Enable AI-Generated PR Comments for Security Remediation¶
BoostSecurity's AI integration enables AI-assisted remediation comments directly in your pull requests. By configuring the "Add a comment to the pull request" and "Generate AI Remediation" actions in your policy settings, you can use your AI provider (OpenAI, Bedrock, Gemini, or Anthropic) to generate actionable code suggestions. This keeps developers in their workflow while addressing security vulnerabilities.
Note
AI-assisted remediation is available for SAST, IaC, and Secrets findings only. SCA findings are excluded because BoostSecurity already provides clear, well-understood remediation paths for these vulnerabilities.
Key Benefits¶
- Automated PR Comments: Receive AI-generated suggestions and comments tailored to detected vulnerabilities.
- Contextual Assistance: Comments appear seamlessly in your pull requests across supported SCM platforms like GitHub, GitLab, Azure DevOps (ADO), and Bitbucket.
- Enhanced Developer Productivity: Enable developers to review and apply remediation advice directly in their PR environment.
- Customizable Feedback: Leverage the selected AI model to align comments with your team's coding standards and security needs.
Prerequisites¶
Before enabling AI-generated comments, ensure the following:
- AI Provider Integration: An AI provider (e.g., OpenAI, Bedrock, Gemini, and Anthropic) is configured with a valid API key, as outlined in the Integrating AI Providers for Assisted Remediation guide.
- Suitable AI Model: The chosen model must support text generation and code analysis (e.g.,
gpt-4,claude-sonnet,gemini-pro). Models designed for image or audio processing are incompatible and may result in errors.
Configuration Steps¶
Follow these steps to enable and customize AI-generated comments in your pull requests:
-
Navigate to the Policy page and select the policy where you want to enable AI comments or create a new policy.
-
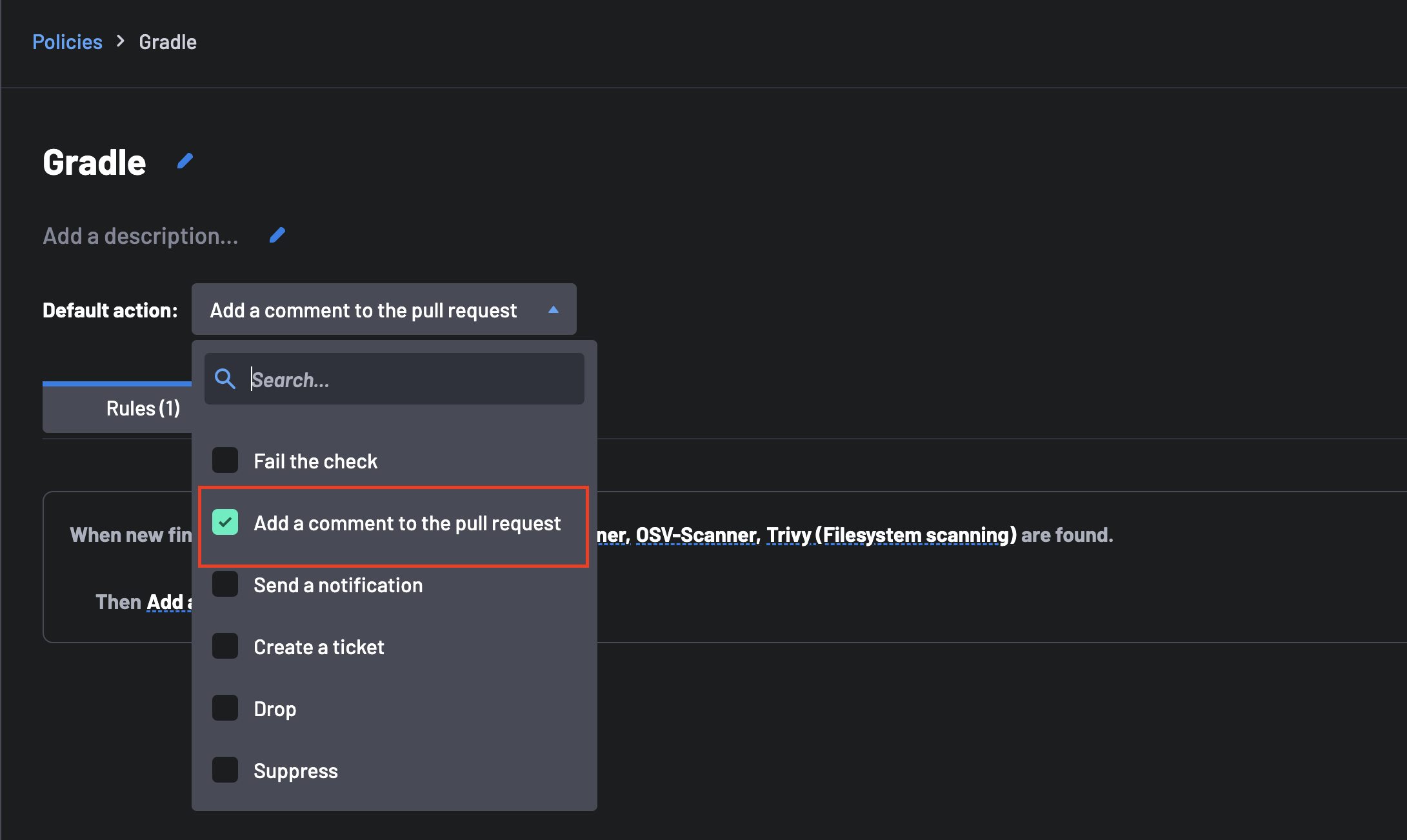
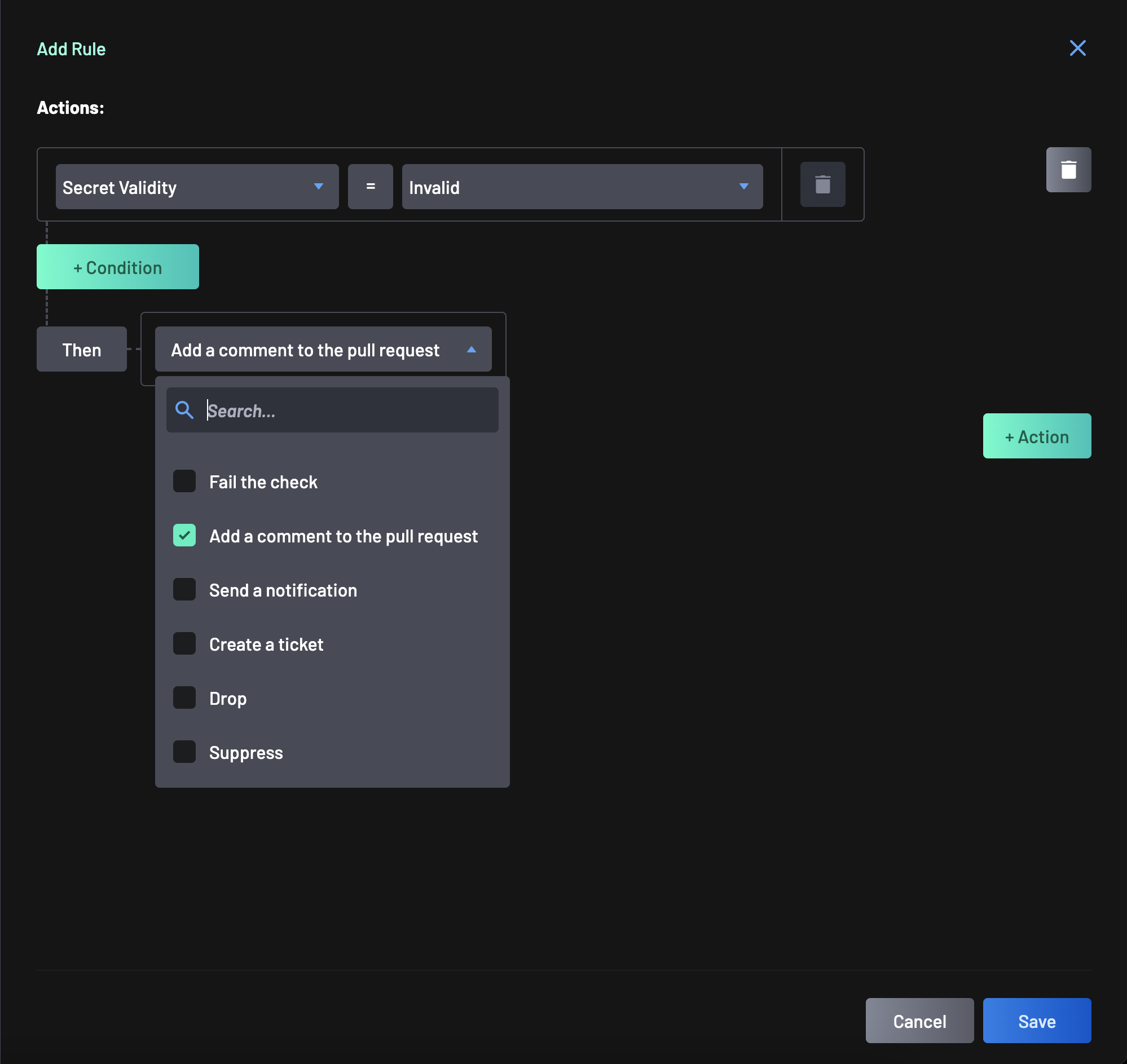
In the policy editor, configure AI-generated comments by selecting one of these options:
-
Set as Default Action: Locate the "Default action" dropdown and select "Add a comment to the pull request" and "Generate AI Remediation".
-
Create New Rule: Click the +Action button, define a trigger, and select the conditional response to the selected action be "Add a comment to the pull request" and "Generate AI Remediation".
-
-
Click Save to apply your configuration. Next, assign the policy to your resources to enable AI-assisted comments. BoostSecurity will then automatically generate AI-remediation comments for security findings detected in your pull requests.
What AI-Generated Comments Look Like¶
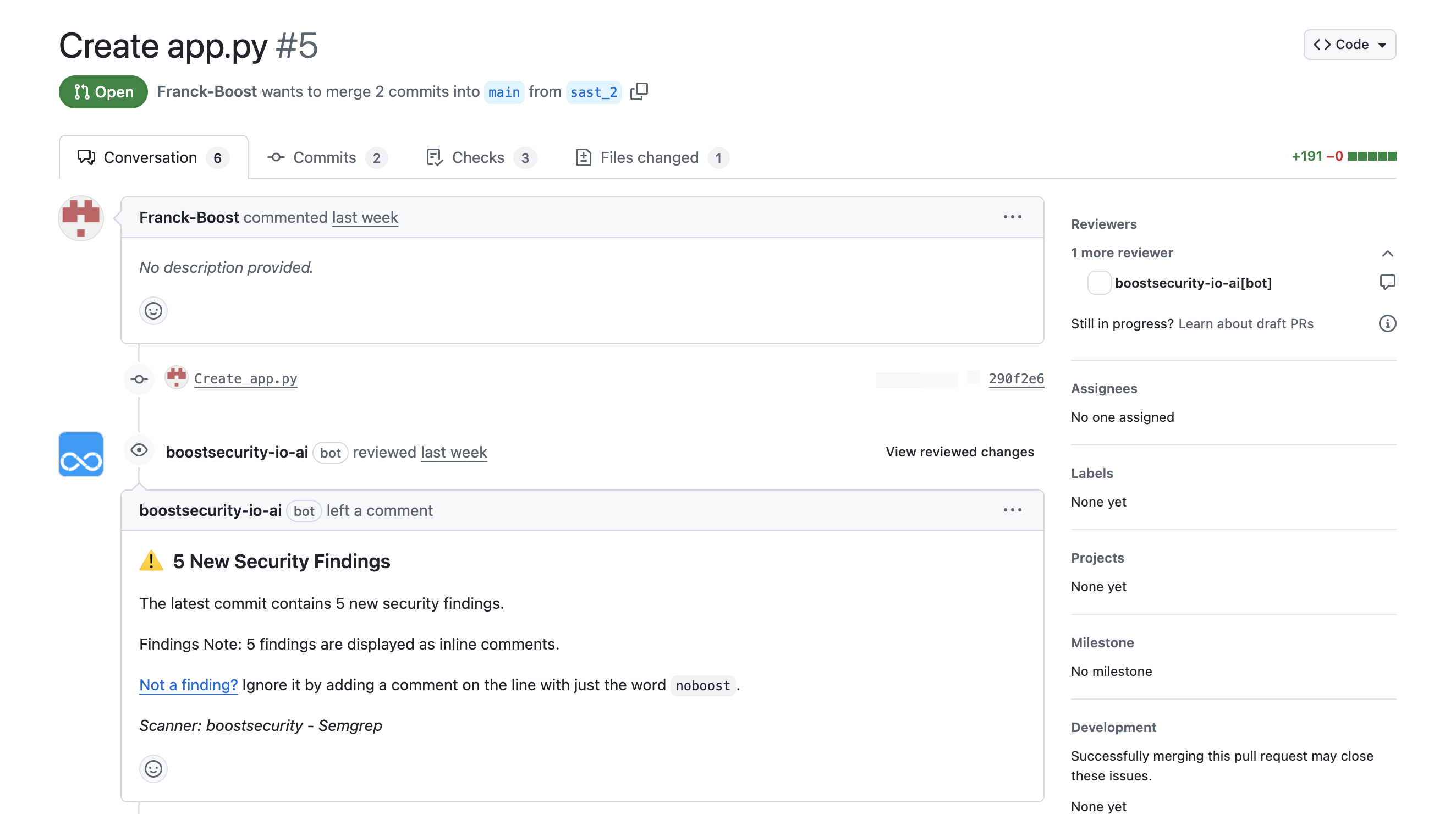
When AI remediation is enabled, comments appear as follows in your pull request:
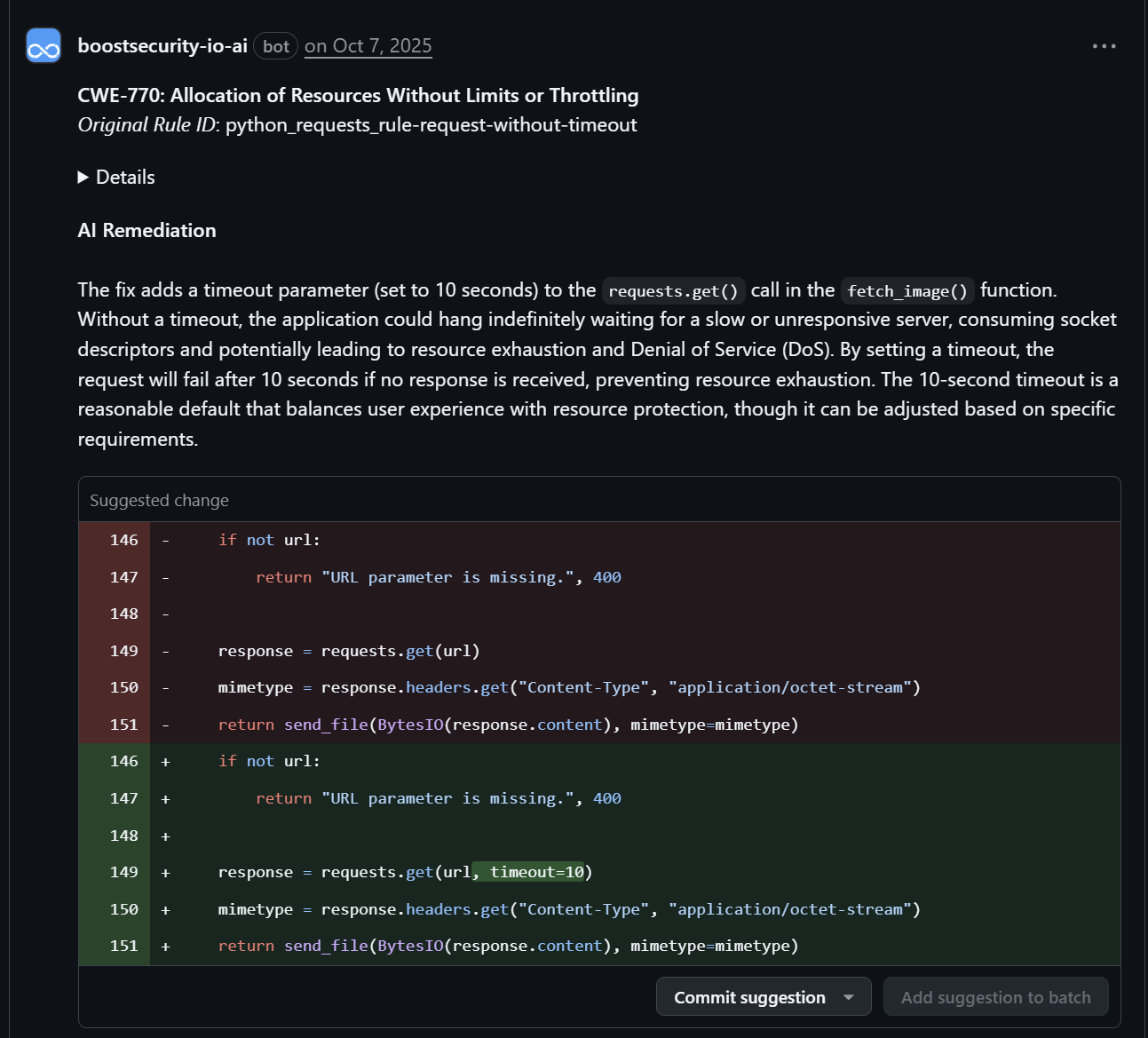
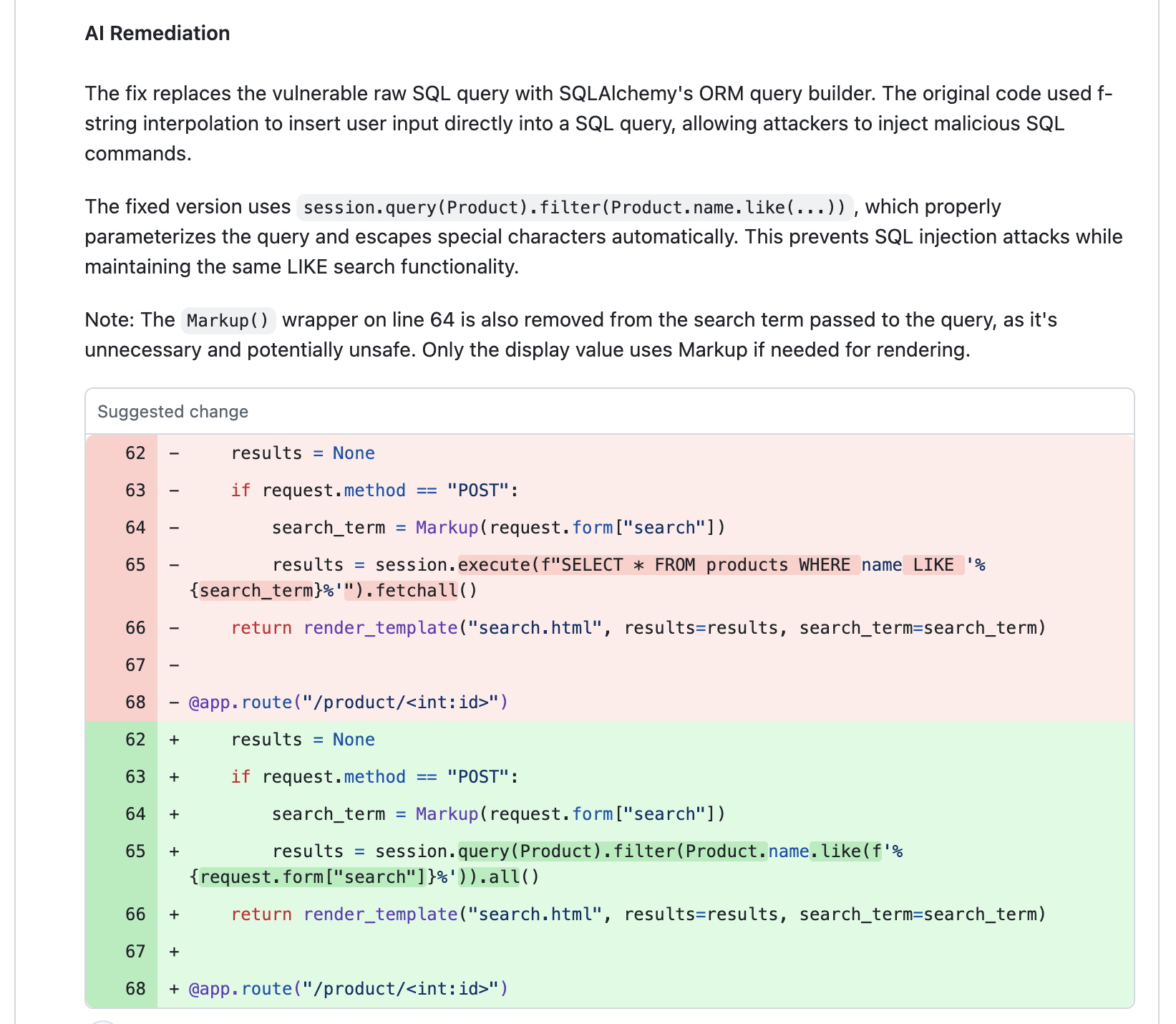
Example AI Security Finding¶
Example AI Remediation¶
- Comments are posted directly in the PR thread, linking to the affected code line.
- Suggestions include code snippets, explanations, and best practices based on the selected AI model.
Managing AI-Generated PR Comments¶
- Edit Policy: Adjust or switch AI models via the Integrations > AI page if comment quality needs improvement.
- Disable Comments: Unselect the "Add a comment to the pull request" option to stop AI-generated comments while keeping other remediation features active.
Troubleshooting¶
| Issue | Possible Cause | Solution |
|---|---|---|
| No Comments Appear in PRs | "Add a comment to the pull request" is disabled, the policy is not configured correctly, or AI provider misconfigured. | Verify the policy settings and check AI provider setup in Integrations. |
| Irrelevant or Poor Comments | Model unsuitable for code analysis. | Switch to a text/code-oriented model (e.g., gpt-4 over gpt-3.5). |
| Comments Missing Context | Insufficient PR data or model limitations. | Ensure PR includes full context; test with a more advanced model. |
| No auto-remediation | There's no SAST, Secrets, or IaC findings in the PR | auto-remediation only triggers for SAST, Secrets, or IaC vulnerabilities. |