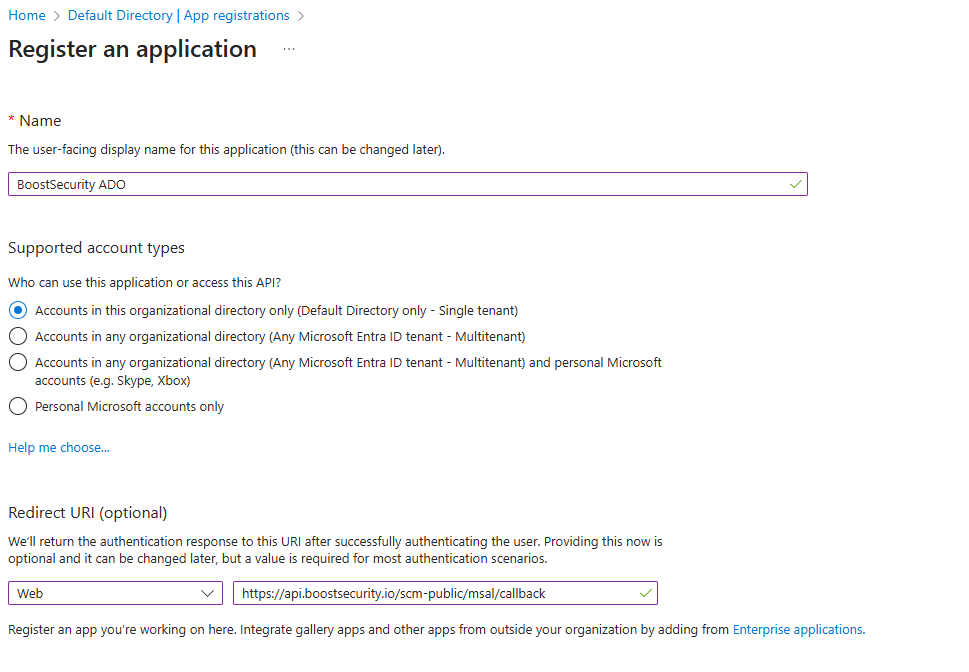
Assign a descriptive name and configure the Web Redirect URL to:
https://api.boostsecurity.io/scm-public/msal/callback -
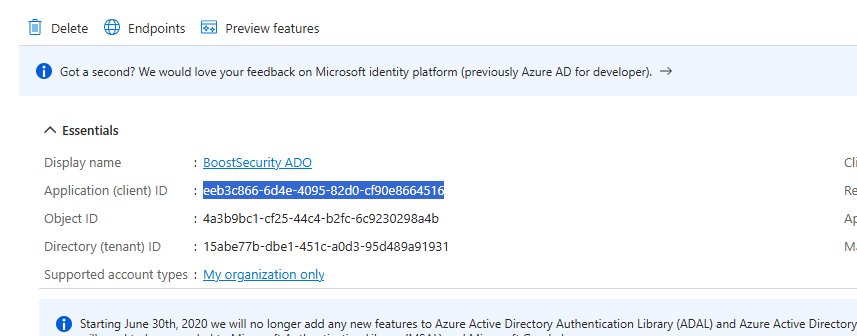
After creating the registration, open the Overview page and copy the Client ID. You will need this value in later steps.
-
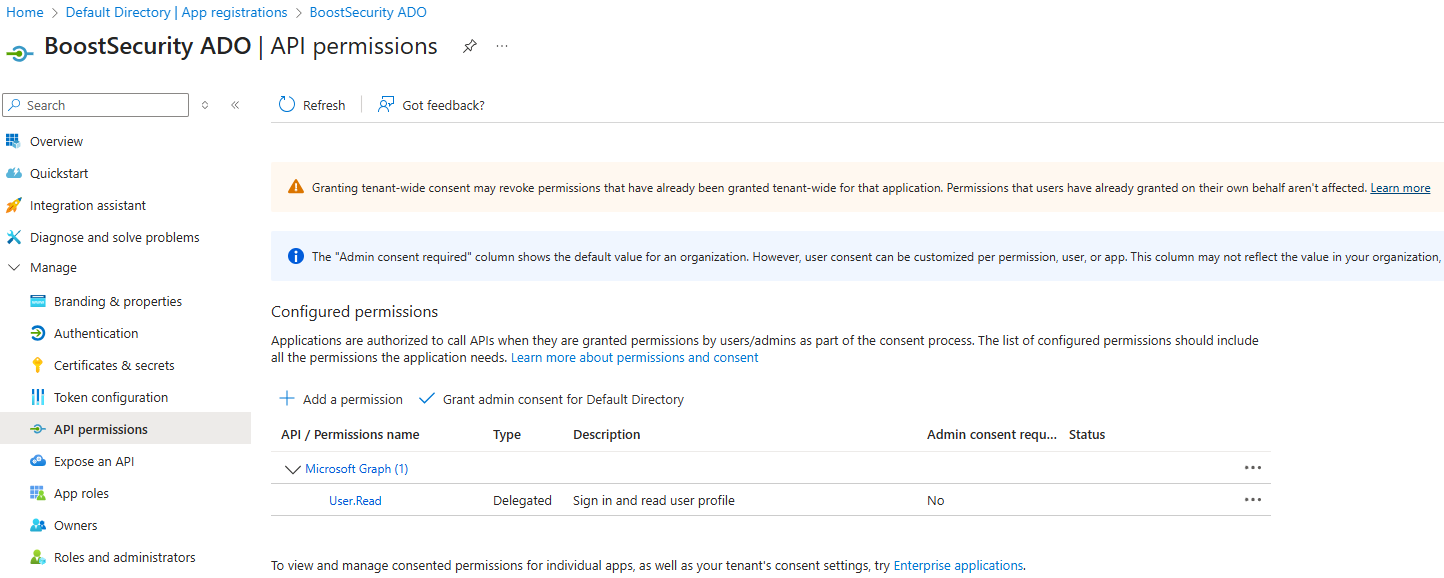
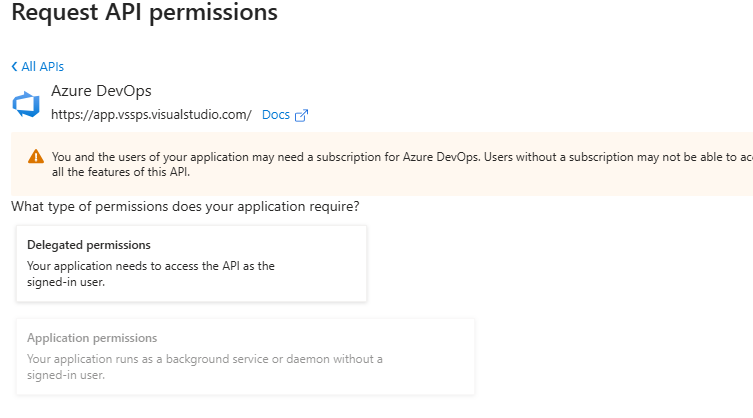
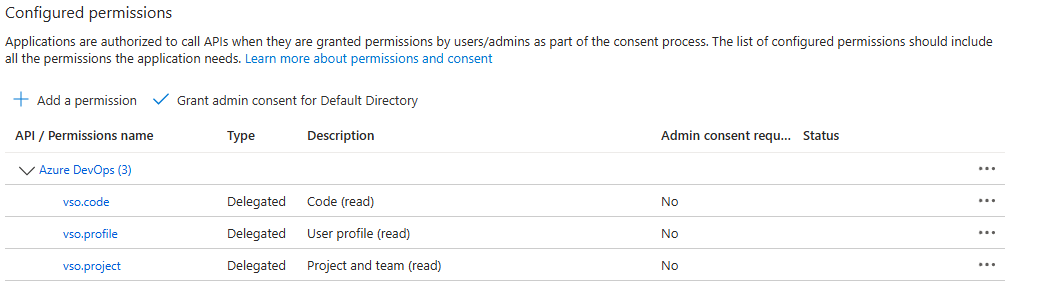
Configure API permissions:
-
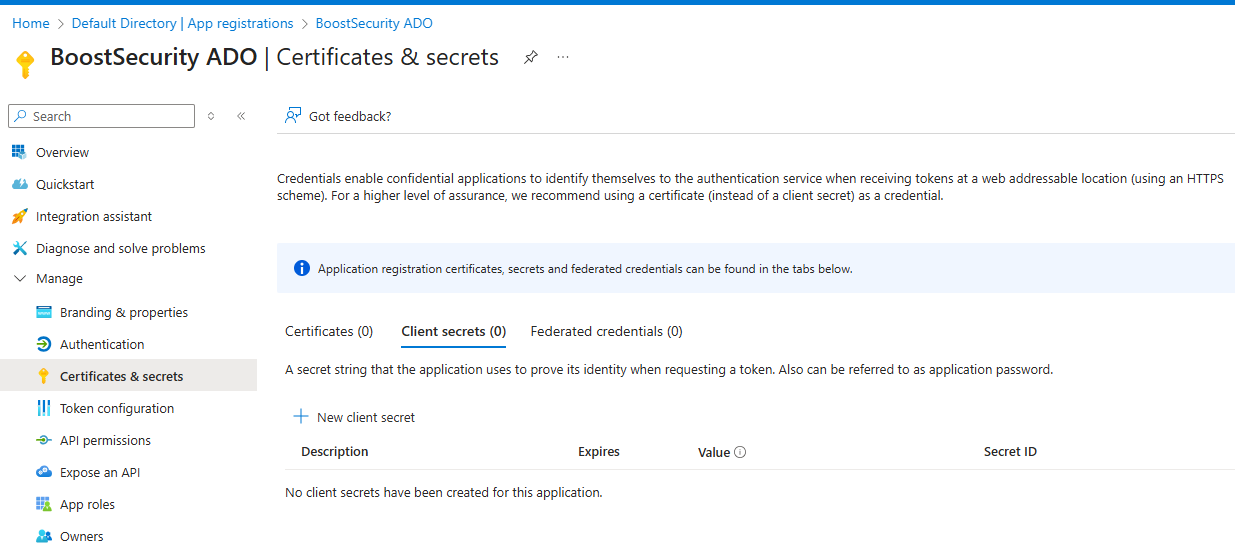
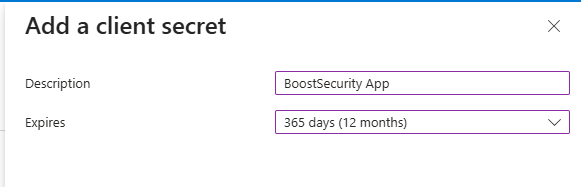
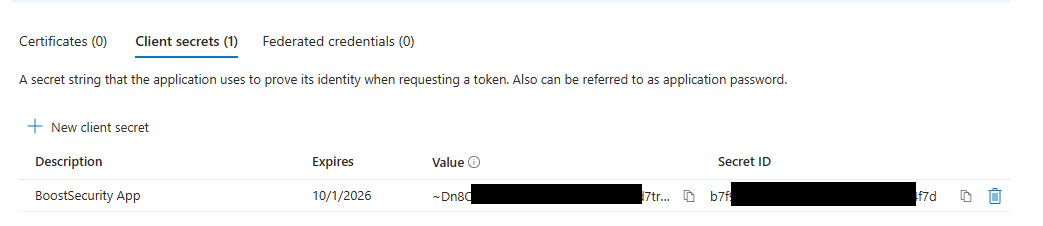
Generate a client secret:
Azure DevOps Configuration¶
-
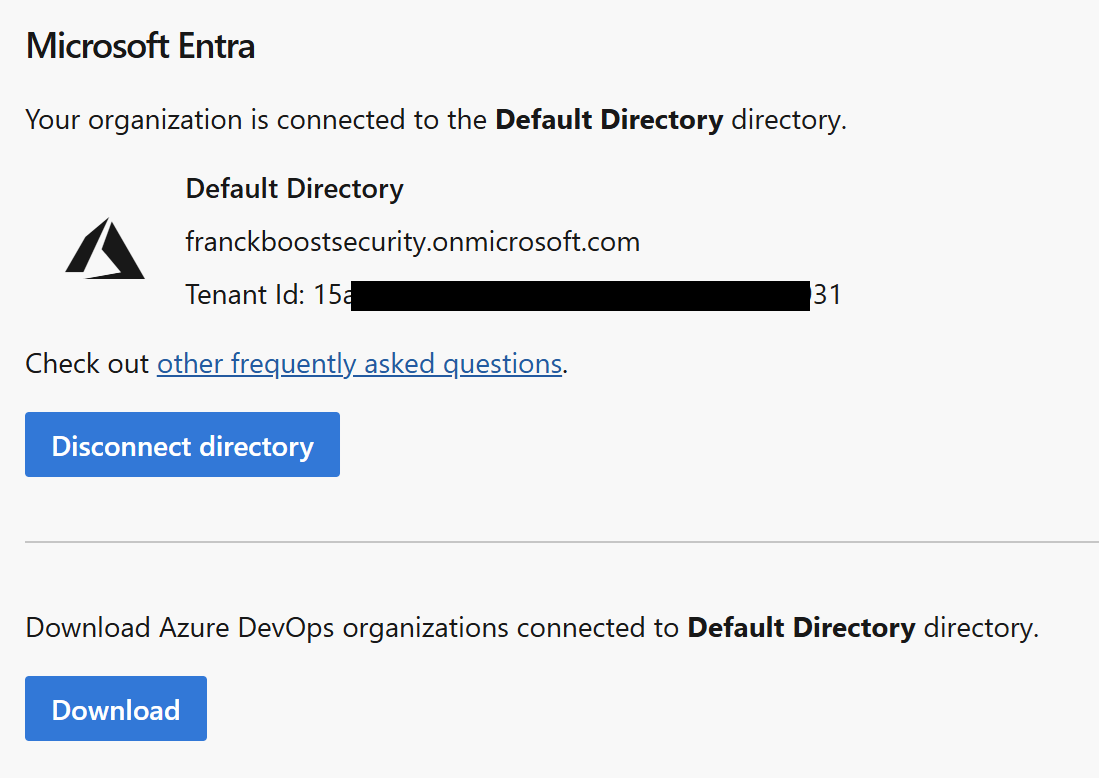
In your Azure DevOps organization settings, confirm that the organization is connected to your Entra ID tenant:
https://dev.azure.com/{ORGANIZATION}/_settings/organizationAad -
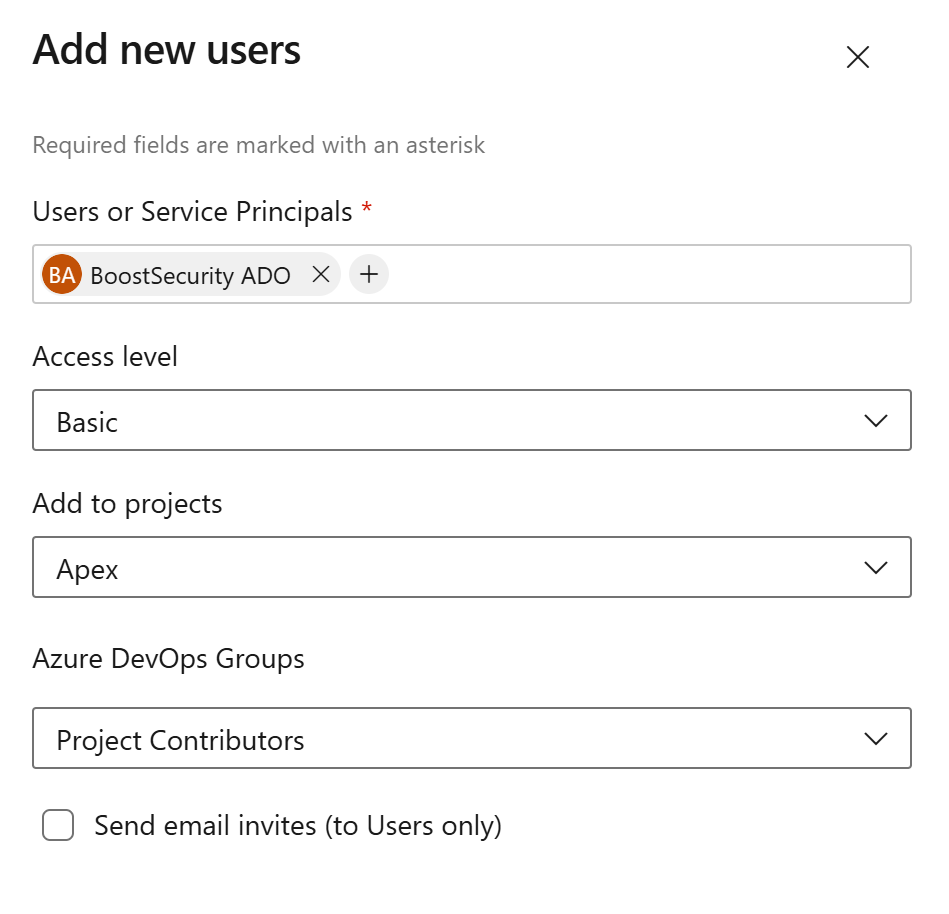
Add the Entra ID service principal as a user:
- Go to
https://dev.azure.com/{ORGANIZATION}/_settings/users. - Search for the service principal by name.
- Assign the service principal the role of Project Contributor with Basic access level.
- To ensure seamless integration, it is recommended to assign access to all projects.
- Go to
BoostSecurity ADO Account Integration¶
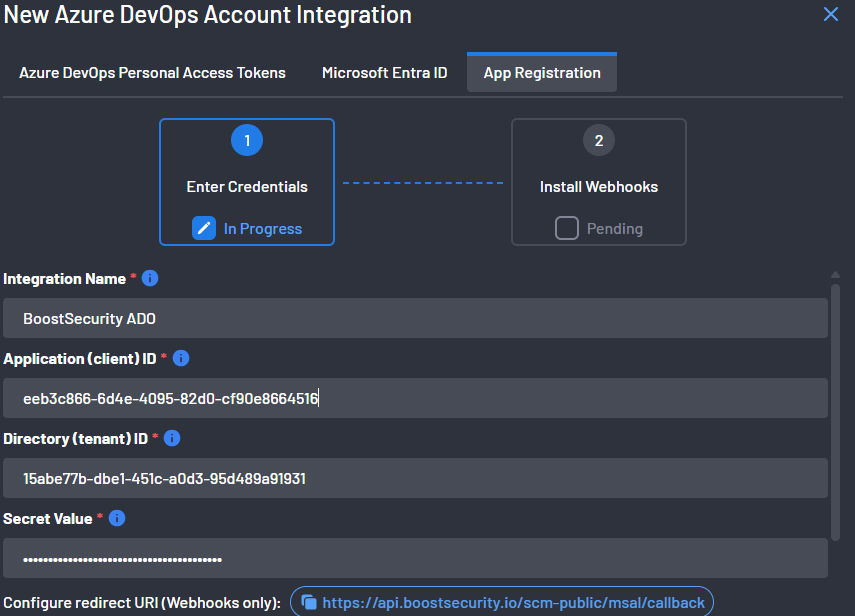
- In the BoostSecurity console, navigate to Settings → Integrations → ADO Account Integration , and select the App Registration tab.
-
Provide the following details:
- Integration name
- Client ID from the Entra ID app registration
- Tenant ID (available at: Active Directory)
- Client Secret generated during the Entra ID configuration
-
Install the webhook:
- BoostSecurity will request temporary authorization to act on your behalf in ADO.
- Approve the authorization request when prompted.
-
Enable Zero Touch Provisioning (ZTP):
- Install the BoostSecurity ADO application from the Visual Studio Marketplace: BoostSecurity Scan App
- Once installed, enable ZTP to complete the configuration.