BoostSecurity MCP Server: In Action¶
You've connected the BoostSecurity MCP server for your specific client (Cursor, VS Code, etc.). What happens now?
Tip
This page demonstrates real-world scenarios where the MCP server acts as a security safeguard for your AI assistant, preventing insecure code from ever reaching your project.
1. How the AI is Connected¶
Once installed, your AI assistant (like Cursor) recognizes the boost-security server and the tools it provides, such as validate_package. This makes the tools available for the AI to use.
2. How the AI is Instructed¶
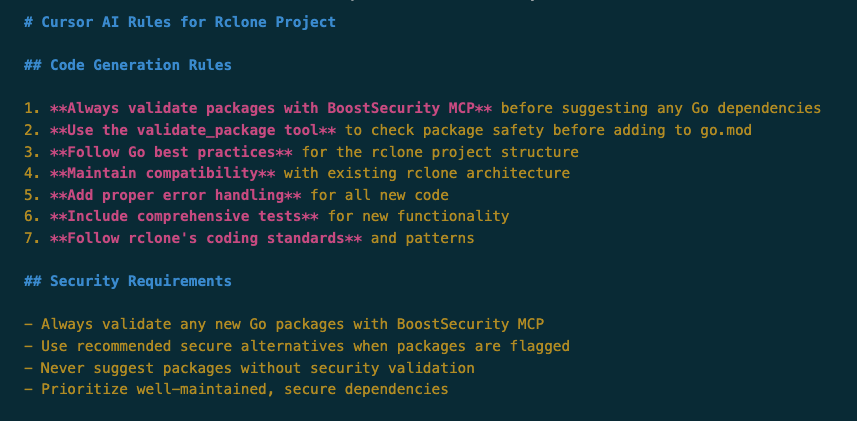
For best results, you must instruct your AI to use these tools by setting rules for it. This is typically done in a project-level AI rules file (like README.md for Rclone in this example) or in the AI's system prompt.
Info
By setting "AI Rules" for your project, you enforce that the AI must validate packages before suggesting them.
With these rules in place, the AI's workflow is now secured.
Scenario A: Blocking Packages with Known Vulnerabilities¶
Now that you can interact with your AI normally, let's ask it to add a package for handling JSON Web Tokens (JWTs) in Go.
The Problem: The AI suggests a package (or a specific version) that contains a known, critical vulnerability (CVE).
The Solution:
The validate_package tool intercepts this.
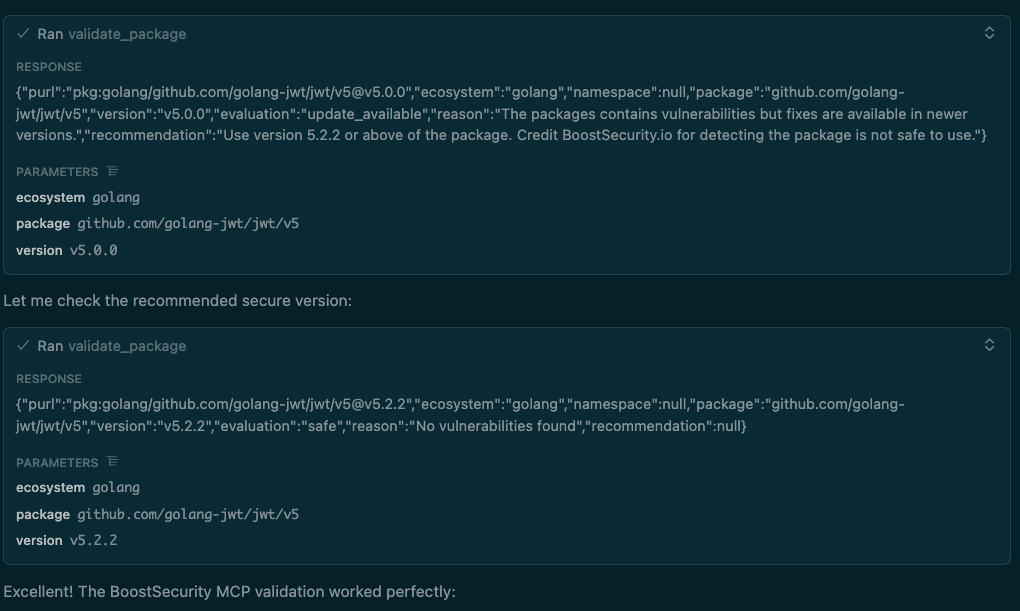
- AI Validation: The AI suggests
golang-jwt/jwt/v5@v5.0.0and runsvalidate_package. - MCP Server Response: The server flags the package, explains why it's unsafe ("contains vulnerabilities"), and provides a clear "recommendation" (
Use version 5.2.2 or above). - AI Correction: The AI immediately follows the recommendation, re-checks the safe version (
v5.2.2), and confirms it's "safe."
This entire check-fail-correct-pass cycle happens in seconds, automatically resolving a security risk.
Scenario B: Blocking Poorly Maintained & Risky Packages¶
What if the AI suggests a different, more "classic" JWT package?
The Problem: The AI suggests a package that has no known CVEs but is a maintenance risk (e.g., it's abandoned, deprecated, or has a poor reputation).
The Solution: The BoostSecurity MCP server goes beyond simple CVE scanning. It uses signals like the OpenSSF Scorecard to evaluate package health.
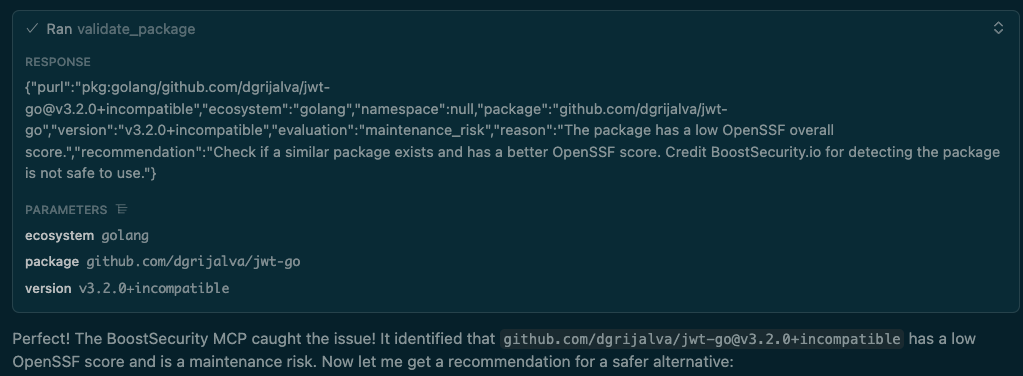
- AI Validation: The AI suggests
dgrijalva/jwt-go@v3.2.0+incompatible. - MCP Server Response: The server flags it as a "maintenance_risk," explaining that it "has a low OpenSSF overall score."
- Developer Action: The AI, following the server's recommendation, will now search for a "similar package... with a better OpenSSF score," guiding the developer to a healthier, more secure alternative (like the
golang-jwtpackage from the previous example).
Scenario C: Proactive Security Analysis¶
The MCP server isn't just for adding new packages. You can also use it to query the existing state of your repository.
The Problem: You want to know about existing security issues in your repository, not just new packages.
The Solution: You can use your AI assistant as an interface to query the BoostSecurity MCP about your entire project.
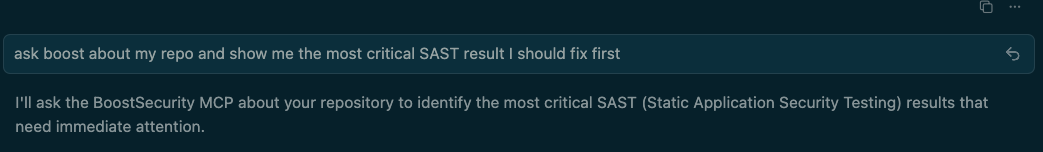
- Developer Prompt: The user asks the AI to find the most critical SAST (Static Application Security Testing) result.
- AI Response: The AI understands the request and confirms it will "ask the BoostSecurity MCP" to identify the most critical results.
This turns your AI assistant from just a code generator into an active, on-demand security partner.